Investigating EHR Software Impersonation: A DIY DRS Guide to Threat Discovery
Several ransomware families have been seen targeting healthcare organizations in the past few years, adding to the challenges faced by the healthcare sector. Phishing is a favored initial access vector, where threat actors commonly utilize domain names. This edition of our DIY investigation guide will demonstrate how healthcare security teams and organizations can retrieve and monitor cybersquatting domains using Domain Research Suite (DRS) search and monitoring tools.
Process #1: Investigating and Expanding Known Malicious Cybersquatting Domains
We start by looking into wwwathenahealth[.]com, a cybersquatting domain targeting Athenahealth that had already figured in malicious campaigns. Athenahealth is a famous electronic health record (EHR) system provider.
Step #1: Retrieve the Malicious Domain’s WHOIS Details
Follow these steps:
1. Go to WHOIS History Search, type the domain name, and click Search.
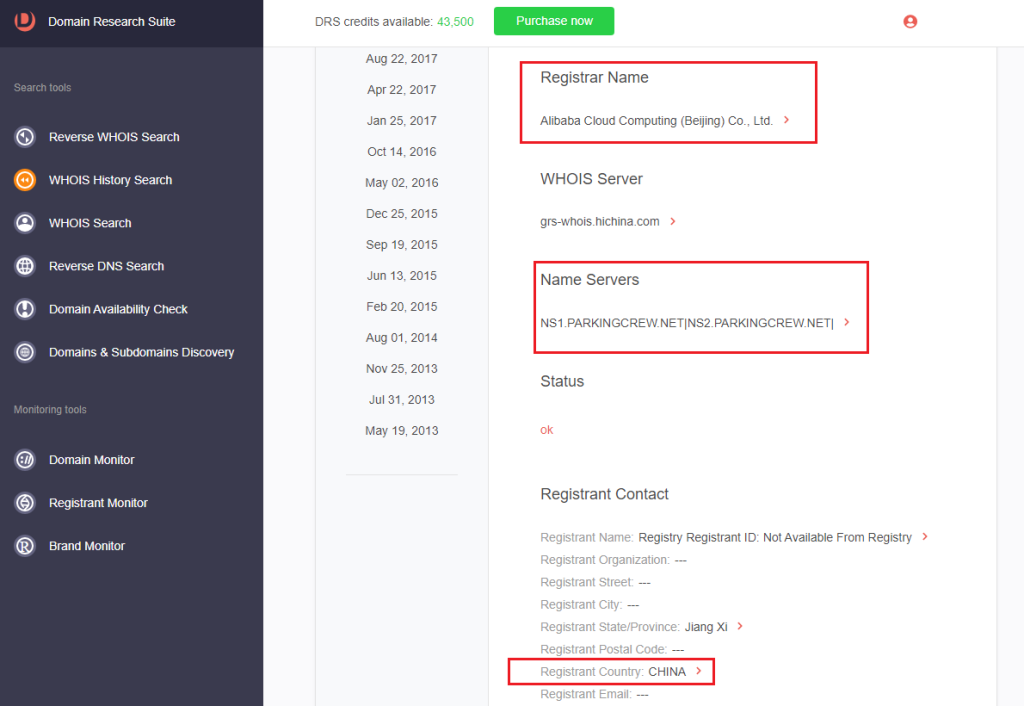
2. Scroll down to the historical WHOIS record with the most public details. For wwwathenahealth[.]com, that record is dated April 30, 2022. The registrar’s name, name servers, and registrant country are available.
Step #2: Find WHOIS-Connected Domains
1. Go to Reverse WHOIS Search and click the Advanced search tab.
2. Under the Search where parameter, select the radio button that says In specific WHOIS fields.
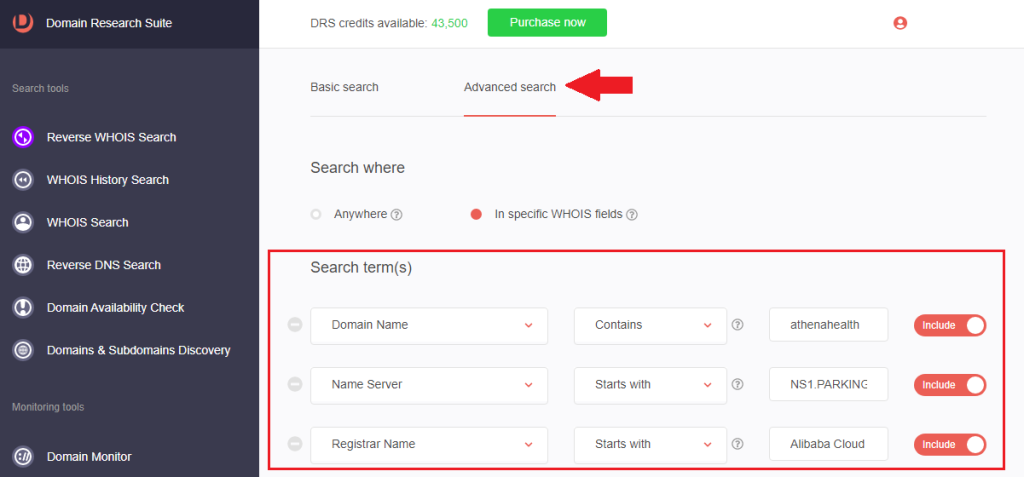
3. Under Search term(s), select the WHOIS field and type the WHOIS detail into the box. We used the name server and registrant name retrieved from the previous investigation for this demonstration. We also included athenahealth as a search string for the Domain Name field.
You may also want to check: How to Trace a Privately Registered Domain’s Owner by Using a WHOIS History Lookup Tool
4. [PRO TIP] You may search through the domain’s current or historical WHOIS records. You can also specify date filters to retrieve domain names created, expired, or updated on specific dates.
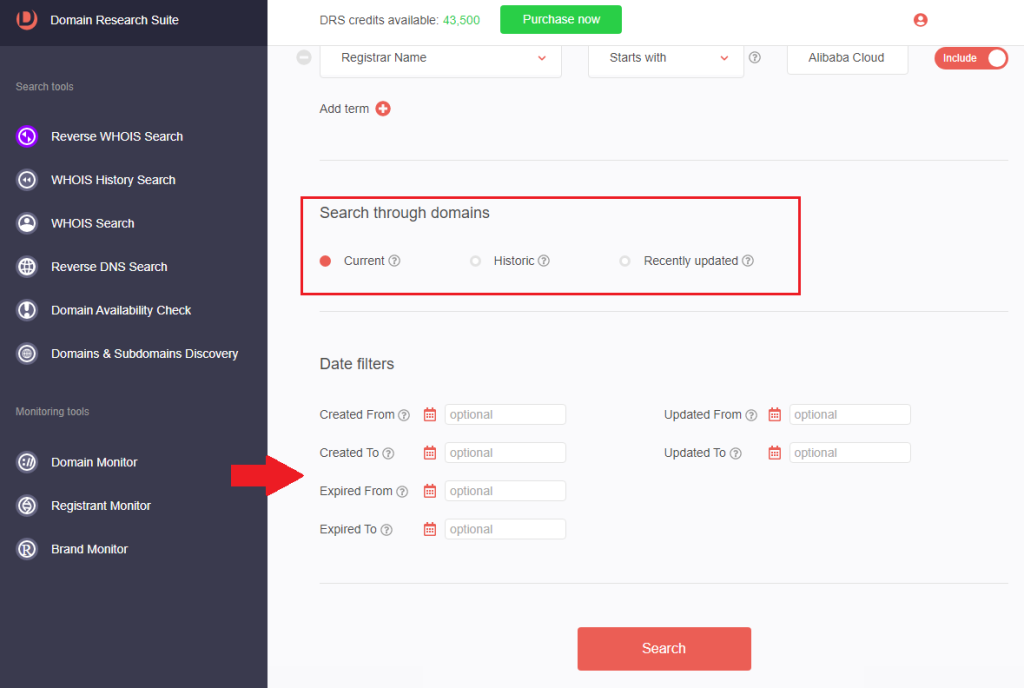
5. In this illustration, we found 10 additional cybersquatting domains targeting Athenahealth that share the same name server and registrar as the malicious domain.
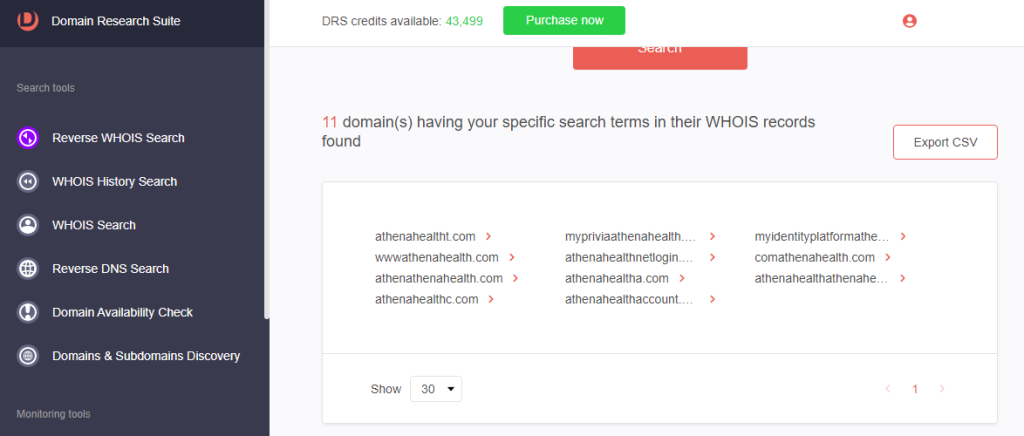
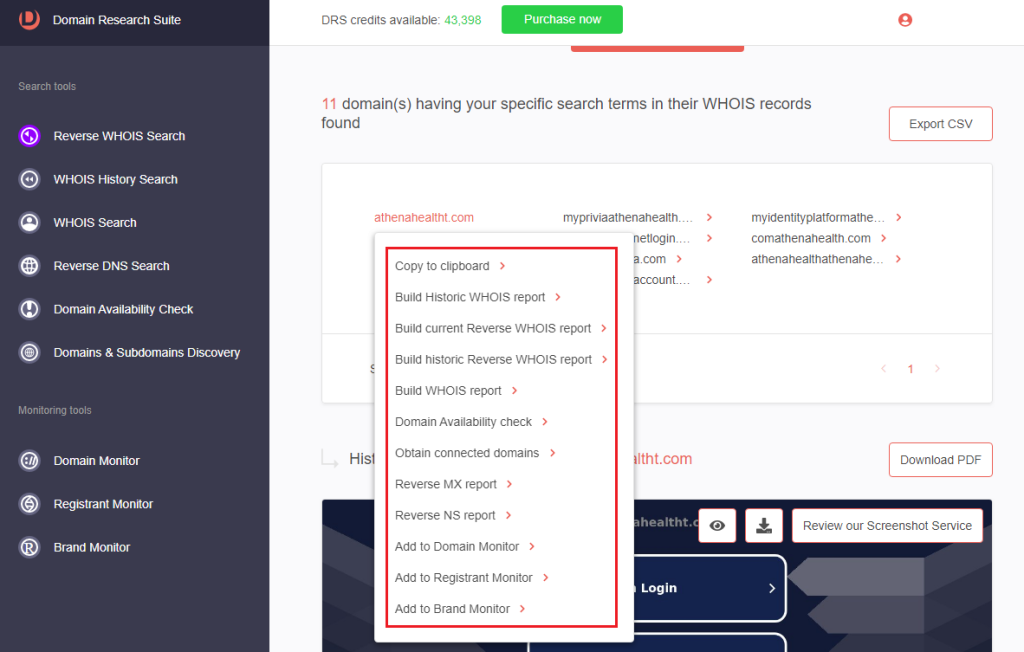
6. [PRO TIP] Click any connected domains to build additional reports.
Process #2: Expanded Threat Discovery
Step #1: Targeted Discovery of Threat Vehicles Targeting a Specific Company
Knowing that there have been malicious campaigns targeting Athenahealth, we can expand our threat discovery to uncover more cybersquatting domains targeting the EHR software provider. To do that, follow these steps:
1. Go to Domains & Subdomains Discovery and make sure that the Domains only option is selected.
2. Type athenahealth into the search box and specify the placement of the search string. For this illustration, we wanted to retrieve all domains that Contains the EHR software’s name.
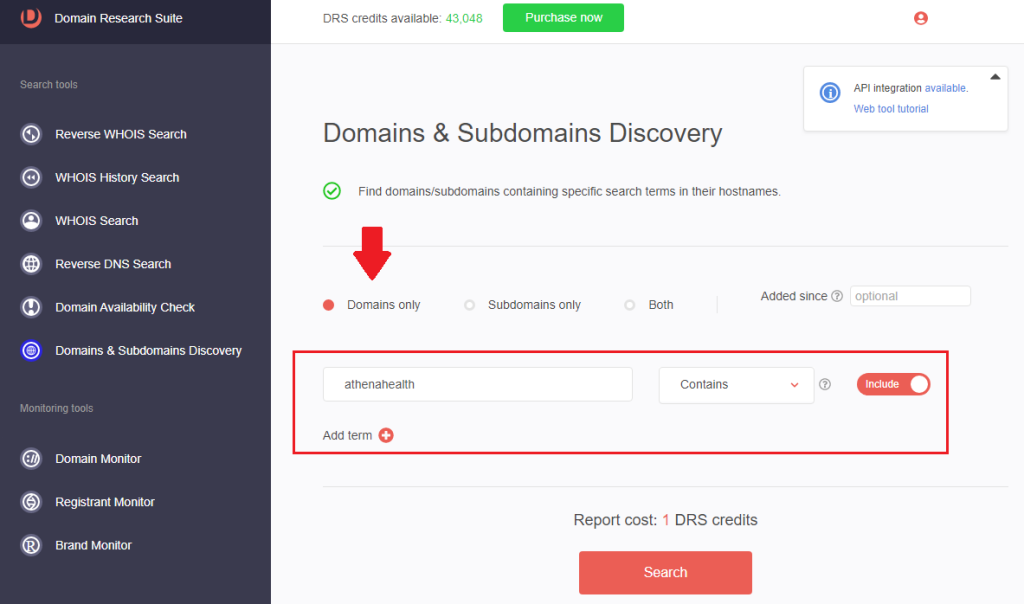
3. [PRO TIP] You can make the search time-bound by specifying an Added since date.
4. Click Search. We found 320 possible cybersquatting domains targeting Athenahealth.
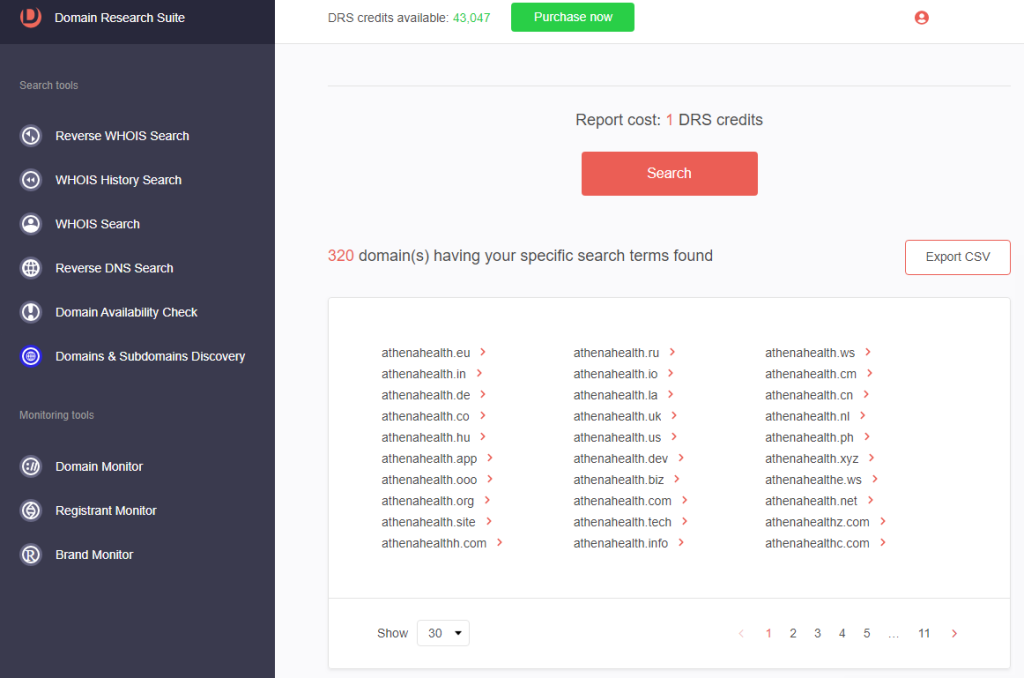
5. [PRO TIP] You may narrow your search by clicking Add term to add another search string. For example, we added login to retrieve potential Athenahealth cybersquatting domains masquerading as the EHR software provider’s login page.
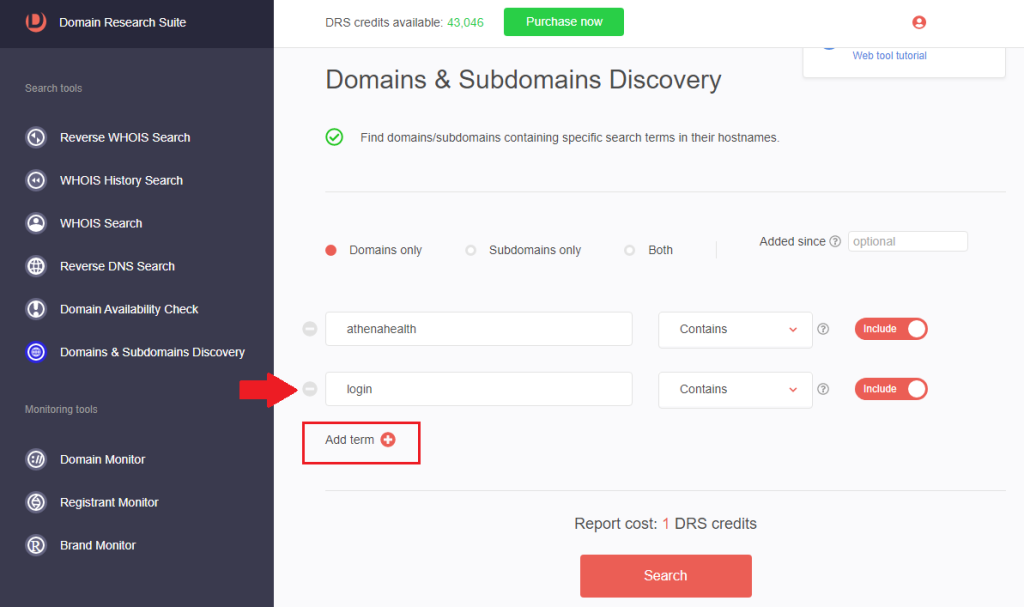
We found nine domains that possibly imitate Athenahealth’s login page.
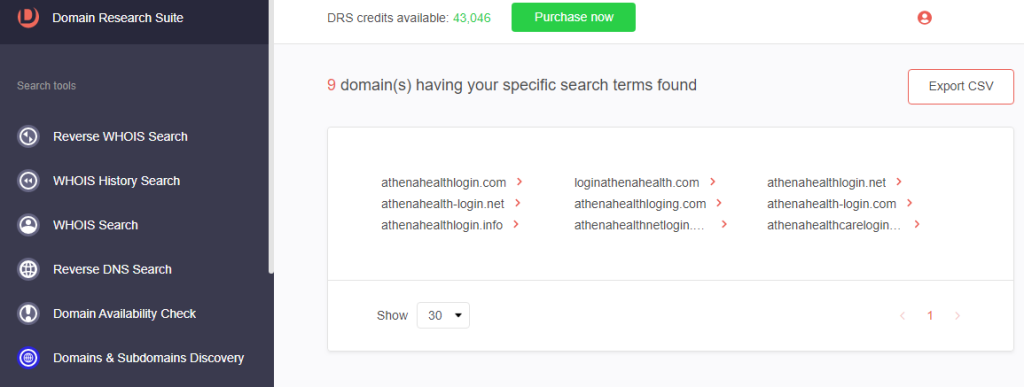
6. Select a cybersquatting domain and click Build Historic WHOIS report to retrieve its WHOIS and other details.
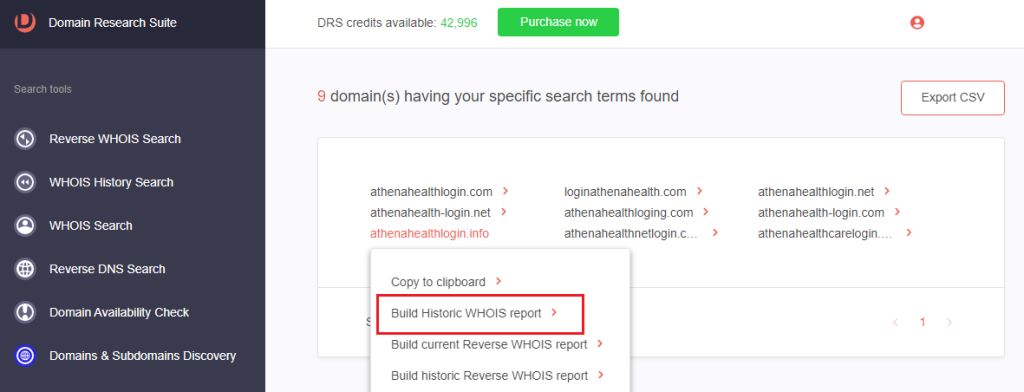
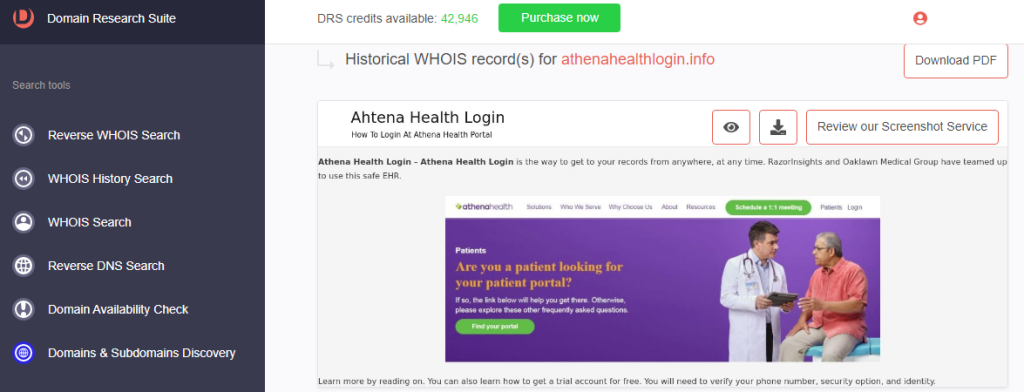
For athenahealthlogin[.]info, we found these details:
a. Website screenshot
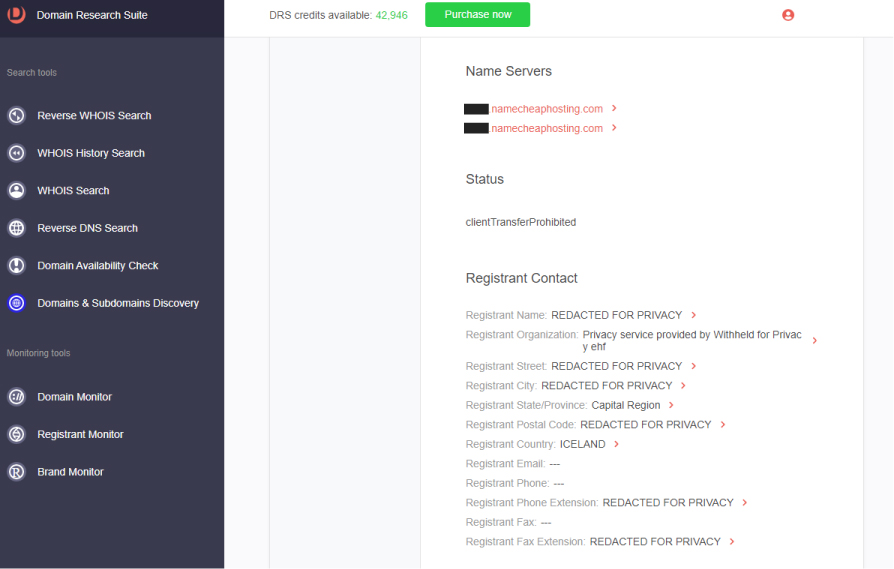
b. Name servers
c. Registrant contact details
7. Go to WHOIS Search, type the official domain name of the imitated company and click Search.
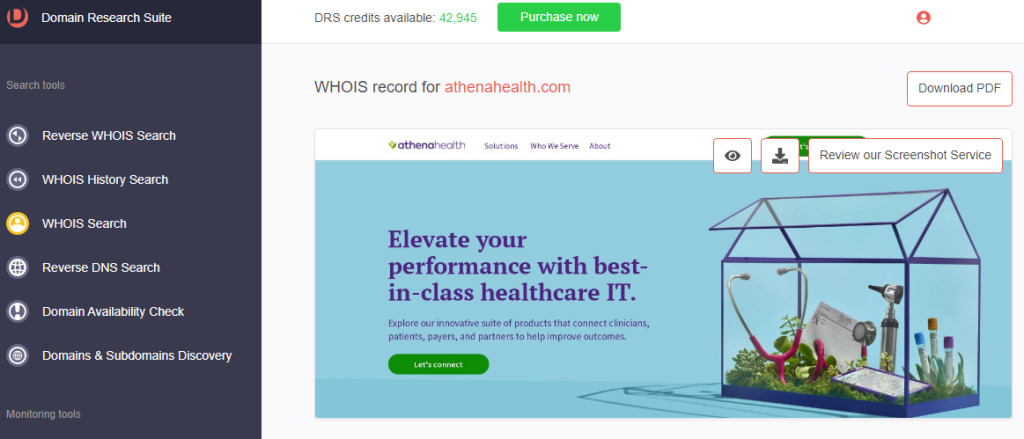
8. Compare the WHOIS details of the official domain and the cybersquatting domain.
a. Website screenshot: The home page of the legitimate Athenahealth website looks different from athenahealthlogin[.]info.
b. Name servers: While athenahealthlogin[.]info uses generic name servers from the registrar, the official domain is hosted on several dedicated name servers.
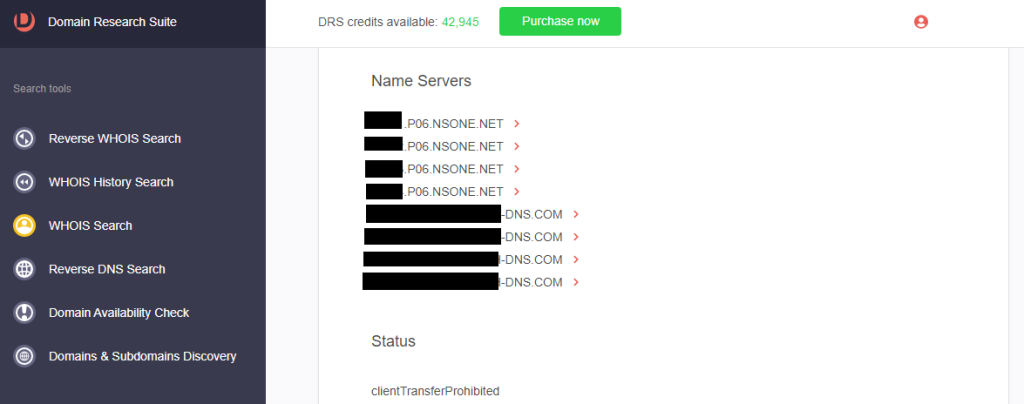
c. Registrant contact details: The registrant details of the official domain are not redacted, while that of the cybersquatting domain are.
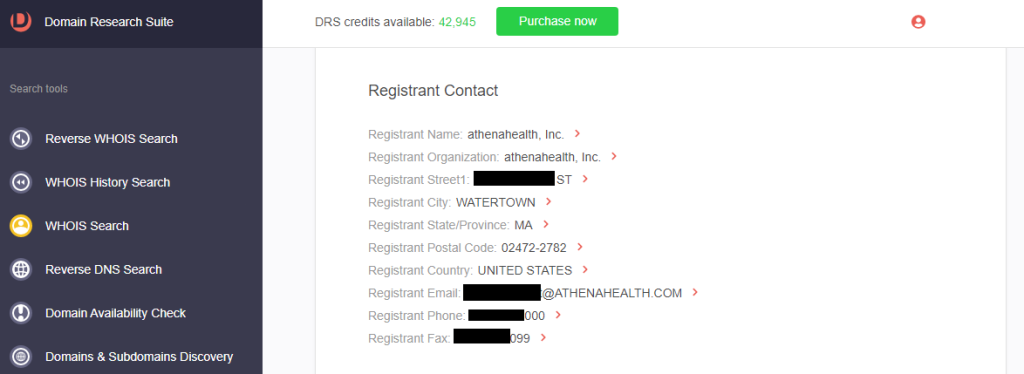
9. [PRO TIP] Since an EHR software provider is targeted, it’s wise to see what other players in the industry are also targeted. Perform steps 1 to 4 using the names of other EHR software providers like Kareo Clinical and NextGen.
Step #2: Industry-Specific Threat Discovery
Aside from cybersquatting domains, threat actors might use generic industry terms in their domains. Here are the steps to follow:
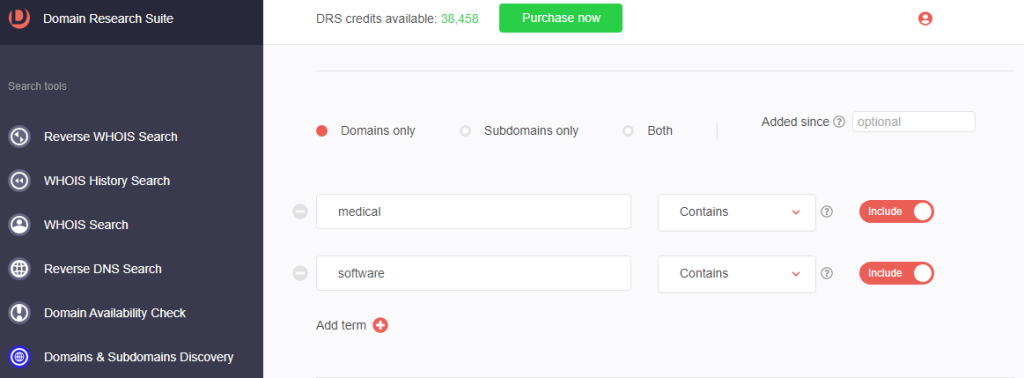
1. Go to Domains & Subdomains Discovery.
2. In the search box, type industry-targeted search string that threat actors may use, such as:
a. ehr and system
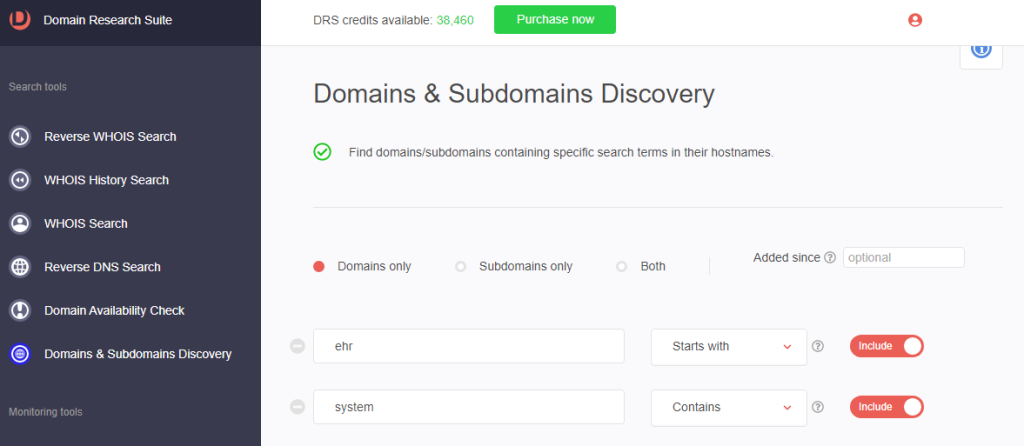
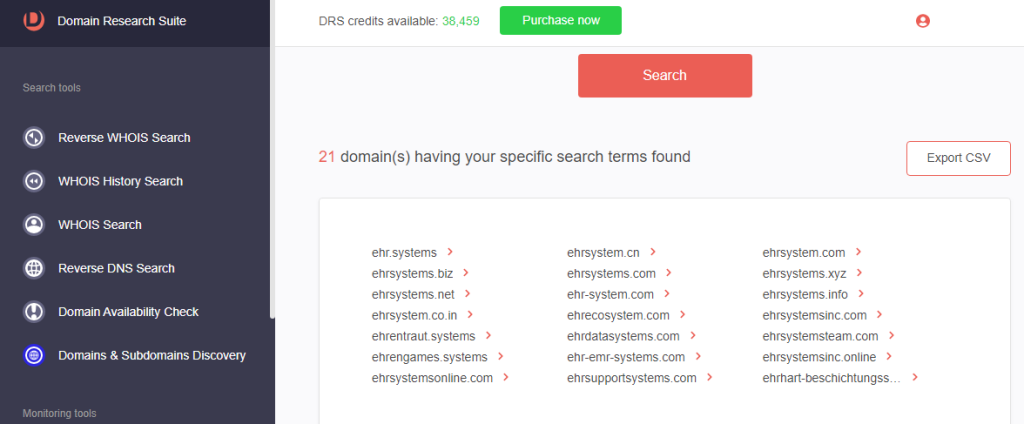
b. [PRO TIP] For search strings that begin with vowels, set the string placement to Starts with. There are 21 domains that start with ehr and contain the string system.
c. medical and software
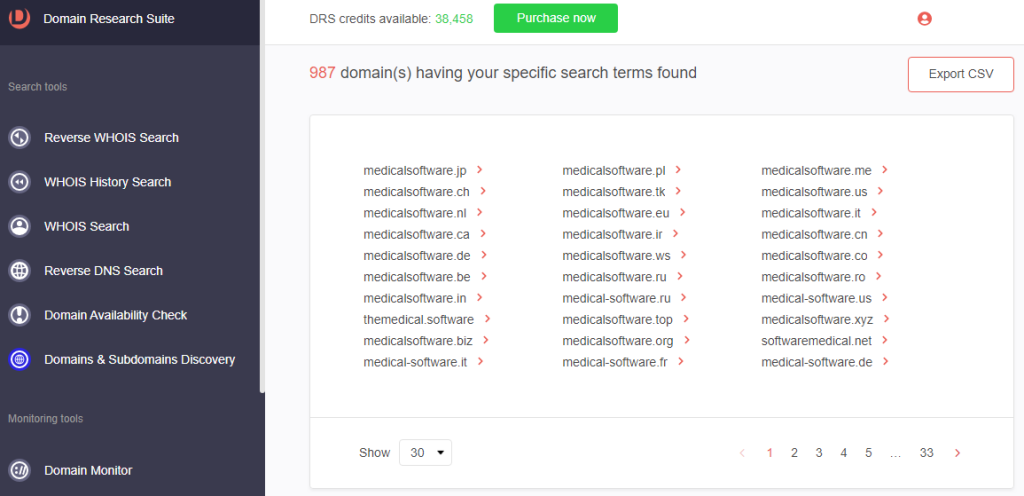
Process #3: Threat Monitoring
Set up a daily monitor of newly added, dropped, and updated domains that contain a specific EHR software company’s name. Follow these steps:
1. Go to Brand Monitor.
2. Type the company name and click Add to monitoring. That adds the search strings to Brand Monitor, which will have an update typically 24 hours after setting up the monitor.
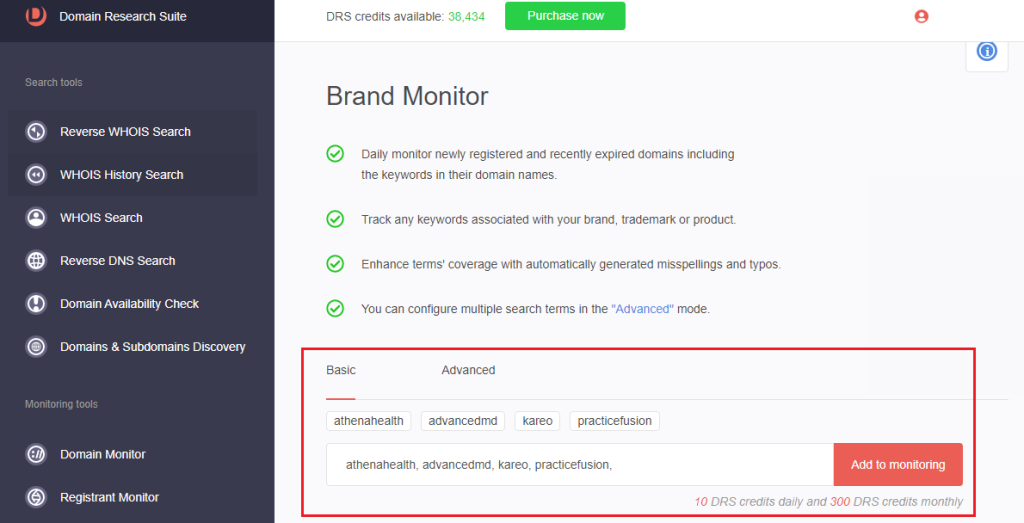
3. [PRO TIP] Use the Advanced search method to include typo variants of the company names.
Impersonating top companies in the DNS is widespread across various industries. In the healthcare software sector alone, we dug up more than a thousand cybersquatting domains targeting some of the most popular EHR software providers using Step #1 of Process #2. Proactive threat discovery and investigation can help prevent any threat that can be carried out using these domains.
Are you interested in doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.




































