Exploring a Zoom-Targeted Campaign: A DIY Domain Research Suite (DRS) Guide to Threat Investigation
Popular software products and applications are often prime targets of cyber attacks—Zoom being one of them. With about 300 million users, Zoom has been repeatedly targeted by malware distribution campaigns, phishing attacks, and other threats. This edition of our DIY investigation guide will look into one of the most recent Zoom attacks, where malicious actors distributed IceID malware through the video communication platform. Our demonstration used different Domain Research Suite (DRS) search and monitoring tools.
Step #1: Uncovering DNS Connections
We obtained a list of IoCs from Cyble, comprising two domains and one IP address. Diving into the malicious properties, we uncovered domains sharing the IoCs’ IP host. We did this through these steps:
1. Go to Reverse DNS Search and make sure you’re on the Obtain connected domains tab.
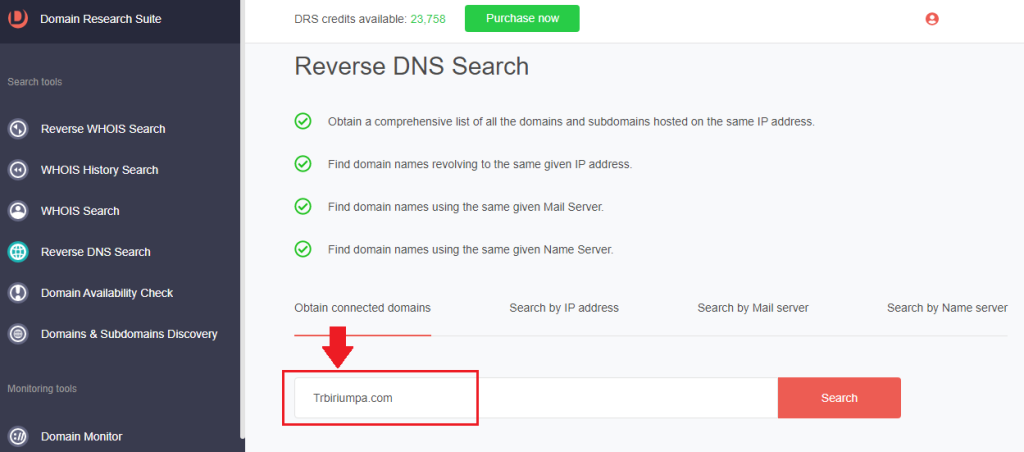
2. Type the domain tagged as a threat IoC and click Search. For trbiriumpa[.]com, we found three additional connected domains.
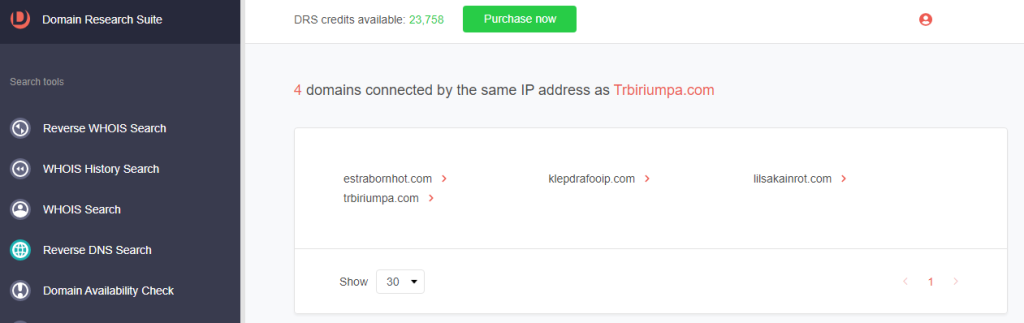
Step #2: Following WHOIS Clues
Now that we have three artifacts, we can dig deeper to see if they share more than an IP host with the IoCs. We demonstrated how to do that below.
1. From the lookup results from Step #1, click a domain name and select Build Historic WHOIS report.
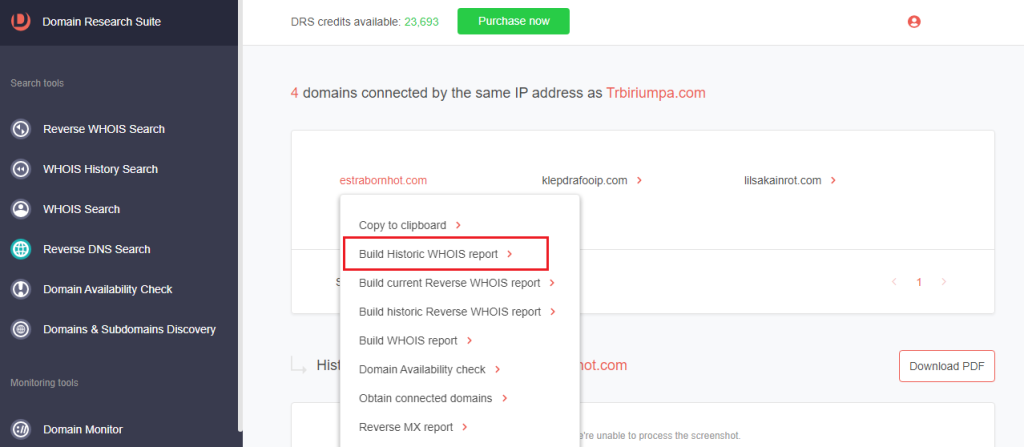
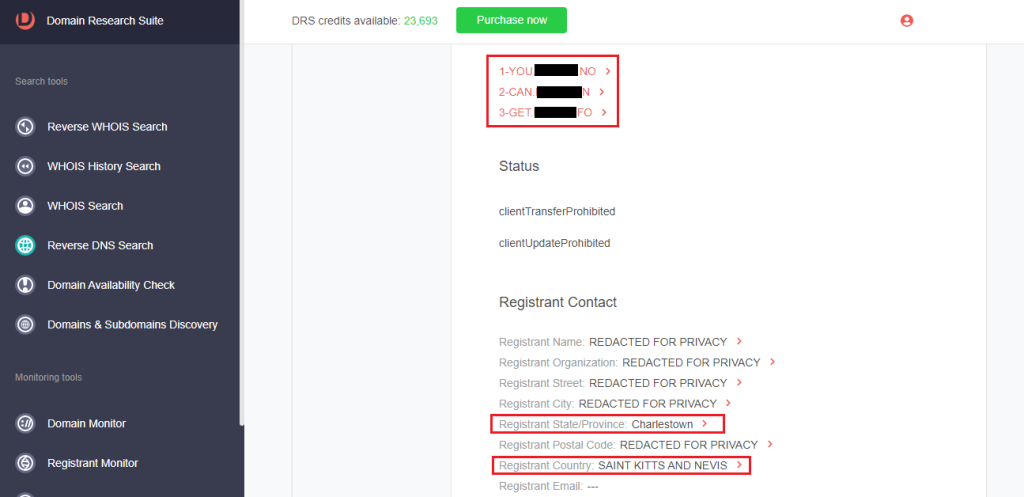
2. Browse through the WHOIS details to find unredacted records.
3. Do the same for the other connected domains to find commonalities. For the domains connected to trbiriumpa[.]com, we found that they had the same name server, registrant province, and country.
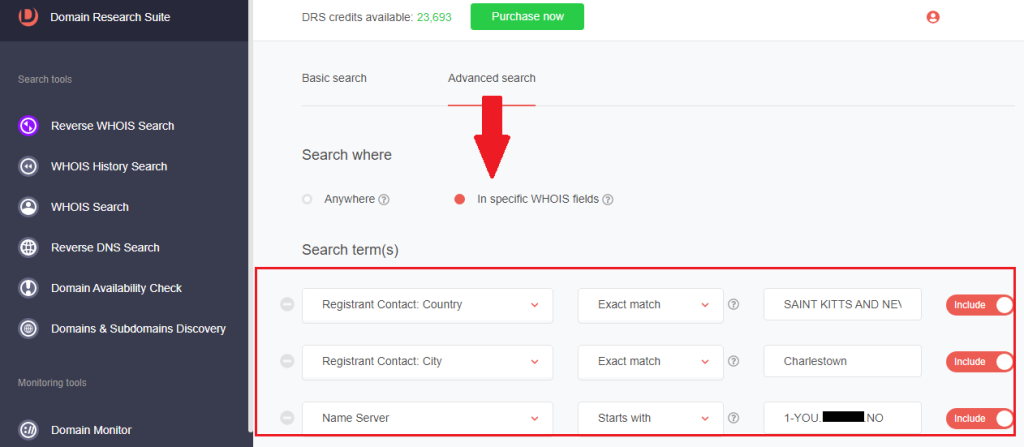
4. Go to Reverse WHOIS Search and click Advanced search.
5. Under Search where, toggle the radio button to In specific WHOIS fields.
6. Under Search term(s), select the WHOIS fields with common details and type the strings into the corresponding box.
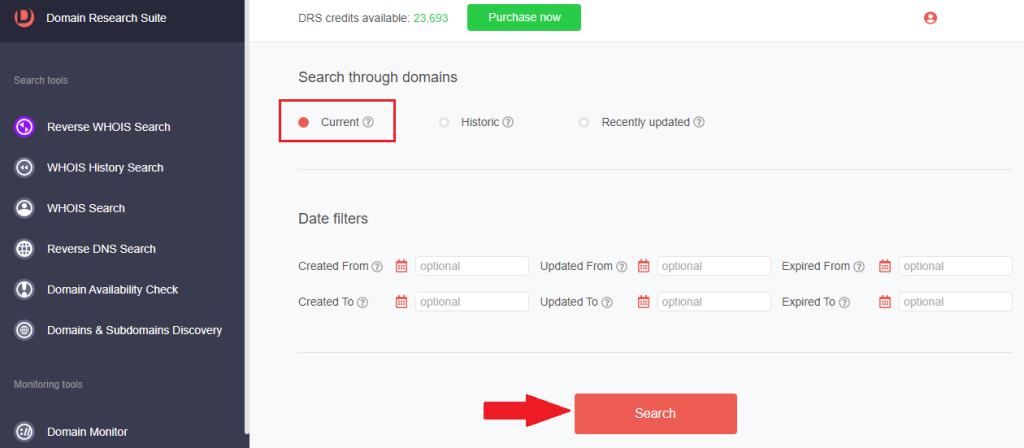
7. Under Search through domains, toggle the radio button to Current and click Search.
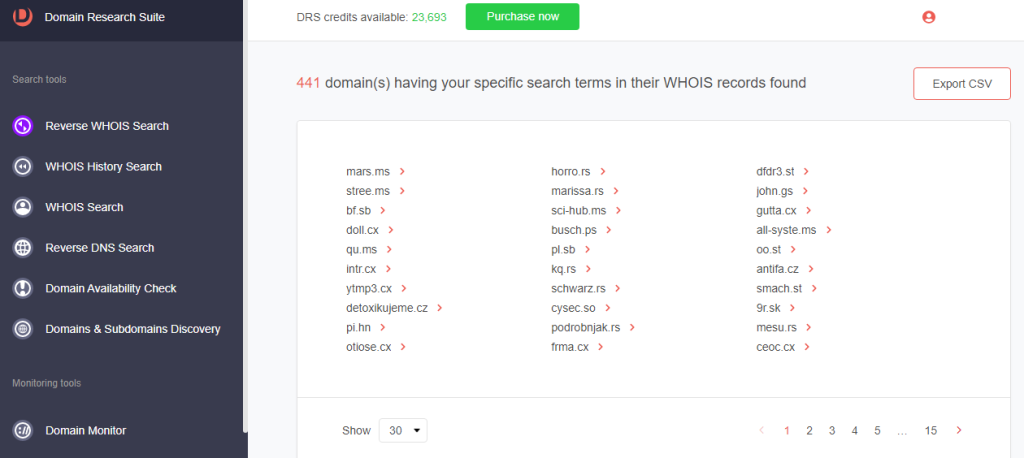
8. We found 441 additional domains connected through the artifacts’ name server and registrant location using this process.
9. [PRO TIP] You may monitor the appearance of common WHOIS details in newly added, updated, and dropped domains by adding them to Registrant Monitor.
Step #3: Zooming in on Typosquatting Web Properties
When targeting large companies, threat actors commonly imitate them by adding their brands to domain names. In fact, one of the IoCs in the recent Zoom cyber attack is the typosquatting domain explorezoom[.]com.
Method #1: Uncovering Typosquatting Domains
To find typosquatting domains that can potentially be used in malicious campaigns, follow these steps:
1. Go to Domains & Subdomains Discovery.
2. Type the company name and specify an Added since date to get the most recently added domains. Click Search.
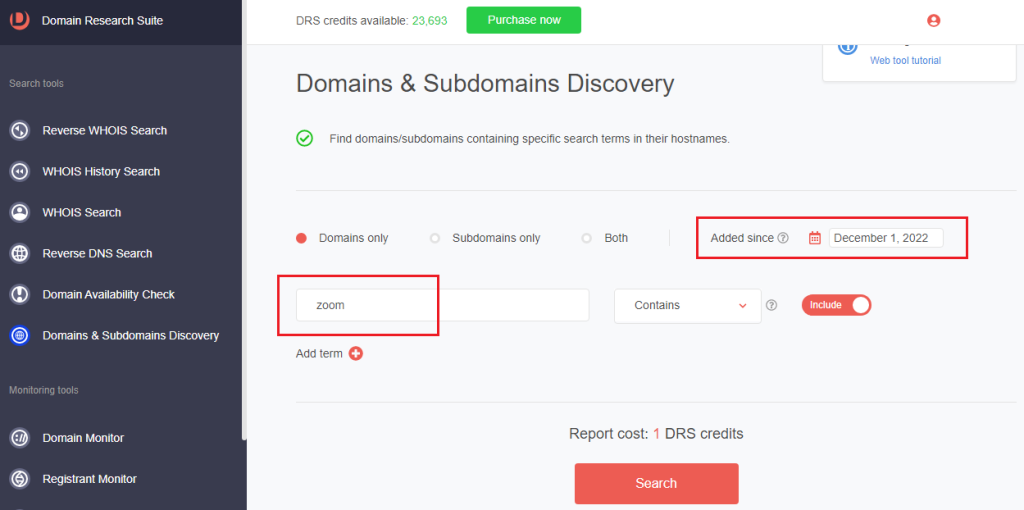
3. The tool returned 2,184 domains containing the string zoom.
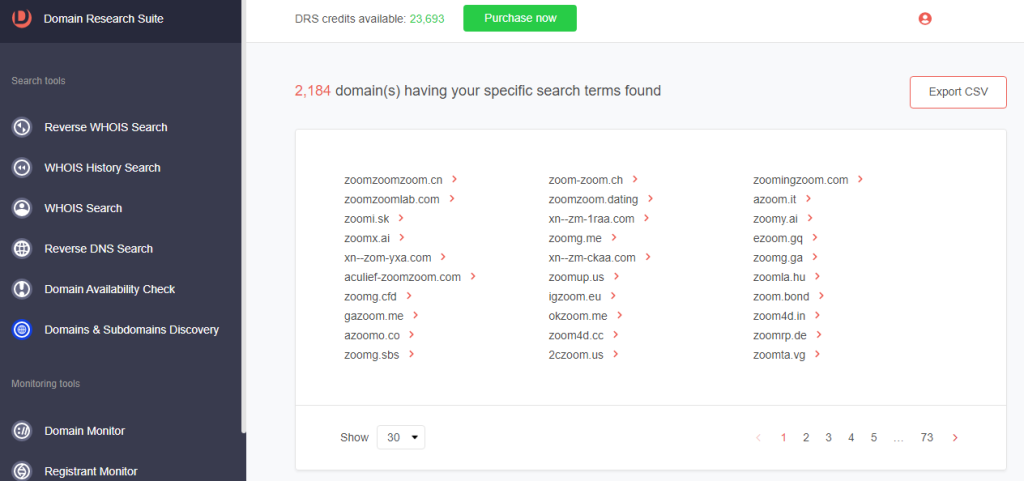
4. Click a domain name and select Build WHOIS report.
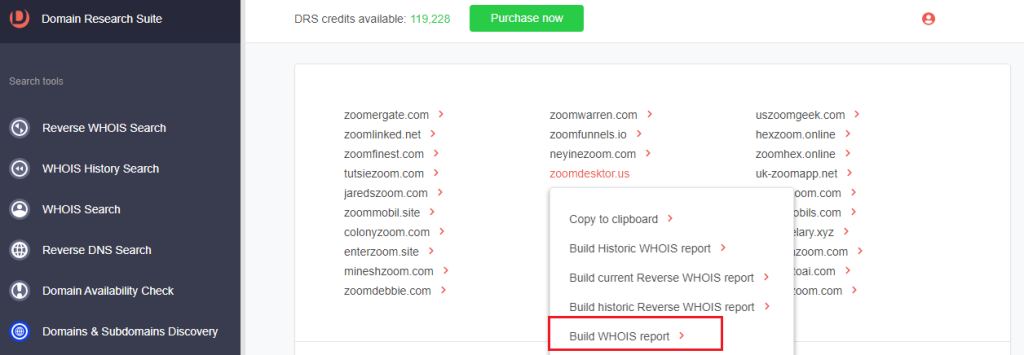
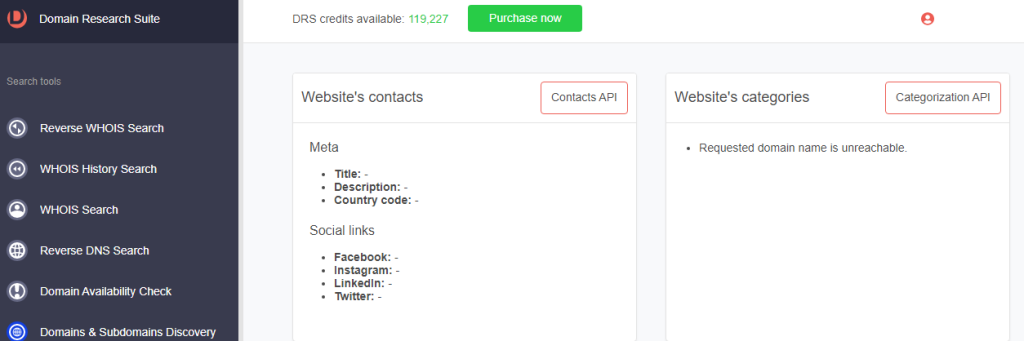
5. Examine the typosquatting domain’s WHOIS details, such as:
a. Website contacts, categorization, and meta details—which are absent in this case since the requested domain name is unreachable (i.e., the website is not live).
b. Name servers
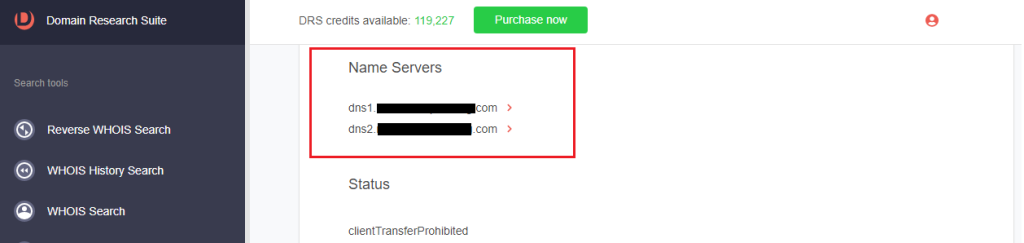
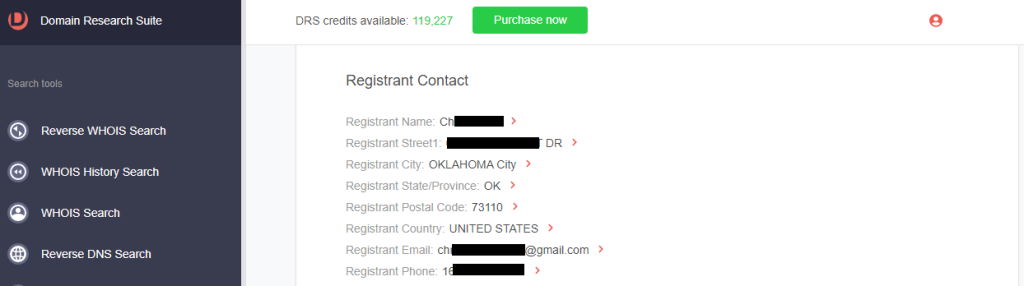
c. Registrant contact details
6. [PRO TIP] Dig deeper into the typosquatting domain’s registrant to learn more about the types of domains in their portfolio.
a. Click the registrant email.
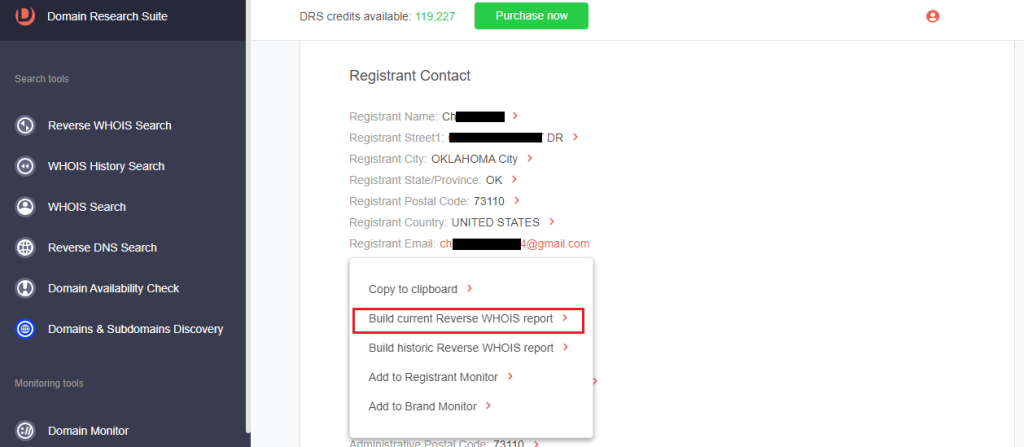
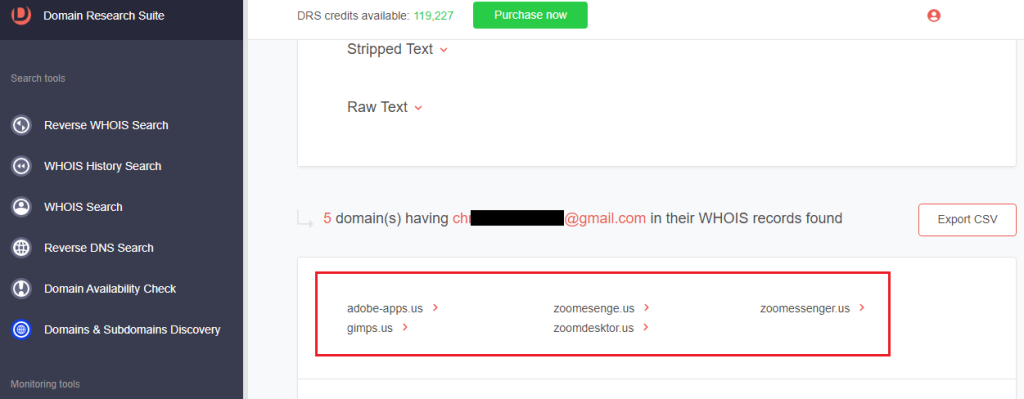
b. Select Build current Reverse WHOIS report to get a list of domains registered by the same person. The registrant currently owns other typosquatting domains targeting Zoom and Adobe.
7. Go to WHOIS Search to look up the WHOIS details of the imitated company.
8. Type the official domain. For this demonstration, that’s zoom[.]com.
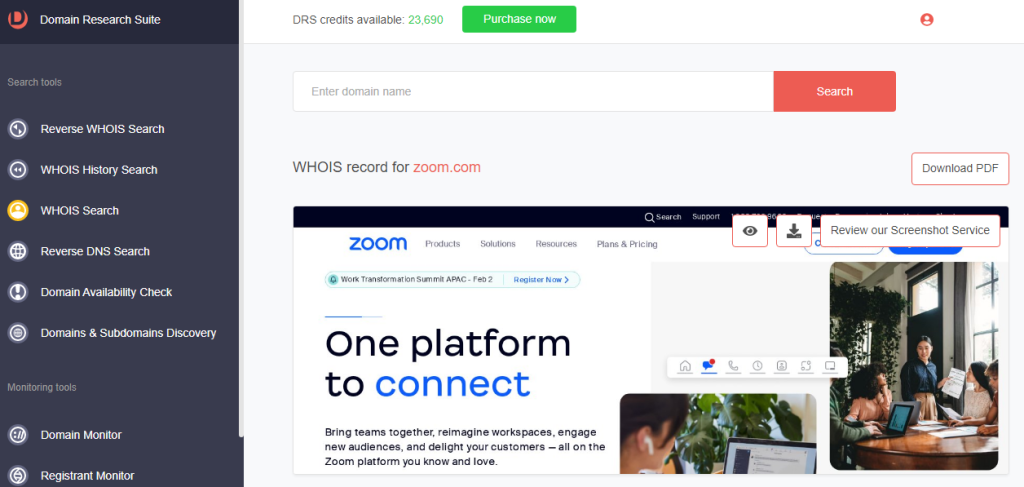
9. Examine the legitimate domain’s WHOIS details and compare them with that of the typosquatting domain.
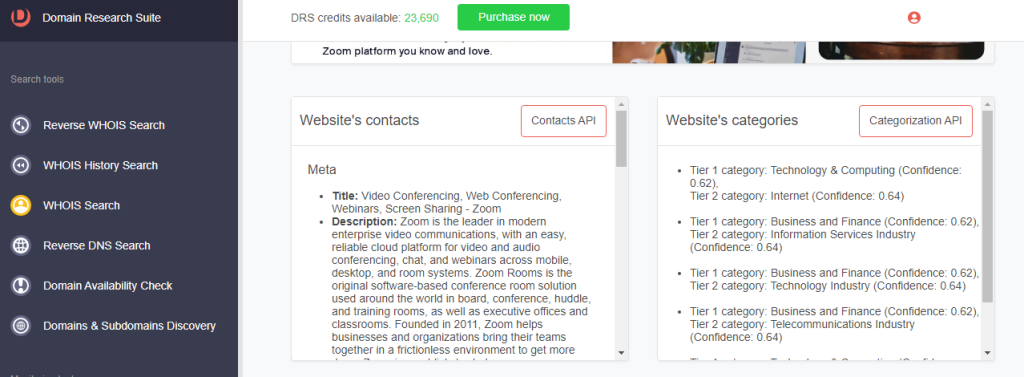
a. Website contacts, categorization, and meta details: The legitimate Zoom domain’s website contacts, categories, and meta descriptions are filled out, while the typosquatting domains’ had been left blank.
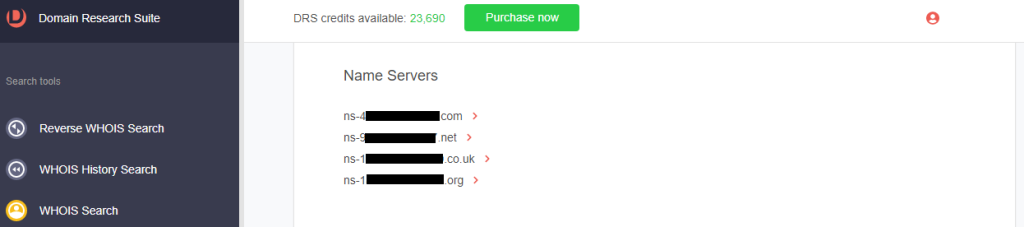
b. Name servers: The name servers of the legitimate and typosquatting domains differed.
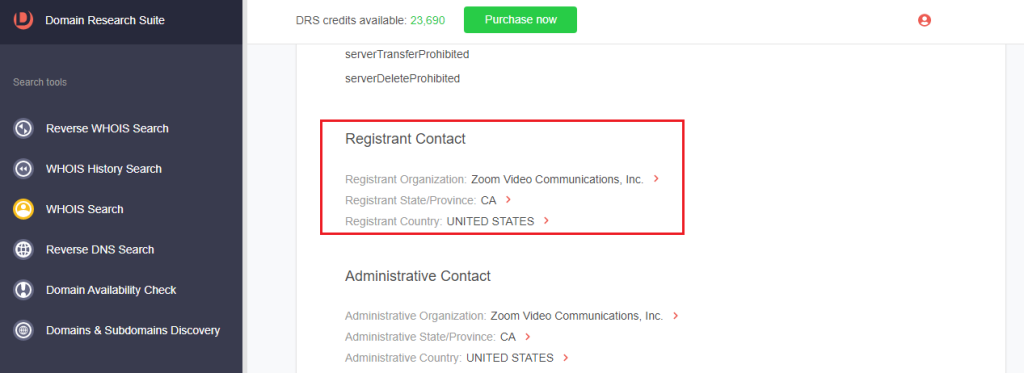
c. Registrant contact details: Zoom’s registrant organization is Zoom Video Communications, Inc., while that of the typosquatting domain was an individual.
Method #2: Uncovering Zoom-related Subdomains
Expand your search to include Zoom-related subdomains, which might be part of legitimate organizations’ configured web surface or could be compromised.
1. On Domains & Subdomains Discovery, toggle the radio button to Subdomains only.
2. Type zoom into the search field. Make sure to specify a start date to make the search more time-bound.
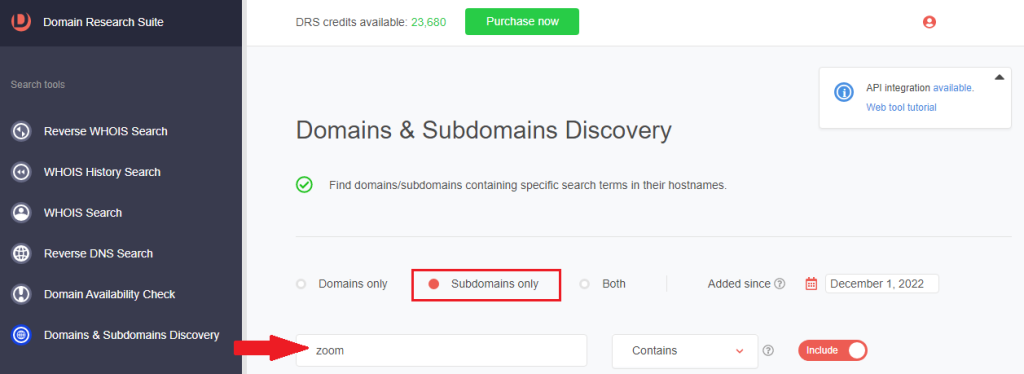
3. Between 1 December 2022 and 26 January 2023, more than 9,000 subdomains containing zoom were added.
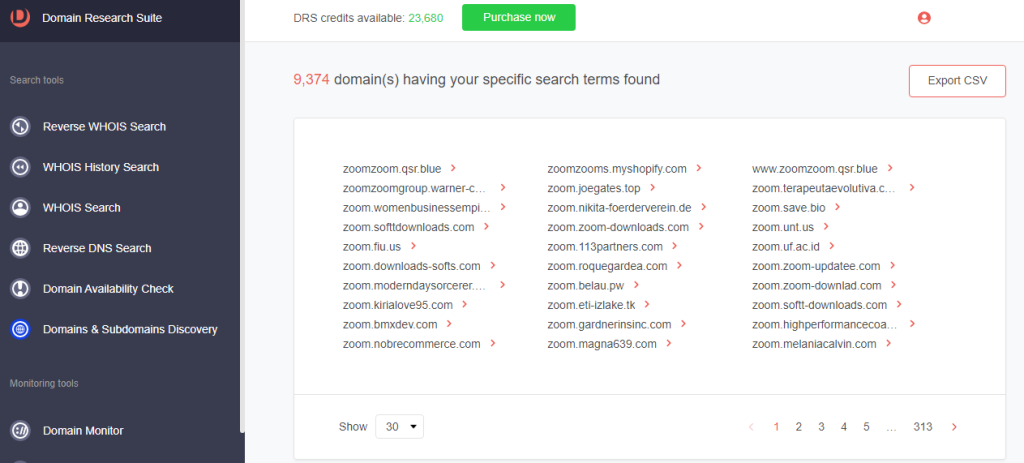
While we used Zoom to illustrate how DRS can be used to investigate attack IoCs and find additional suspicious web properties, other companies are also prime targets. DRS search and monitoring tools can help uncover and monitor typosquatting domains impersonating different entities.
Are you interested in doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.




































