Staying One Step Ahead of BEC Scams: A DIY DRS Guide to Threat Discovery
Business email compromise (BEC) scams cost organizations billions of dollars annually, making it a lucrative business for threat actors. BEC campaigns commonly spoof target companies and reputable email and electronic document service providers.
In this edition of our DIY investigation guide, we will demonstrate how companies and their security teams can detect potential BEC scam vehicles in the DNS using the Domain Research Suite (DRS) search and monitoring tools.
Process #1: Tracing Known BEC Vehicles in the DNS
BEC threat actors were recently seen sending phishing emails that spoofed a DocuSign email address. More email domains imitating the electronic document management provider could sit in the DNS, waiting to be weaponized. To uncover possible BEC scam vehicles spoofing DocuSign, follow these steps:
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only.
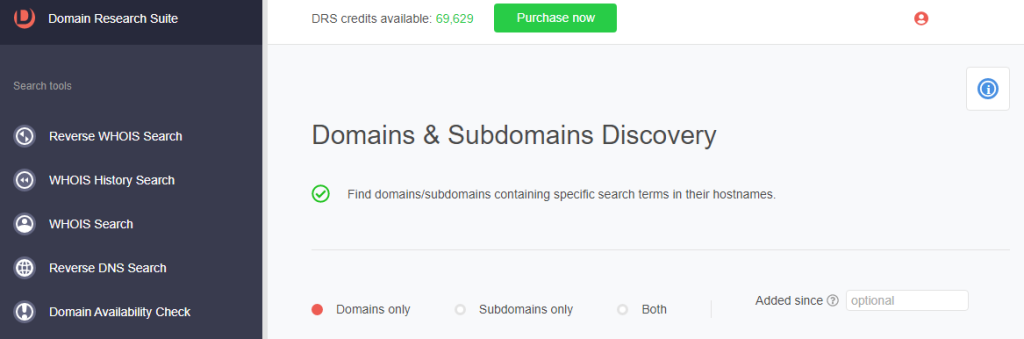
2. Type docusign into the search field.
3. Set the string placement parameter and click Search. For this demonstration, we limited our search to domains that Start with docusign.
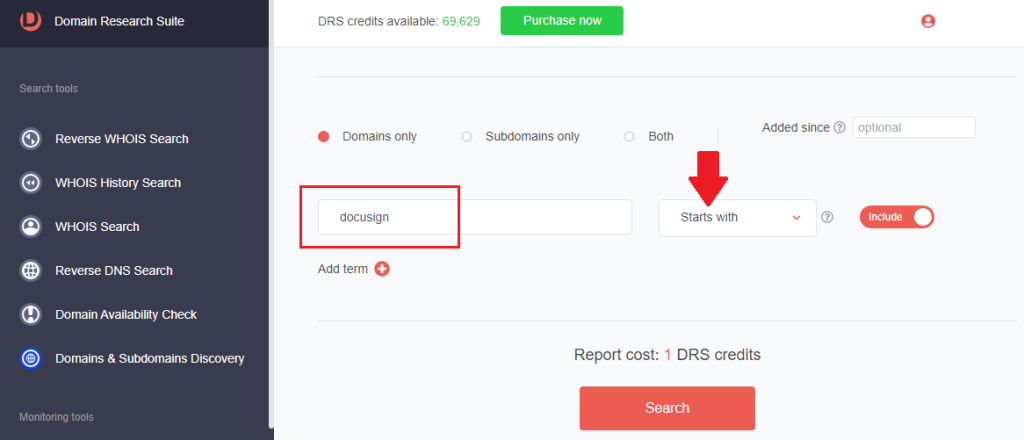
4. We found 1,958 domains.
5. Scroll up to go back to the top of the page. Select Subdomains only.
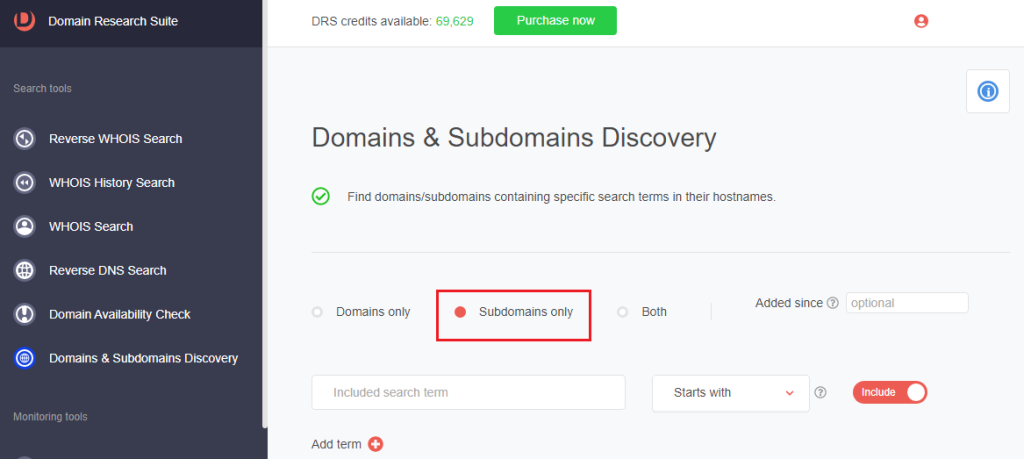
6. Type docusign into the search box to retrieve subdomains containing the string.
7. Set the string placement parameter and click Search. For this demonstration, we limited our search to subdomains that Start with docusign.
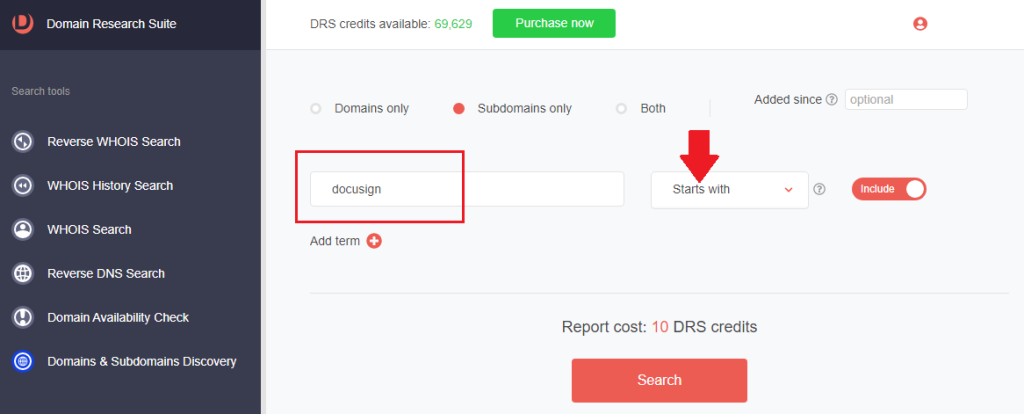
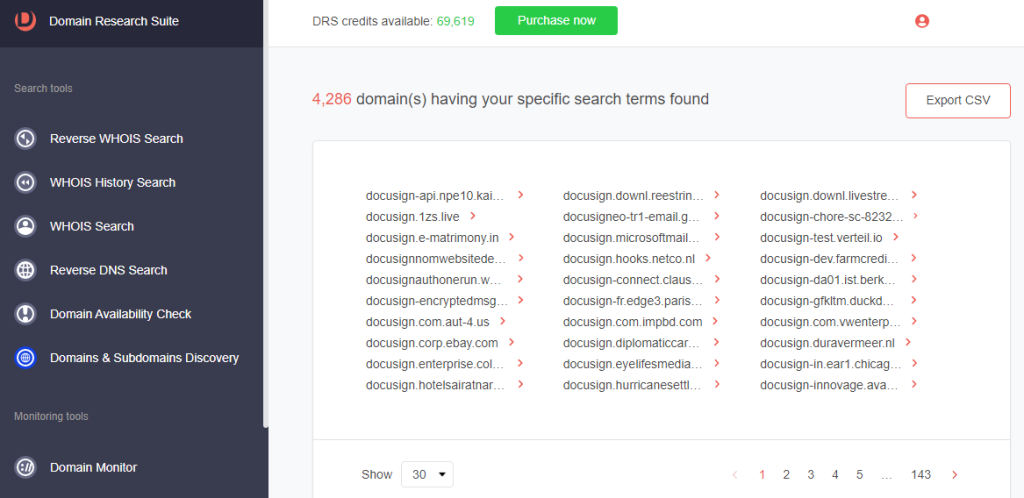
8. We found 4,286 subdomains that start with the string docusign.
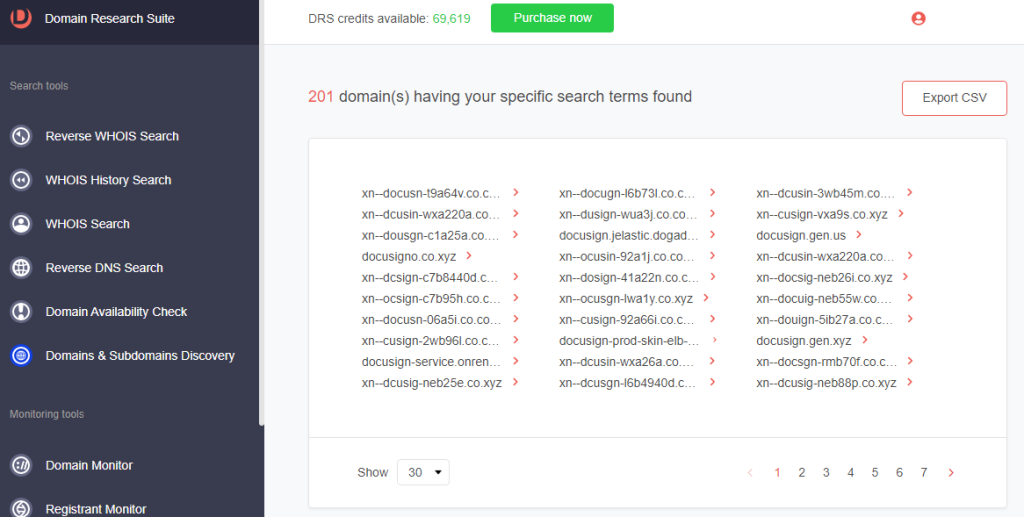
9. [PRO TIP] Make your domain and subdomain searches time-bound by setting the Added since parameter.
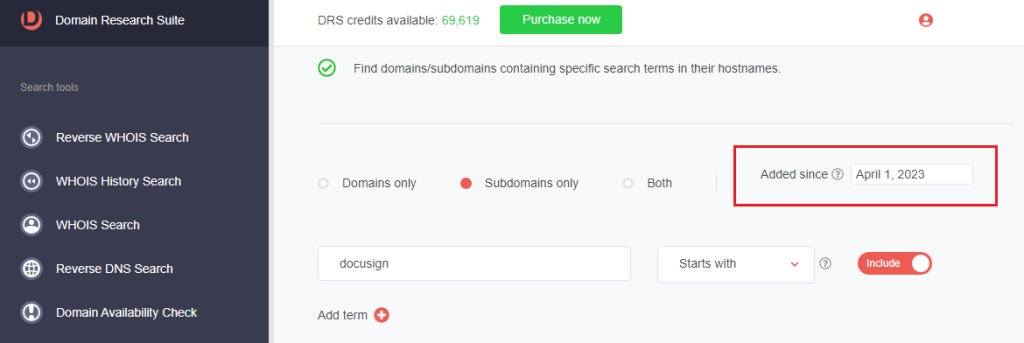
We found 201 subdomains added since 1 April 2023 that start with docusign.
Process #2: Identifying Possible BEC Scam Vehicles Targeting the Supply Chain
A BEC threat actor impersonated one of Google’s and Facebook’s third-party associates, collecting more than US$100 million from both companies by sending fake invoices and contracts for years. DRS can help identify potential BEC scam vehicles imitating third parties. Follow the steps below.
Step #1: Uncovering Domains Imitating a Third Party
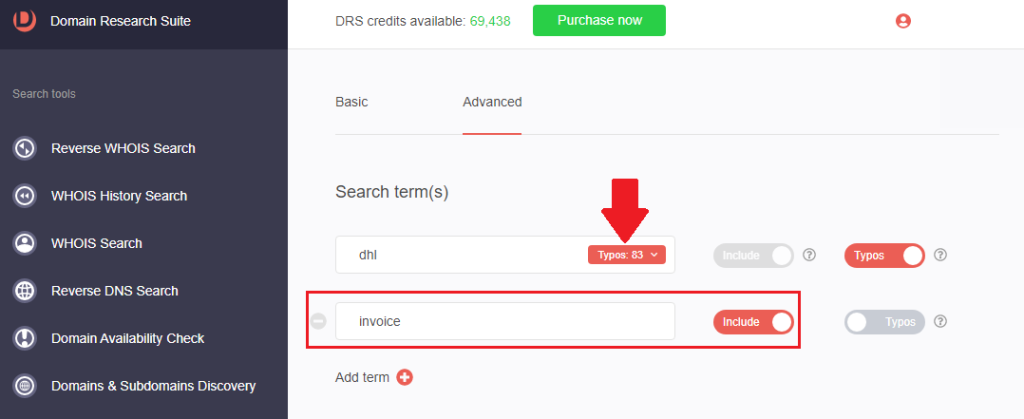
1. Go to Domains & Subdomains Discovery, select Domains only and type the company name into the search field. We will demonstrate this process using DHL.
2. [PRO TIP] To make the search more targeted, include keywords that threat actors are likely to use. In our illustration, we included invoice as a search string.
3. Set the string placement parameter and click Search. For this demonstration, we limited our search to domains that Start with dhl and Contain invoice.
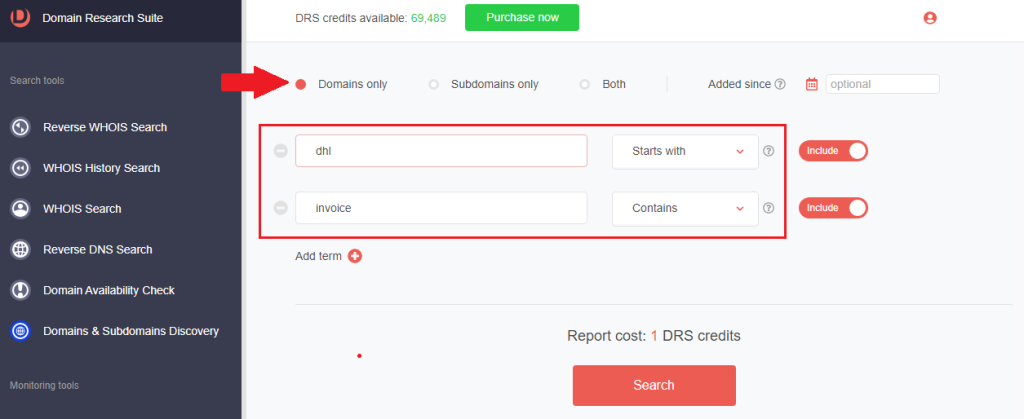
4. We found 23 domains.
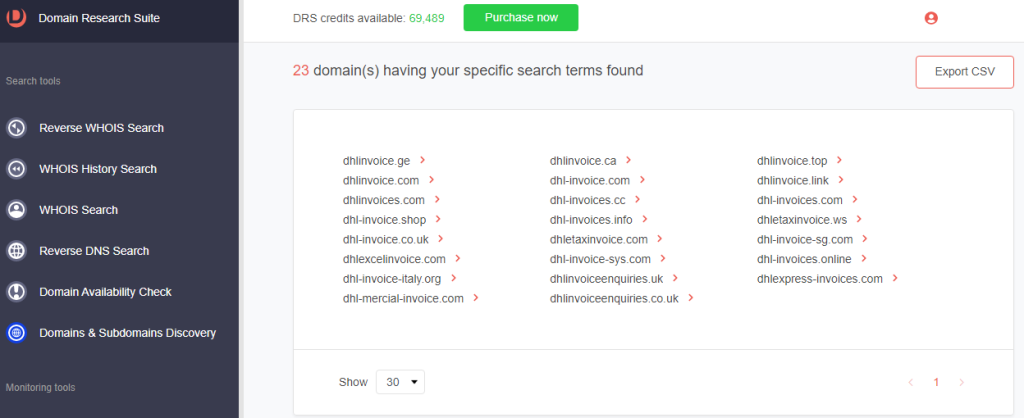
5. Click a domain and select Build Historic WHOIS report.
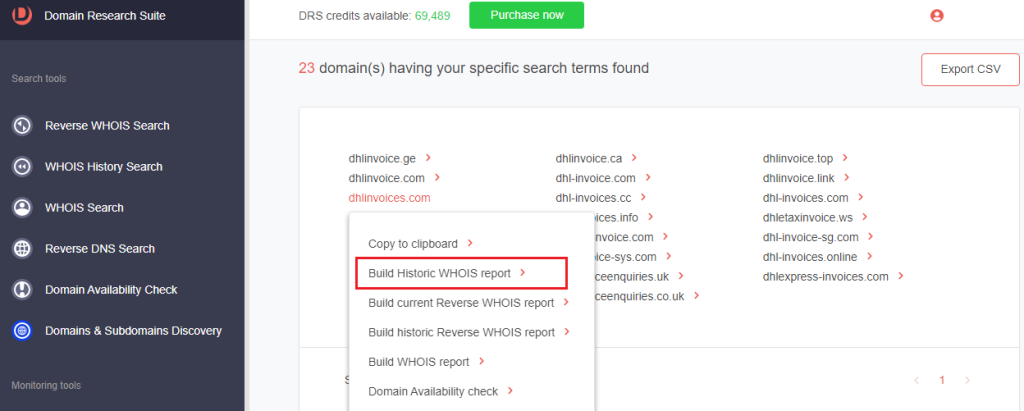
6. Check the following details:
a. Website screenshot

b. Metadata
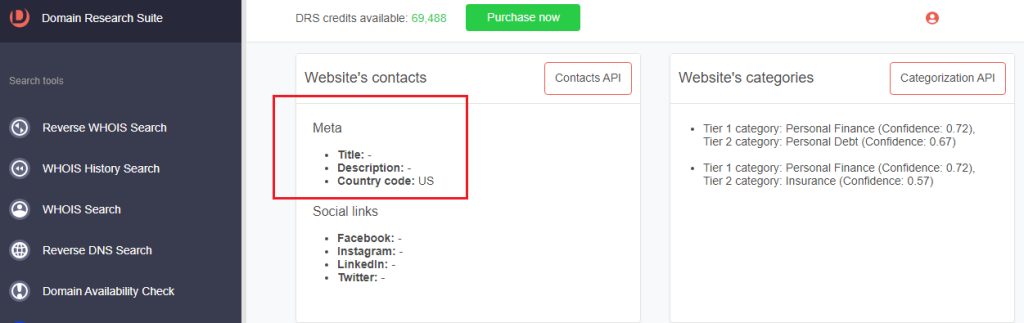
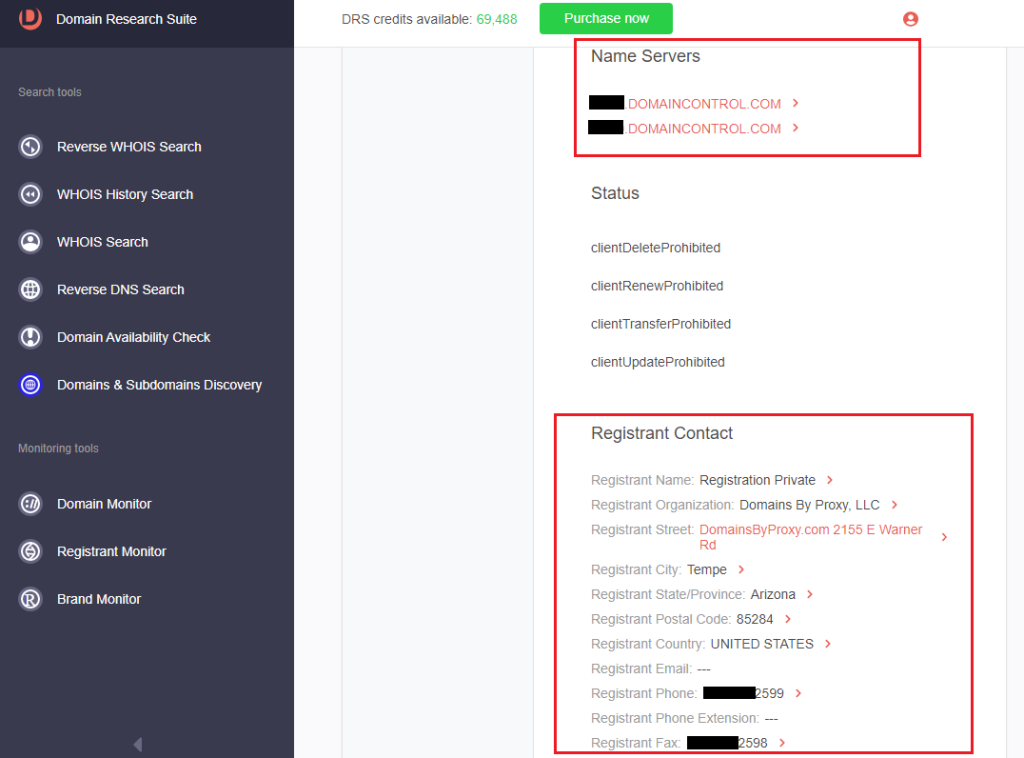
c. Name servers
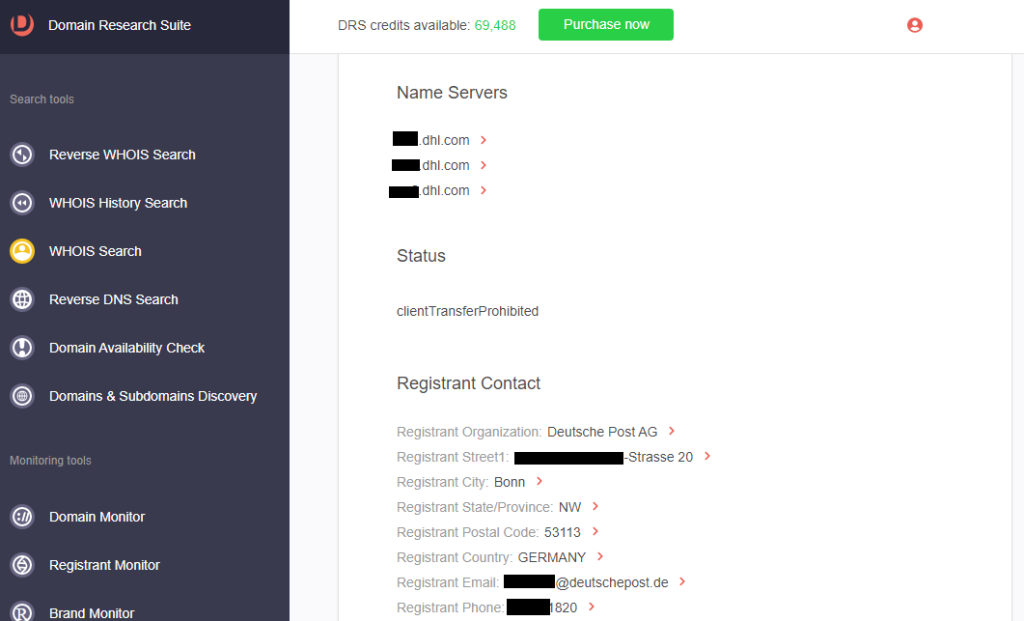
d. Registrant contact details
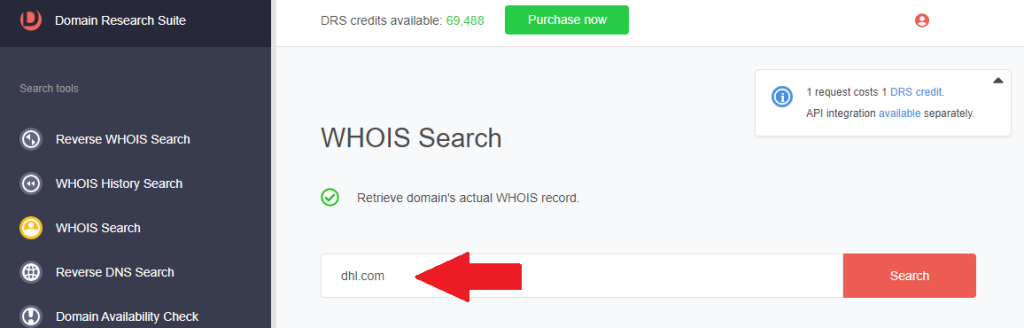
7. Go to WHOIS Search to retrieve the current WHOIS details of the impersonated company. Type the official domain name dhl[.]com for our sample investigation.
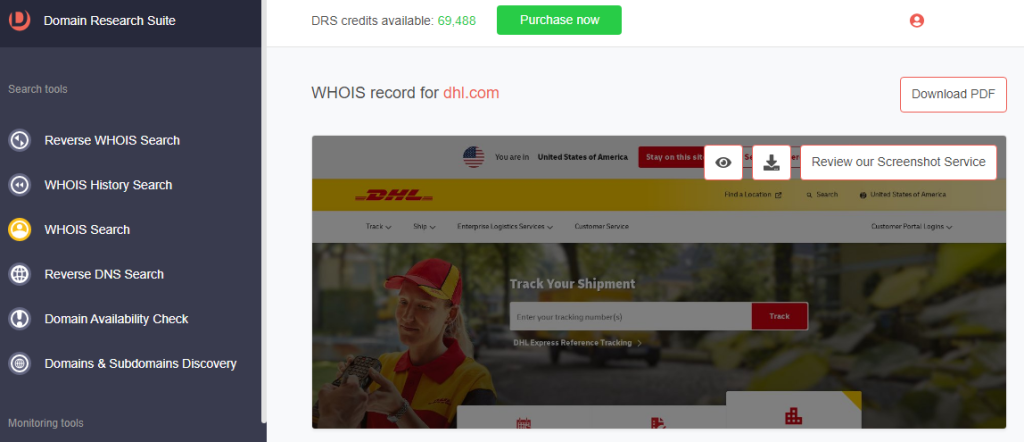
8. Compare the official details with those of the domain from step #6 and note the differences.
a. Website screenshot: While dhlinvoices[.]com used DHL’s brand colors and logo, its web content differed from the official website’s as shown below.
b. Metadata: The official domain’s metadata has been configured while that of the impersonating domain was left blank.
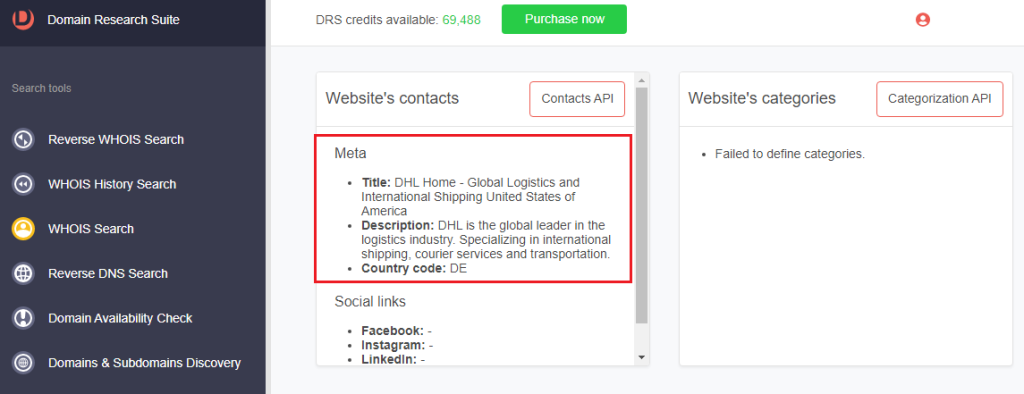
c. Name servers and registrant contact details: DHL uses its official email address and name servers, while dhlinvoices[.]com had a redacted email address and different name servers.
Step #2: Monitoring the DNS for New Domains Spoofing a Third Party
Track the registration of domain names, possibly impersonating an entity in your supply chain. To do that, follow the steps below.
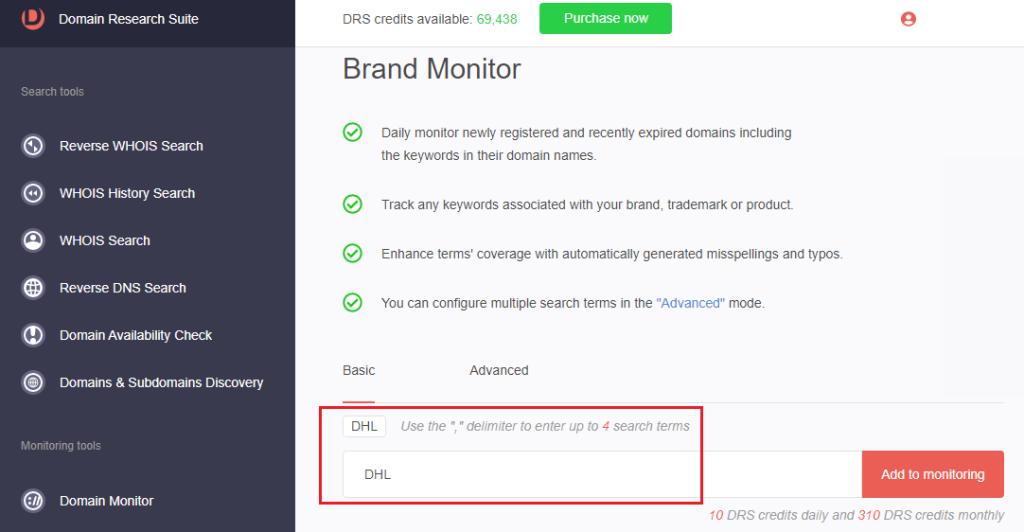
1. Go to Brand Monitor.
2. Type the company name and click Add to monitoring.
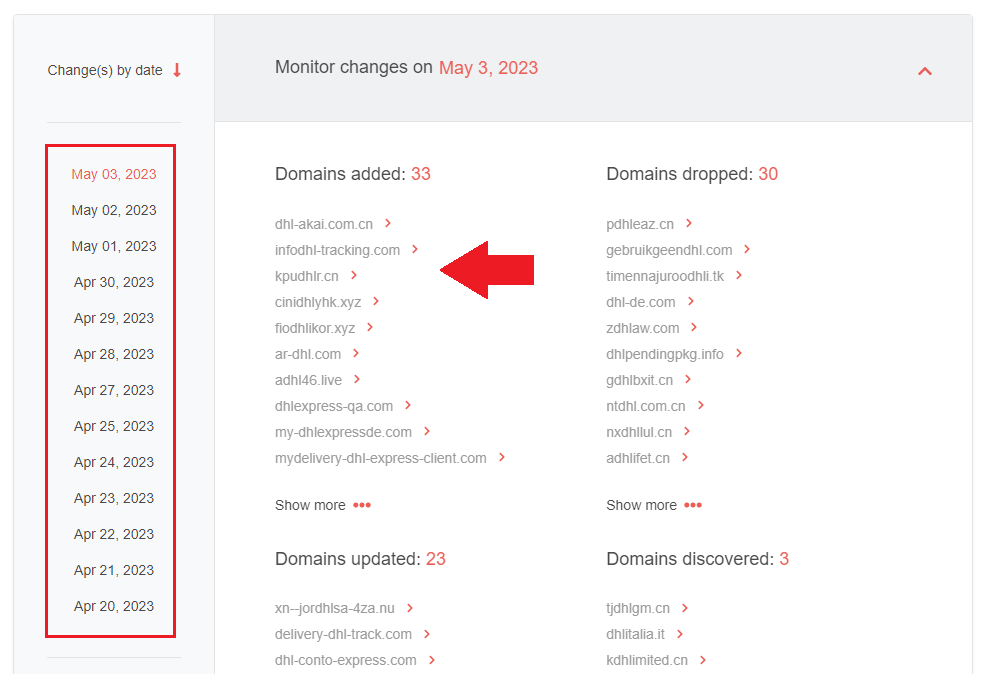
3. The tool will start monitoring the search term in newly added, expired, and updated domains’ records within 24 hours. We have been tracking dhl since 20 April 2023 and detected an average of 36 newly registered domains (NRDs) per day.
4. [PRO TIP] Use the Advanced search option to include typo-containing variants and other terms in the monitor.
Process #3: Investigating Publicly Available BEC Scam Indicators
Security companies and researchers publish indicators of compromise (IoCs) related to BEC scams. To provide context and learn more about these IoCs, follow these steps:
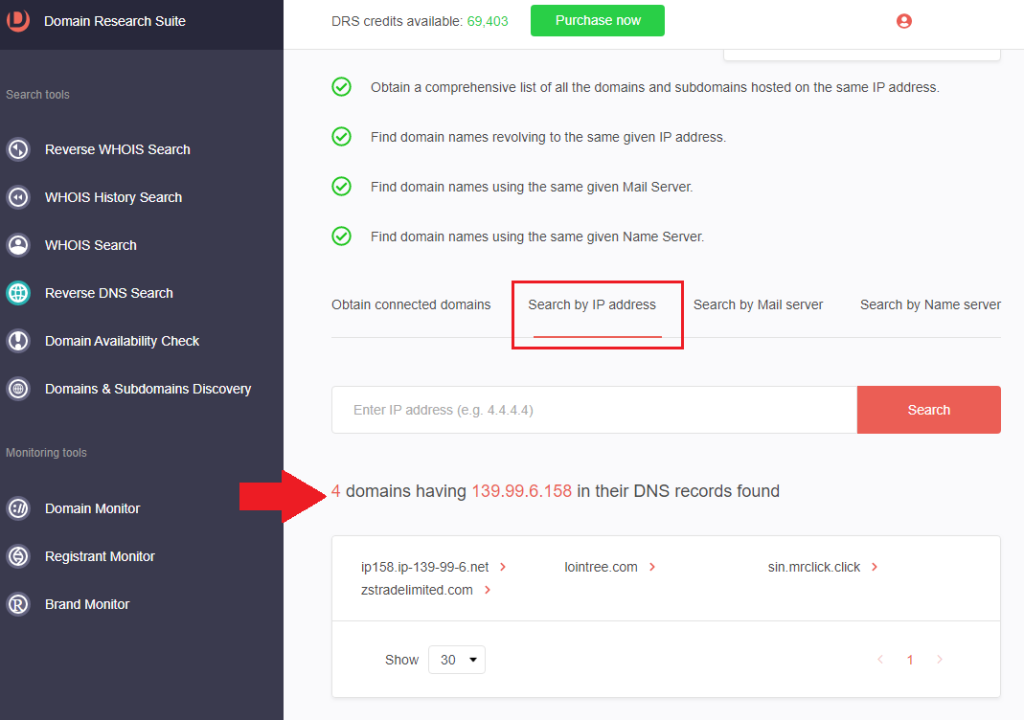
1. Go to Reverse DNS Search. For IP addresses tagged as IoCs, click Search by IP address.
2. Type the IP address and click Search. To demonstrate, we used 139[.]99[.]6[.]158, an IoC related to a recently reported BEC scam. The tool returned four domains sharing the IP host.
3. Click a connected domain and select Build Historic WHOIS report and study its WHOIS details.
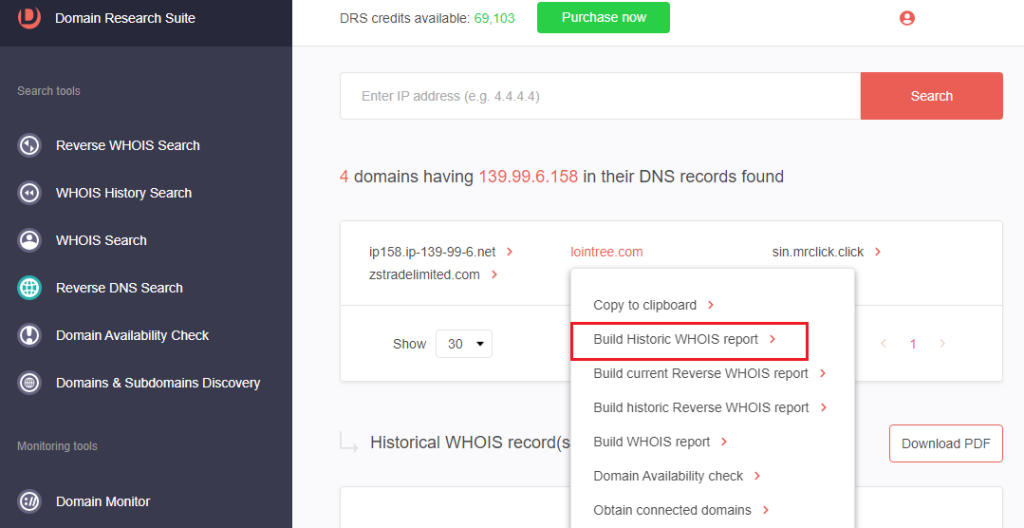
4. Repeat step #3 for a few other connected domains and compare the results with the others. Three of the four domains resolving to 139[.]99[.]6[.]158 had redacted WHOIS records and were created in 2022.
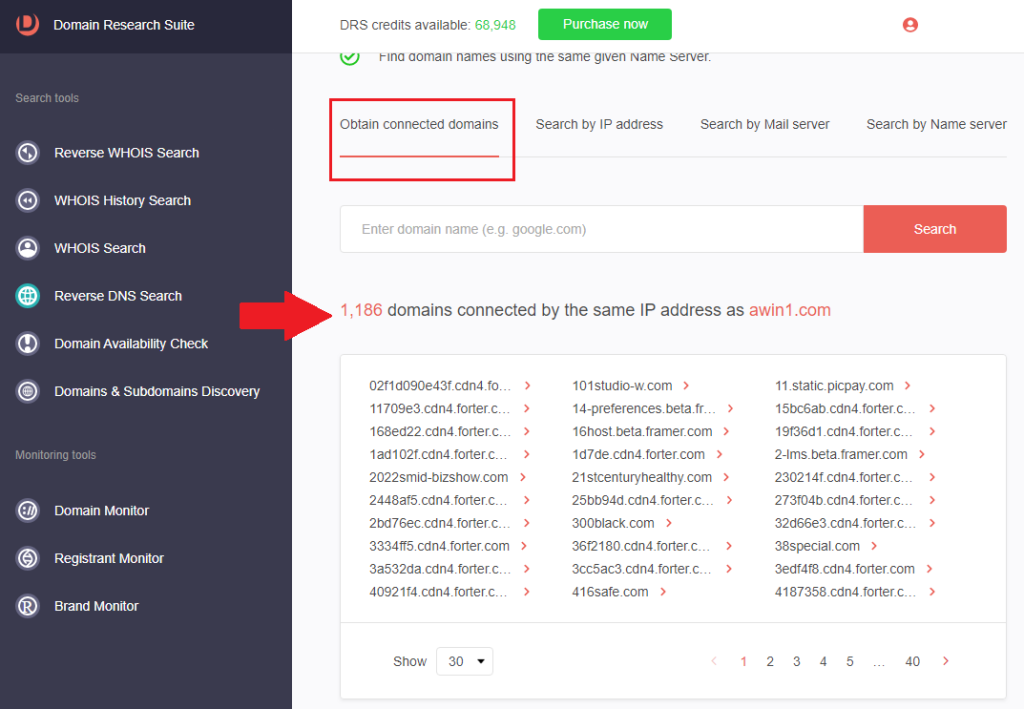
5. Scroll back to the top of the page and click Obtain connected domains if your IoCs include domains.
6. Type the domain and click Search. We used awin1[.]com, another IoC tagged in a recently reported BEC scam, for this demonstration.
7. The tool returned 1,186 connected domains.
Domains and subdomains are commonly used as vectors for BEC scams and other fraudulent activities. In this DIY investigation, we identified web properties related to tools abused by threat actors in BEC scams. We also detailed how to look for domains possibly impersonating third parties. These processes enable accelerated threat detection and help organizations avoid costly incidents.
Are you interested in doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.




































