Steering Clear of Fake VPN Services: A DIY DRS Guide to Threat Discovery
Distributing fake virtual private network (VPN) services is no longer a novel cybercrime concept. They have, in fact, likely been around since the service’s usage gained ubiquity in the 2000s.
VPN service usage is only bound to become increasingly popular as more privacy issues and data breaches emerge. Unfortunately, that could also lead to more fake VPN service scams over time.
In this edition of our DIY investigation guide, we will demonstrate how companies and their security teams can detect potential VPN service scam vehicles in the DNS using the Domain Research Suite (DRS) search and monitoring tools.
Process #1: Looking for Potential Fake VPN Scam Vehicles
Threat actors were recently seen distributing OpcJacker malware in the guise of free VPN services, which, of course, turned out to be fake. Instead of protecting their privacy and data, therefore, the victims ended up with data stealer infections.
Step #1: Searching for a Specific Legitimate VPN Service Provider’s Copycats
Since the OpcJacker investigation didn’t specify a target legitimate VPN service, we opted to perform a DIY DRS investigation on today’s top VPN app—ExpressVPN.
To uncover potential ExpressVPN copycats that could have already figured in or may be waiting to get weaponized for malware campaigns, follow these steps.
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only.
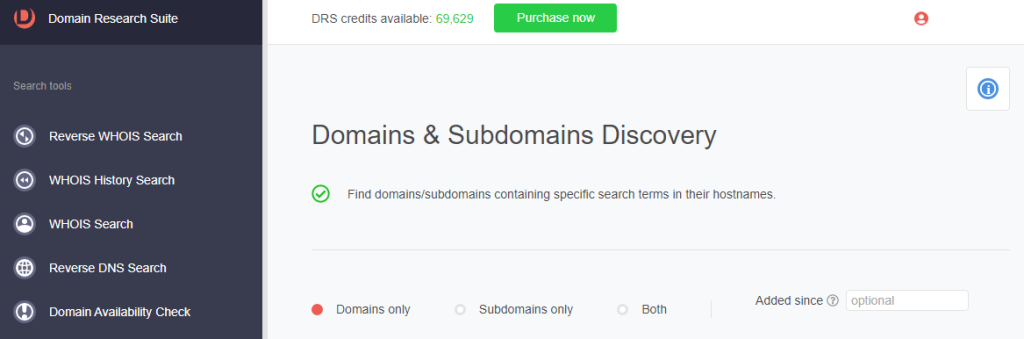
2. Type expressvpn into the search field.
3. Set the string placement parameter and click Search. For this demonstration, we limited our search to domains that Start with expressvpn.
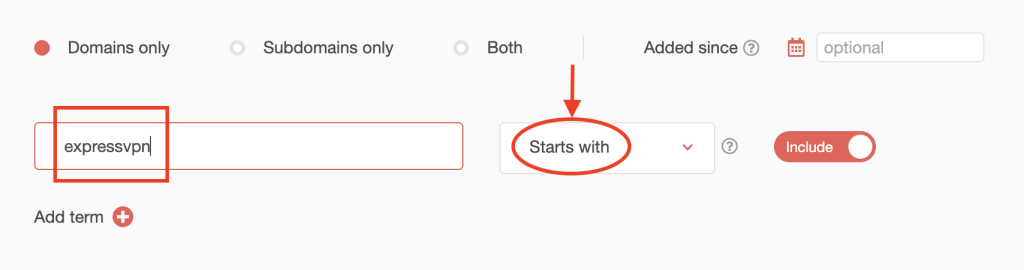
We found 375 domains that start with expressvpn.
4. Scroll up to go back to the top of the page. Select Subdomains only.
5. Type expressvpn into the search box to retrieve the subdomains containing the string.
6. Set the string placement parameter and click Search. For this demonstration, we limited our search to subdomains that Start with expressvpn.
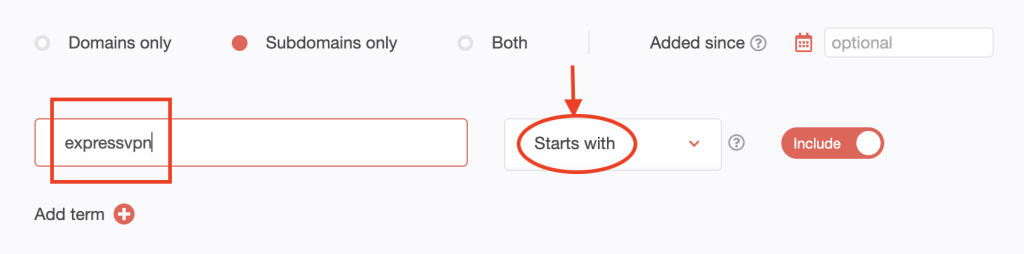
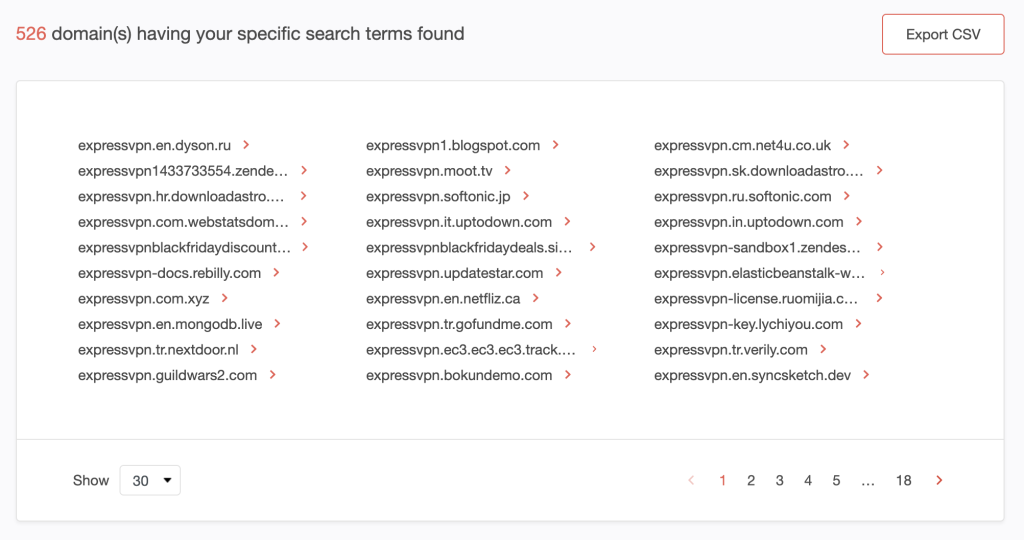
We found 526 subdomains that start with the string expressvpn.
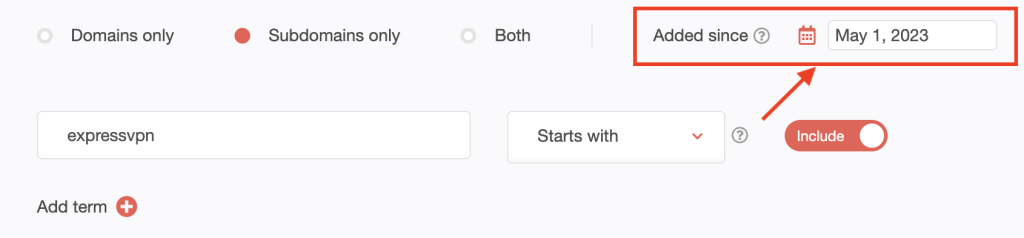
7. [PRO TIP] Make your domain and subdomain searches time-bound by setting the Added since parameter.
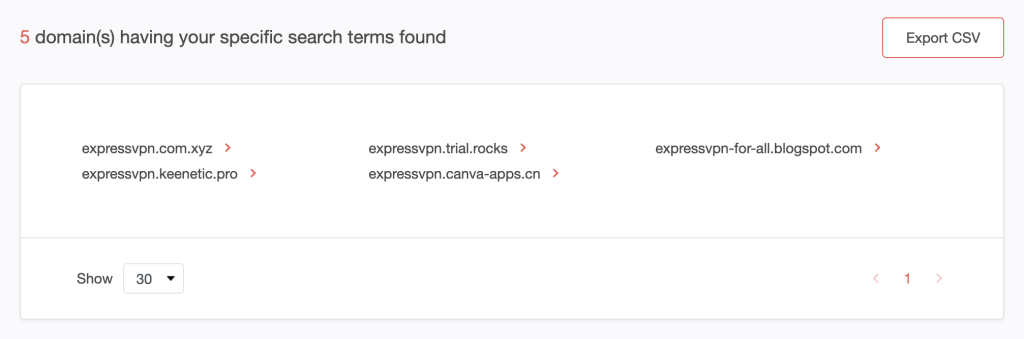
We found five subdomains that start with expressvpn added since May 1, 2023.
Step #2: Looking for Potential Legitimate VPN Service Cybersquatters
We all know by now that ExpressVPN isn’t the sole service provider in the market that cybercriminals can abuse. Finding domains and subdomains that can serve as potential fake VPN scam vehicles is also possible with DRS. How? Follow these steps.
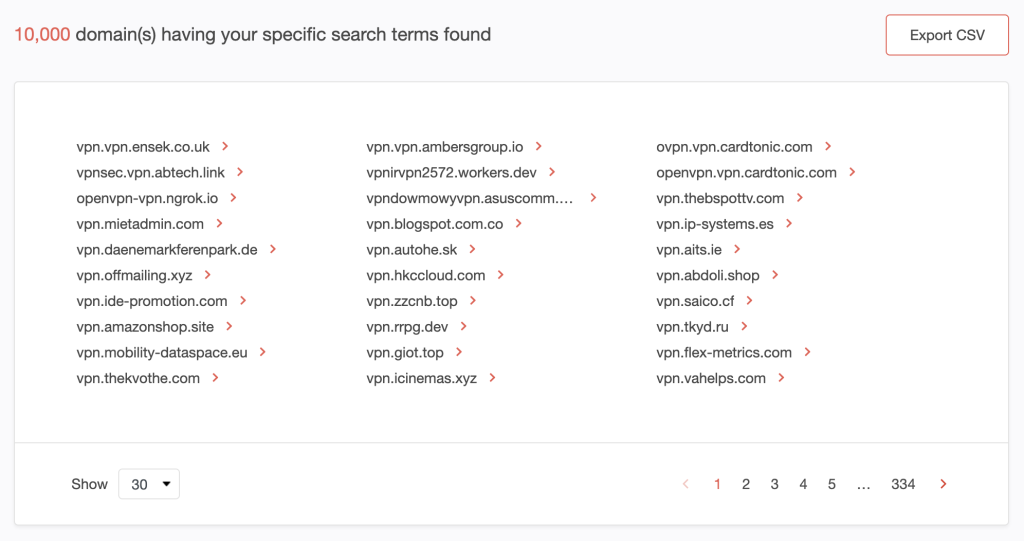
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only. Type vpn into the search field. Set the string placement parameter and click Search. For this demonstration, we used Contains.
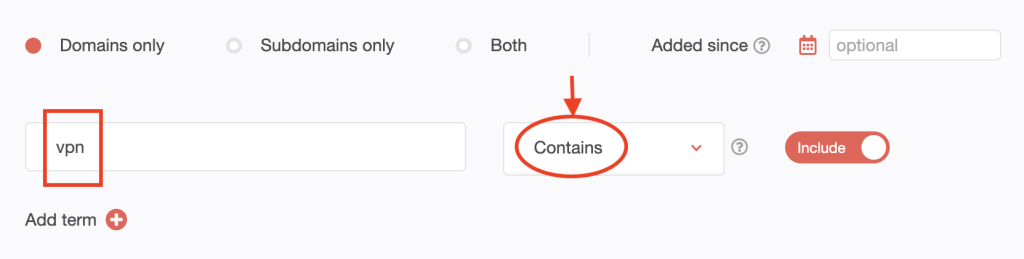
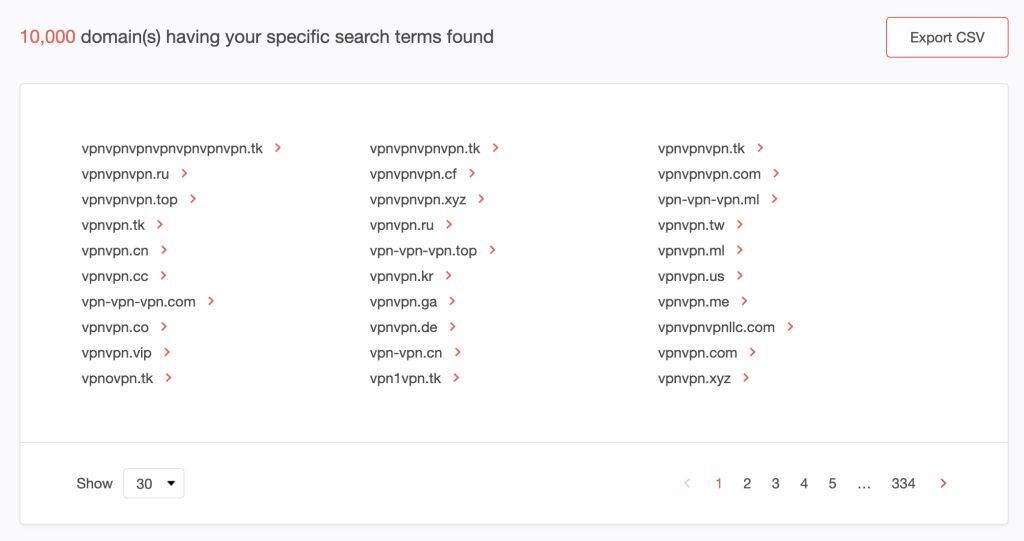
We found at least 10,000 domains that contain vpn. Note that the DRS search tool only provides a maximum number of 10,000 results.
2. Scroll up to go back to the top of the page. Select Subdomains only. Type vpn into the search box to retrieve the subdomains containing the string. Set the string placement parameter and click Search. For this demonstration, we used Contains.
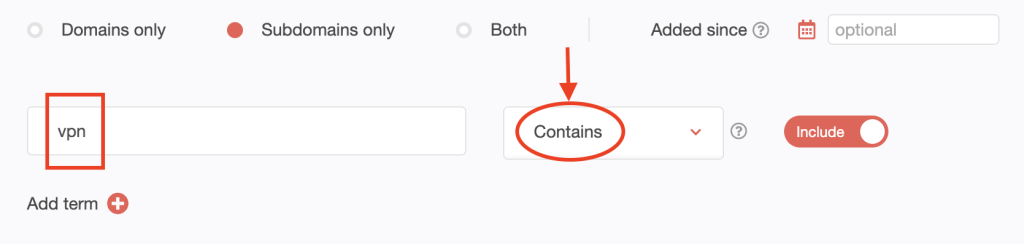
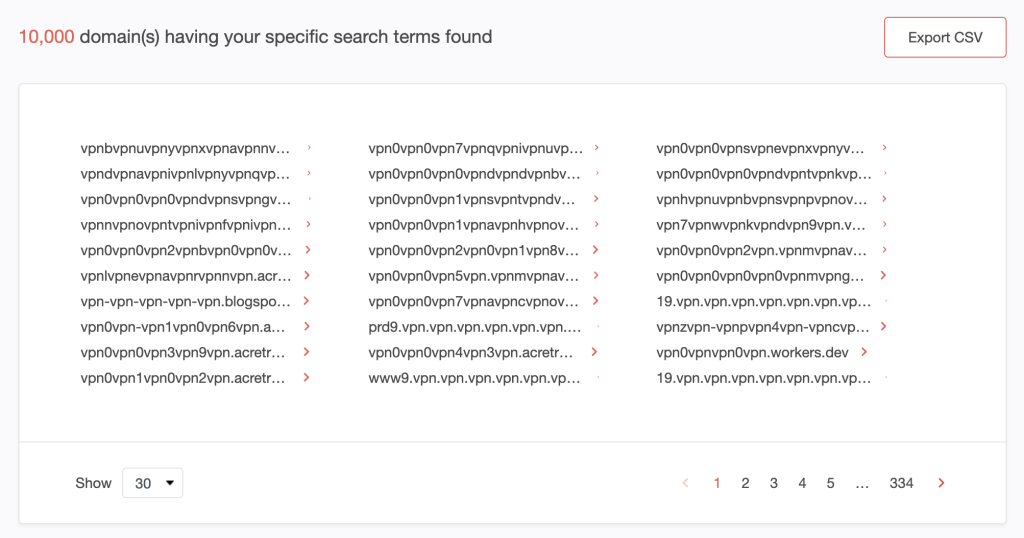
We found at least 10,000 subdomains that contains vpn.
3. [PRO TIP] Make your domain and subdomain searches time-bound by setting the Added since parameter.
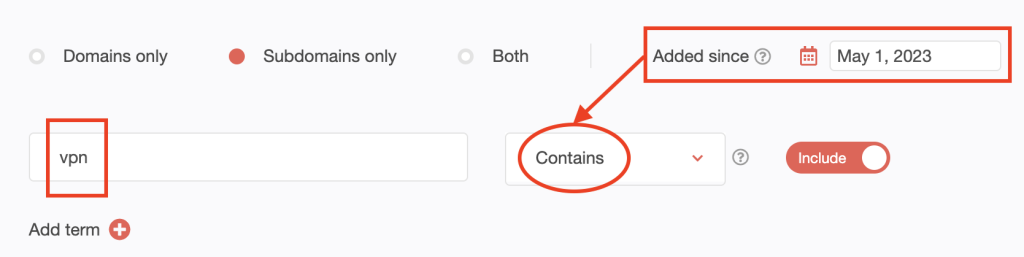
We found at least 10,000 subdomains that contain vpn added since May 1, 2023.
Process #2: Investigating Potential Copycats of a Legitimate VPN Service Provider
Let’s say you’ve been tasked to determine which of the domains and subdomains containing expressvpn could serve as fake VPN scam vectors. DRS can help you find out which of the domains and subdomains are actually owned by ExpressVPN. Follow these steps.
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only. Then type expressvpn into the search field. Set the string placement parameter and click Search. For this demonstration, we limited our search to domains that Start with expressvpn.
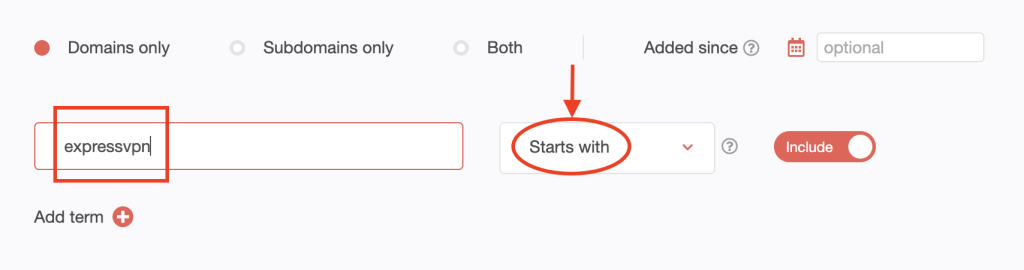
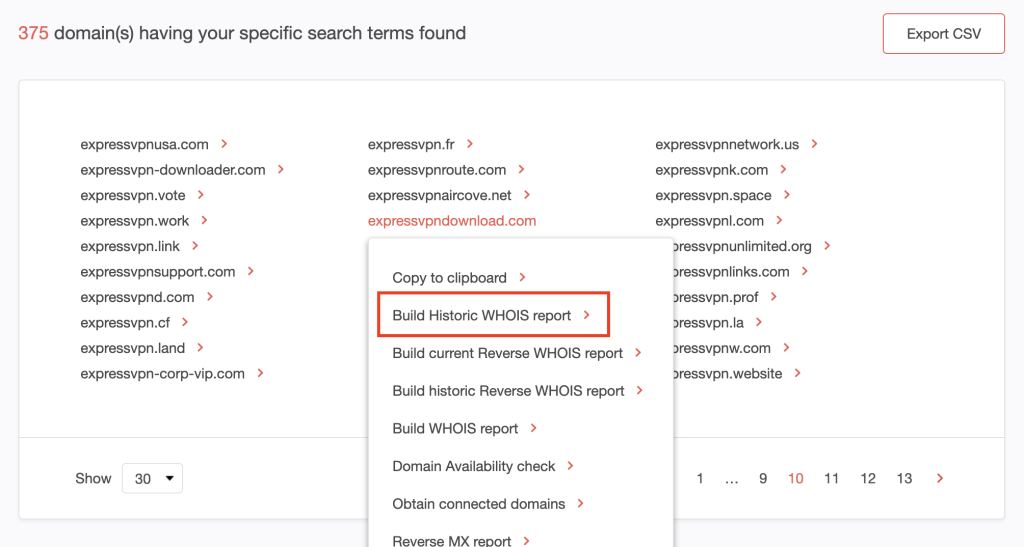
We found 375 domains that start with expressvpn.
--- MISSING IMAGE ---
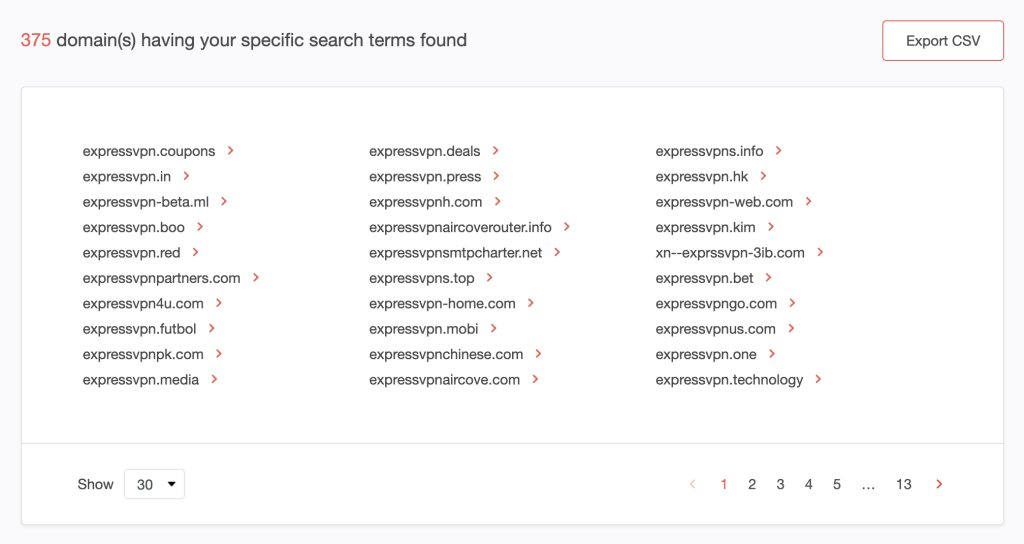
2. Zoom in on the domain expressvpndownload.com, as it looks like something cybercriminals would use in a fake VPN scam. Click the domain name and choose Build Historic WHOIS report.
3. Check the following details:
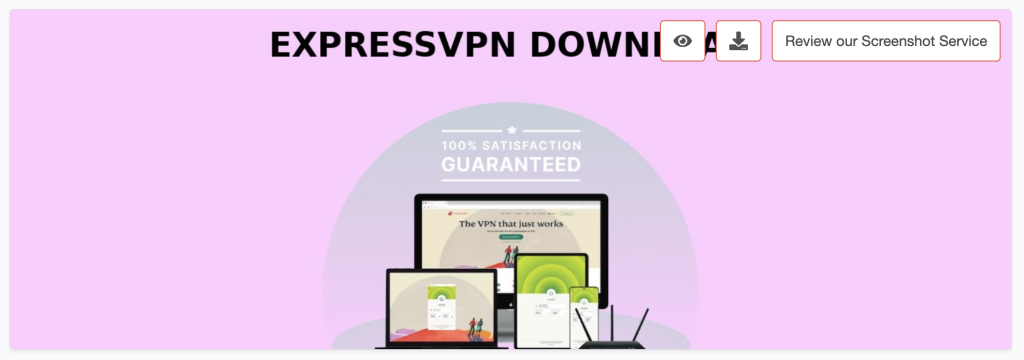
a. Website screenshot
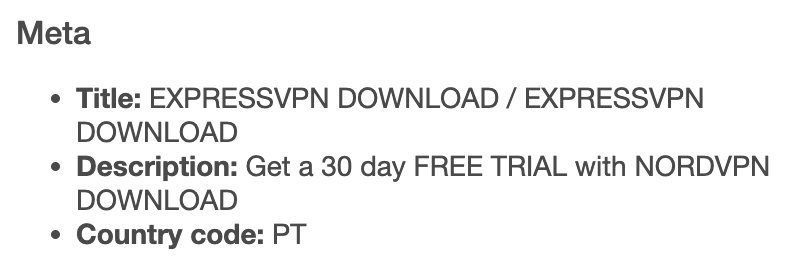
b. Metadata
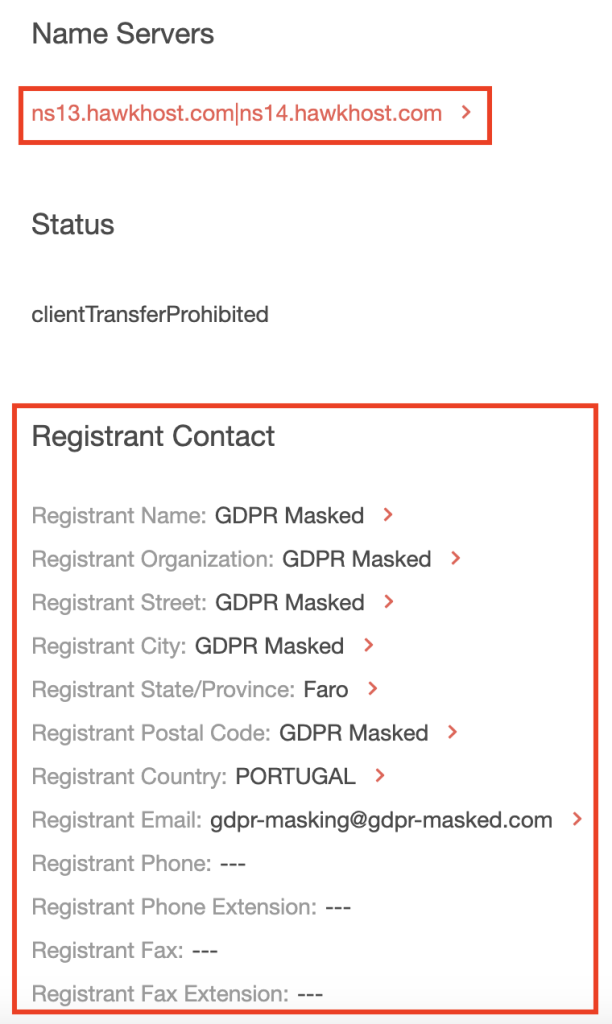
c. Name servers and registrant contact details
4. Go to WHOIS Search to retrieve the current WHOIS details of the company that is potentially being impersonated. Type ExpressVPN’s official domain name expressvpn.com into the search input field. Click Search.
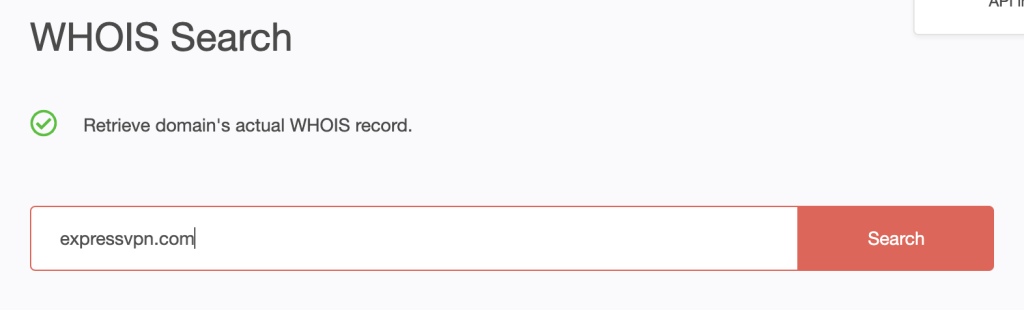
5. Compare the official details with those of the domain—expressvpndownload.com—from step #2 and note the differences.
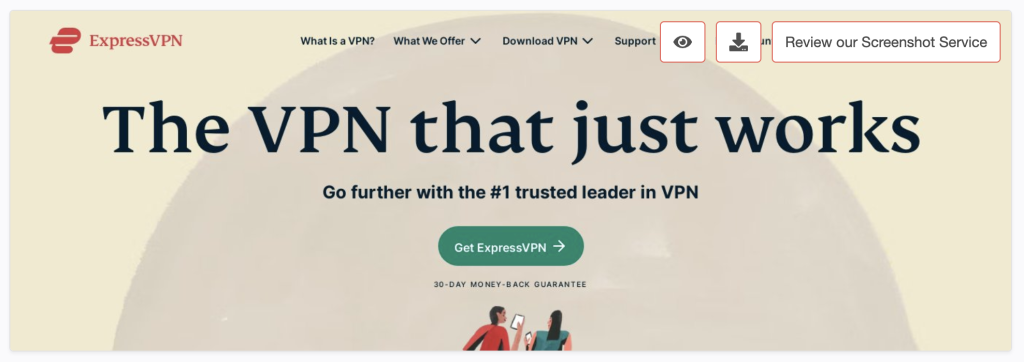
a. Website screenshot: The page hosted on expressvpndownload.com doesn’t look anything like the official ExpressVPN website shown below.
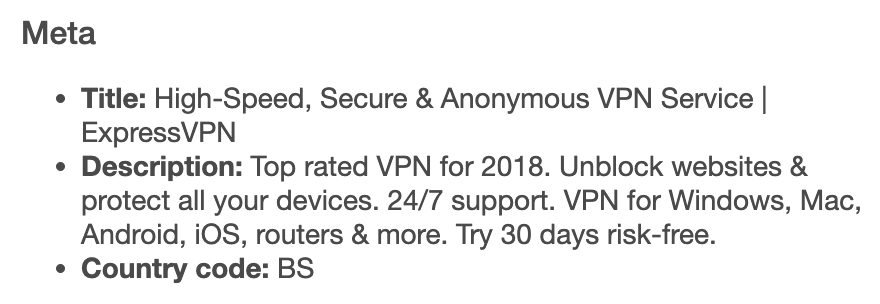
b. Metadata: While both domains’ metadata are available, they vastly differed in terms of title, description, and even country code.
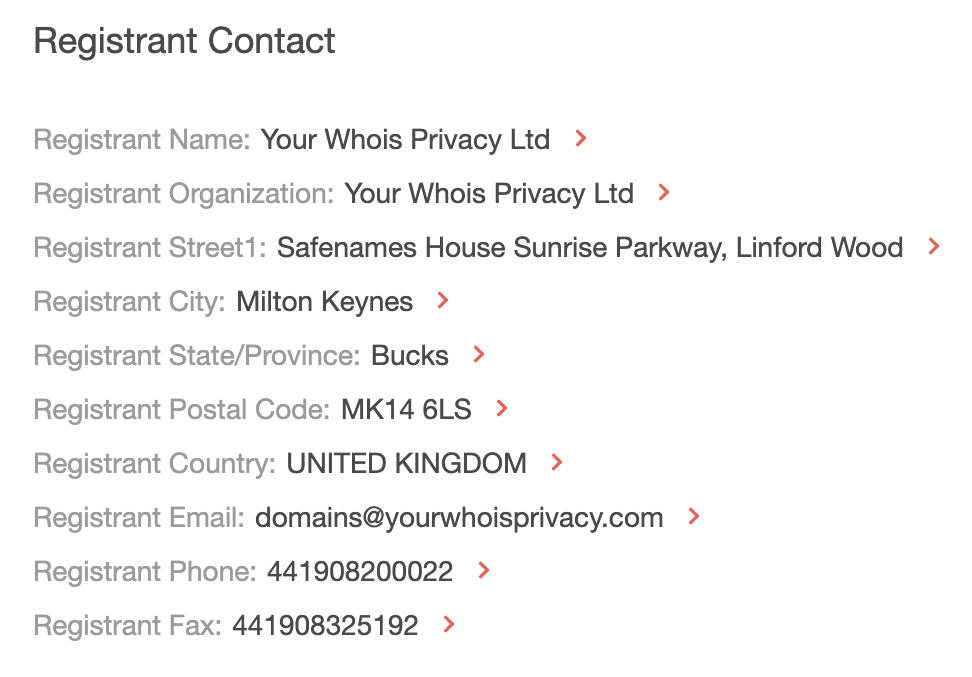
c. Name servers and registrant contact details: ExpressVPN uses name servers provided by Amazon Web Services (AWS) while the potential cybersquatter uses one provided by Hawk Host. Also, while both domains had privacy-protected registrant contact data, they didn’t use the same service provider.
Process #3: Monitoring the DNS for Potential VPN Scam Hosts
As an additional precautionary measure, you can also track the registration of domain names that could be riding on your brand’s or service provider’s popularity. To do that, follow the steps below.
1. Go to Brand Monitor.
2. Type the company name, ExpressVPN in this case, into the input field and click Add to monitoring.
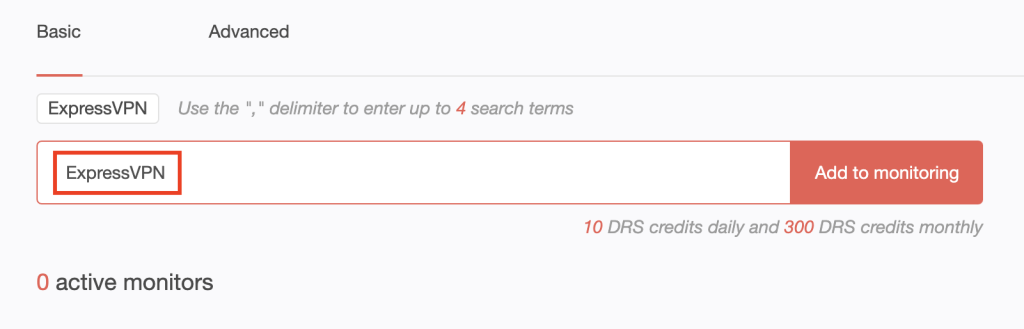
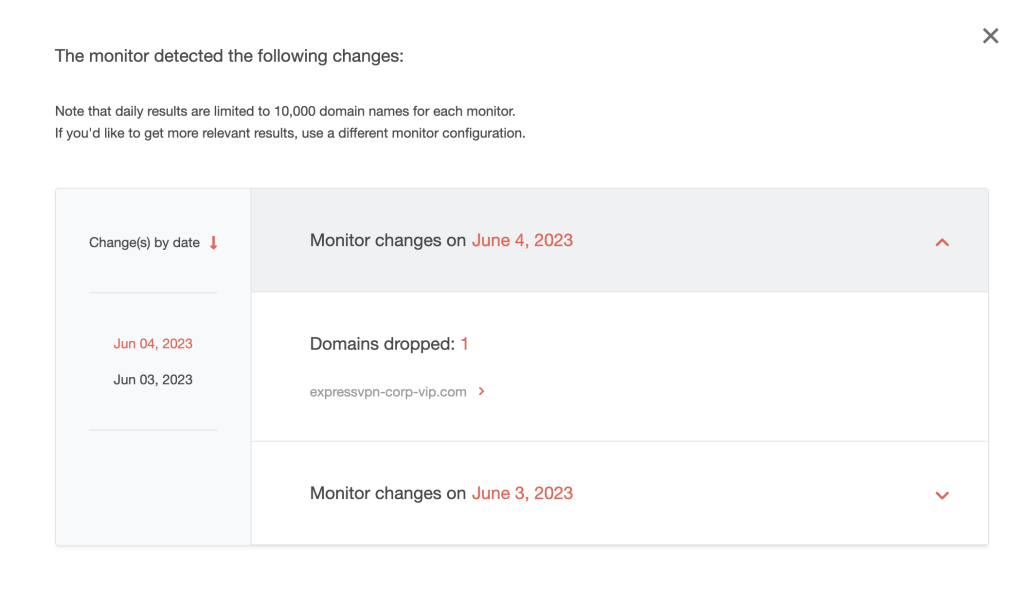
3. The tool will start monitoring newly added, expired, and updated domain records for ExpressVPN within the next 24 hours. Since we started the monitor only on 1 June 2023, we detected that one domain has been dropped as of 7 June.
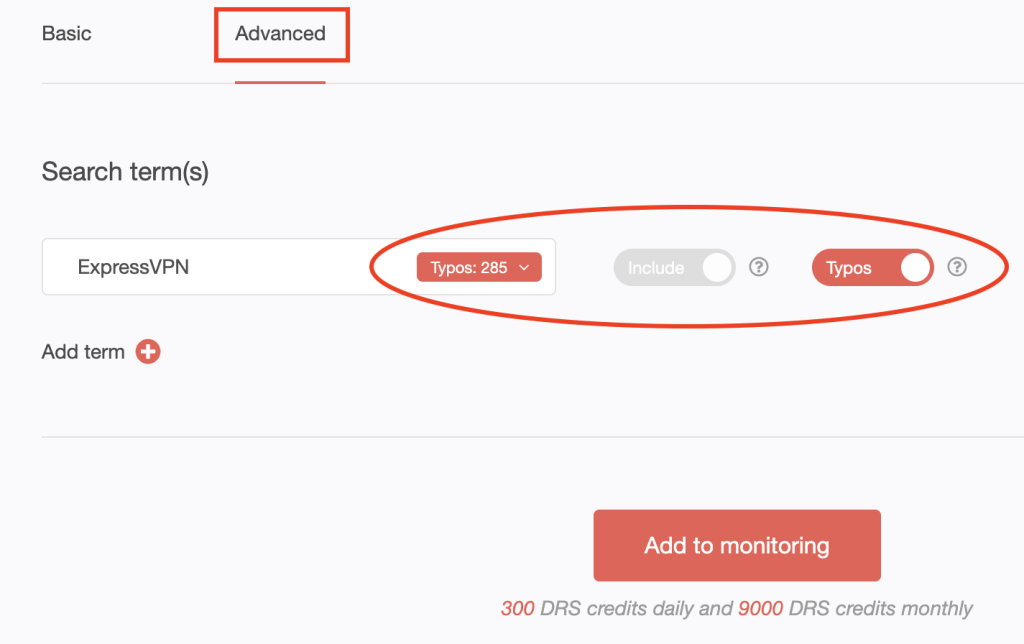
4. [PRO TIP] Use Advanced search to include typo-containing variants and other terms to your monitor. Click Add to monitoring.