Chasing Ducktail Info Stealer: A DIY Domain Research Suite (DRS) Guide to Threat Hunting
An info stealer dubbed “Ducktail” was observed targeting Facebook business accounts, particularly those using Meta’s ad platform. This edition of our DIY investigation guide will demonstrate how to investigate and build on the Ducktail IoCs for more proactive threat hunting and cybersecurity defense using different Domain Research Suite (DRS) search and monitoring tools.
Process #1: Investigating IoCs
We begin by obtaining a list of IoCs from reputable security research firms. For this investigation, we obtained domains tagged as Ducktail IoCs from WithSecure. We dove deeper into one of the domains, uncovering its WHOIS, DNS, and other Internet-related records. Follow these steps:

1. Go to WHOIS History Search and type the IoC domain into the search field. For this illustration, we focused on ductai[.]xyz.
![WHOIS History Search results for ductai[.]xyz](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/1-1024x362.png)
2. Browse through the domain’s historical WHOIS records. The tool has been tracking ductai[.]xyz for more than five years, detecting 19 historical records and three ownership detail changes.
![Tool has been tracking ductai[.]xyz for more than five years](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/2-1024x267.png)
3. Open each historical WHOIS record until you find unredacted details. The current WHOIS record of ductai[.]xyz is already protected by Domains By Proxy, LLC. However, we found unredacted registrant names, organizations, and email addresses from 2017 and 2018.
![The current WHOIS record of ductai[.]xyz is already protected by Domains By Proxy, LLC.](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/3-1024x467.png)
4. [PRO TIP] WHOIS records filed on or before 2018 (i.e., the year widespread WHOIS data redaction took place) are likely to reveal public registrant details.
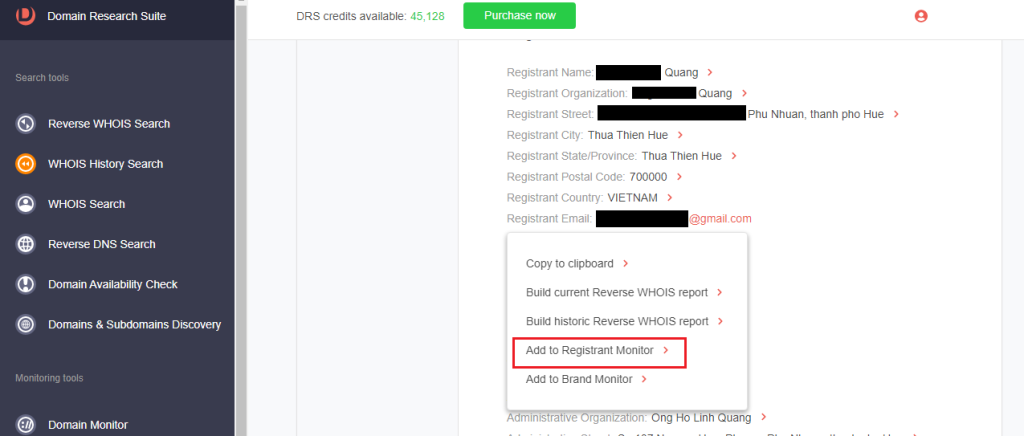
5. [PRO TIP] You can add the unredacted registrant details to Registrant Monitor by selecting a specific record and clicking Add to Registrant Monitor.
Process #2: Expanding the List of IoCs
There are two ways to find artifacts or connected domains using DRS. We demonstrate these below.
Method #1: Digging Up WHOIS-Connected Domains
Using the historical WHOIS details found during the IoC investigation, you can use Reverse WHOIS Search to look for WHOIS-connected domains. Here’s how:
1. From among the WHOIS History Search results from Process #1, click the unredacted registrant detail.
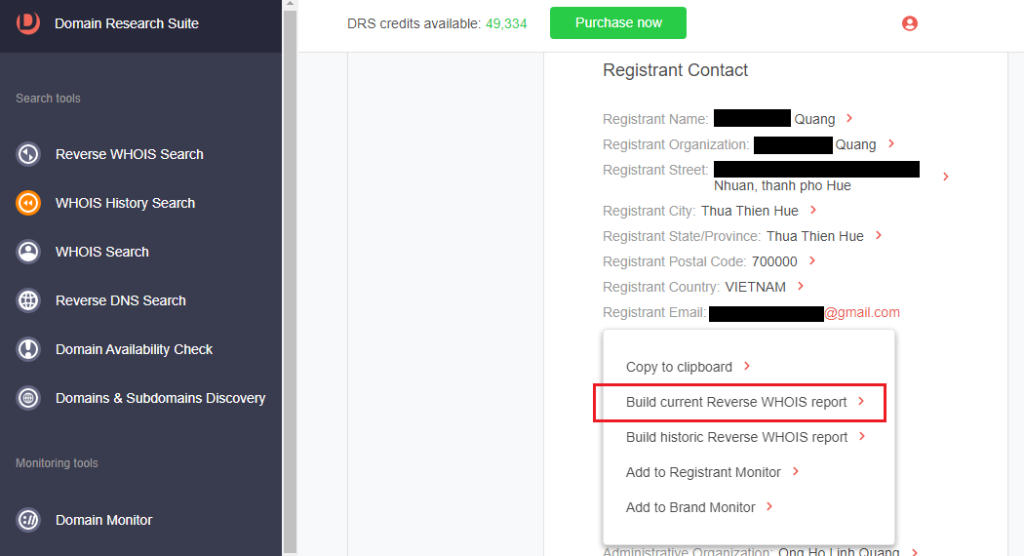
2. Select Build current Reverse WHOIS report. This action will return domain names whose current WHOIS details contain the registrant data. For the email address tied to ductai[.]xyz, we found seven connected domains.
![For ductai[.]xyz, we found seven connected domains](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/2-1-1024x527.png)
3. [PRO TIP] Choose Build historic Reverse WHOIS report to broaden the expansion and include all domains registered by the registrant at one point. We found 17 domains historically connected to ductai[.]xyz.
![ductai[.]xyz, we found seven connected domains](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/3-1-1024x480.png)
4. Alternatively, you can go to Reverse WHOIS Search and use a combination of search terms.
5. Go to Advanced Search and toggle the In specific WHOIS fields radio button on.
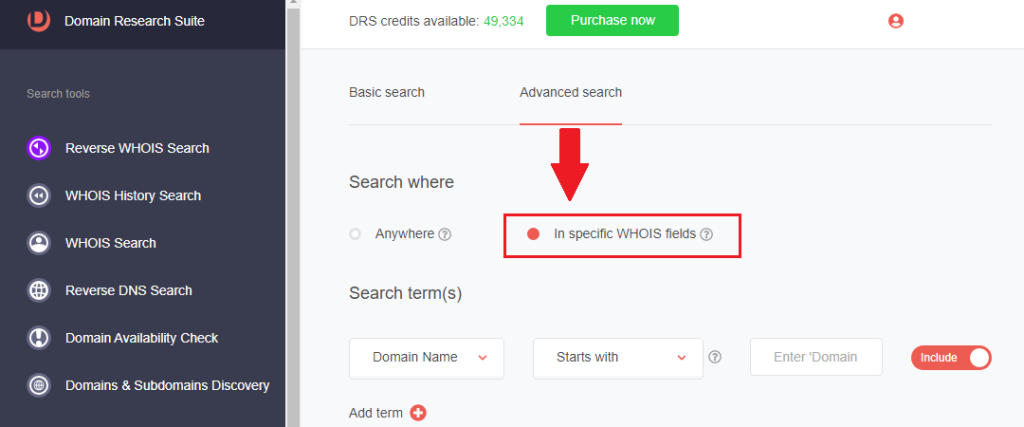
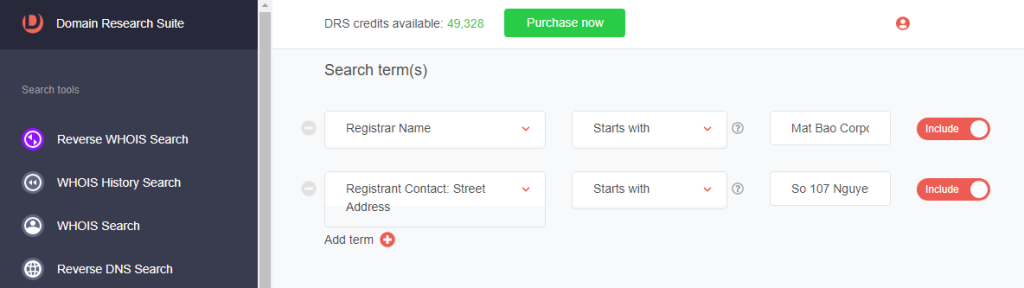
6. Select the WHOIS field and type the WHOIS detail you want to use as search terms. For instance, you can find domains sharing the IoC’s street address and registrar by specifying them under Search term(s). We found five domains using these criteria.
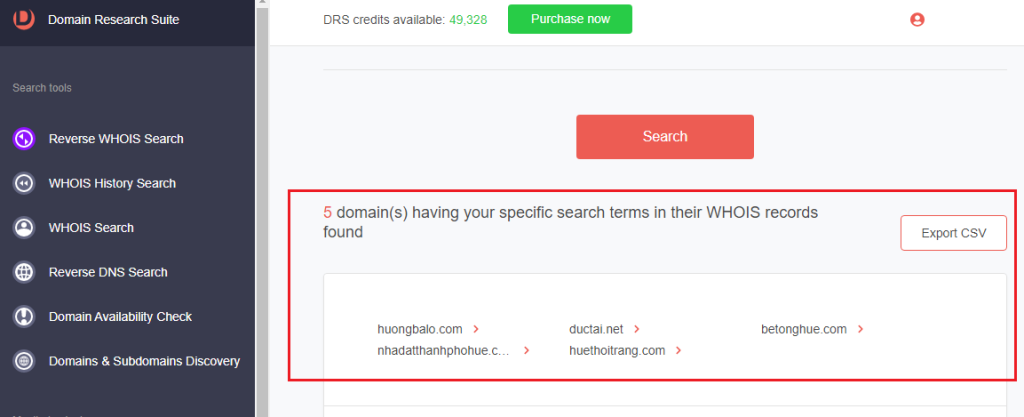
Method #2: Uncovering DNS-Connected Domains
To find domains that resolved to the same IP host identified as an IoC, follow these steps:
1. Go to Reverse DNS Search and ensure you’re on the Obtain connected domains tab.
2. Type the domain tagged as threat IoC and click Search.
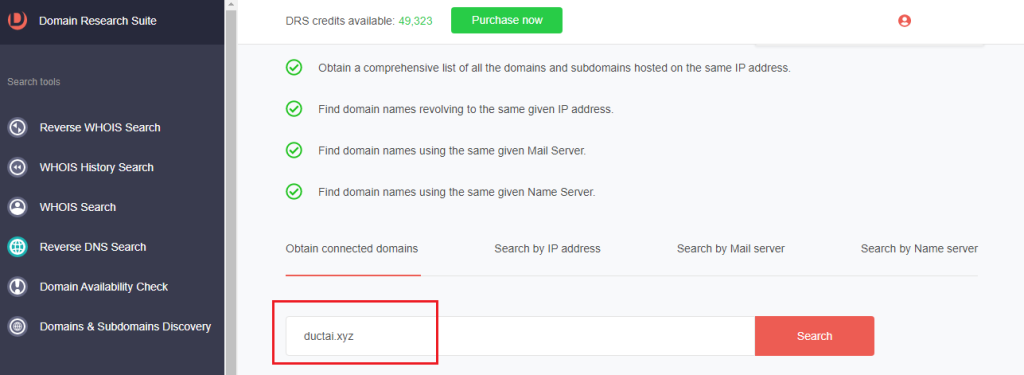
3. At least 300 domains are connected to ductai[.]xyz through their DNS resolutions.
![At least 300 domains are connected to ductai[.]xyz through their DNS resolutions](https://publishing-platform.whoisxmlapi.com/wordpress/wp-content/uploads/2023/01/2-2-1024x483.png)
4. [PRO TIP]You can zoom in on a connected domain by clicking it and selecting any of the functionalities in the pivot menu. You can Build Historic WHOIS report, Obtain connected domains, or add the domain to Domain Monitor, Registrant Monitor, and Brand Monitor.
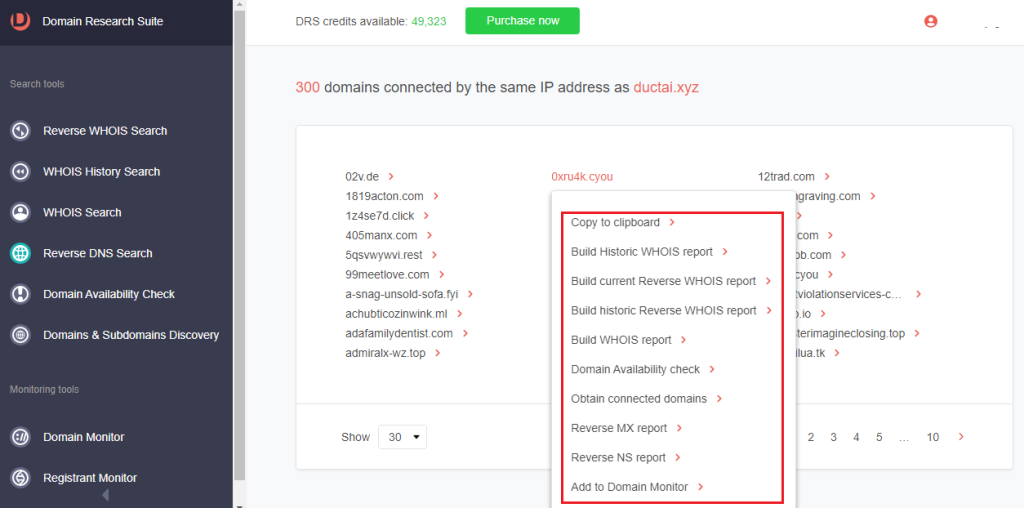
Method #3: Finding String-Connected Artifacts
You may also expand your threat hunting efforts to include web properties containing the same text strings as the threat IoCs. We illustrated how to do this below using “ducktai” as it was the string found on two domains tagged as Ducktail IoCs.
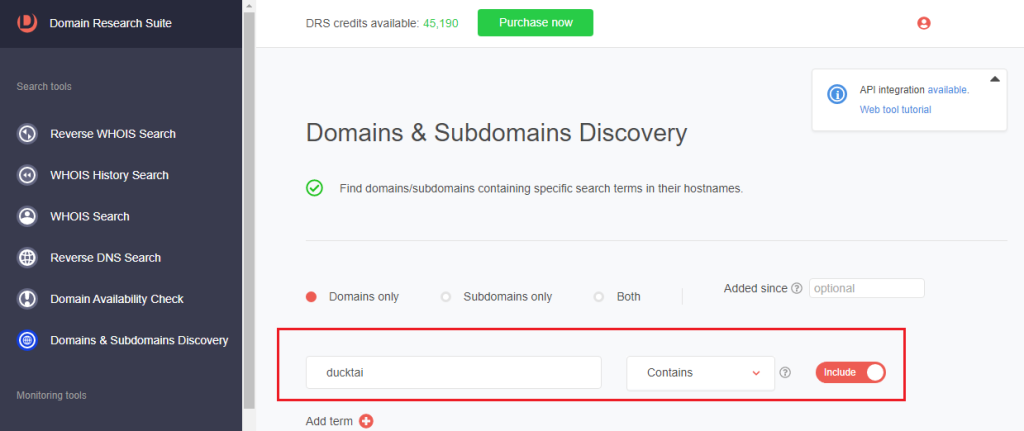
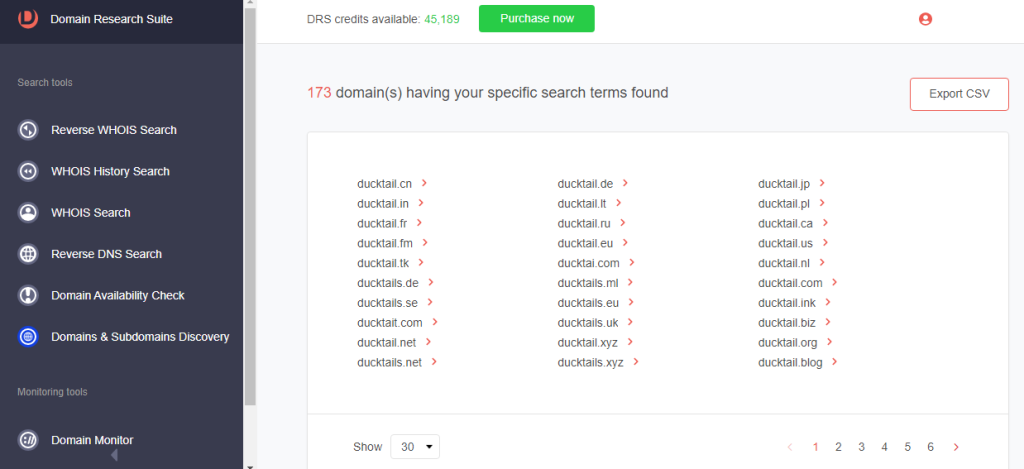
1. Go to Domains & Subdomains Discovery.
2. Toggle the Domains only radio button on.
3. Type the search string into the search box. Select the string placement parameter (i.e., Starts with, Ends with, Contains, or Exact match). DRS returned 173 domains containing “ducktai” as a string.
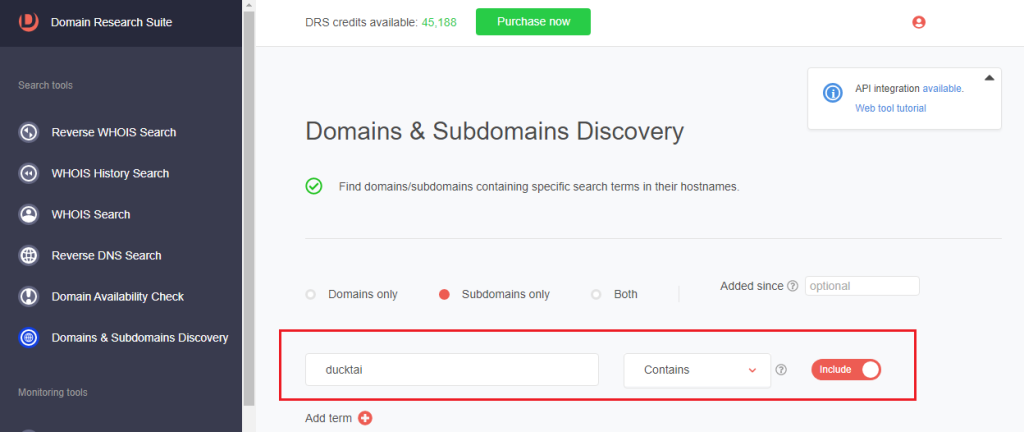
4. Toggle the Subdomains only radio button on to look up subdomains containing the search string.
5. Type the string into the search box, select the string placement parameter, and hit Enter. DRS returned 153 subdomains containing “ducktai” as a string.
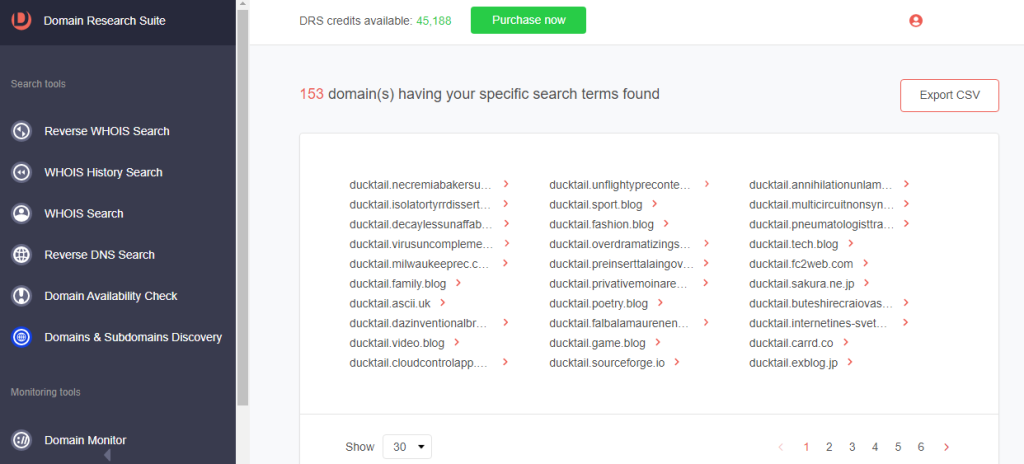
6. [PRO TIP] You may set an Added since parameter to make the search time-bound. This will return all domains or subdomains matching the search criteria added since the specific date you indicated.
Process #3: Monitoring Ducktail
DRS has monitoring tools that allow you to follow the domain footprints of threat IoCs and artifacts. To do that, follow the steps below.
Monitoring Threat Actors’ Domain Registration Activities
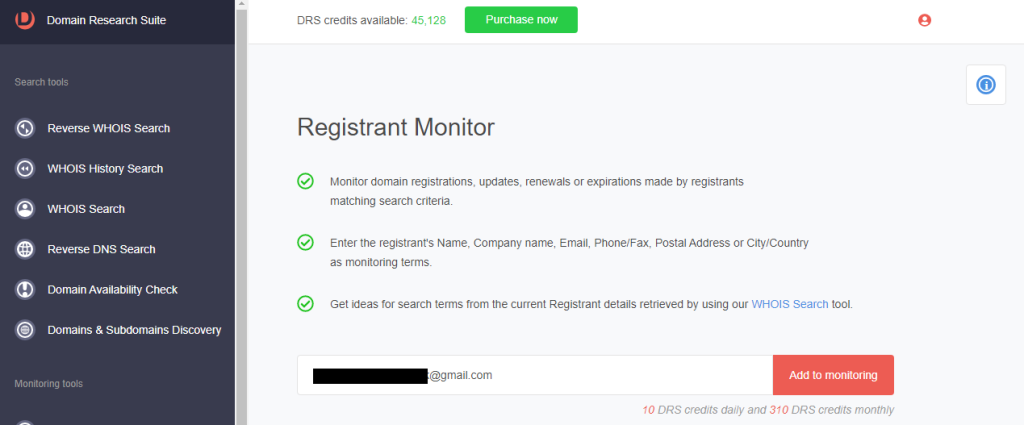
1. Go to Registrant Monitor.
2. Type an email address, an organization name, or a person’s name related to the threat into the search box and click Add to monitoring. WithSecure published more than a thousand email addresses tagged as Ducktail IoCs. These can be added to the Registrant Monitor so you can get alerted when the threat actors register a domain name.
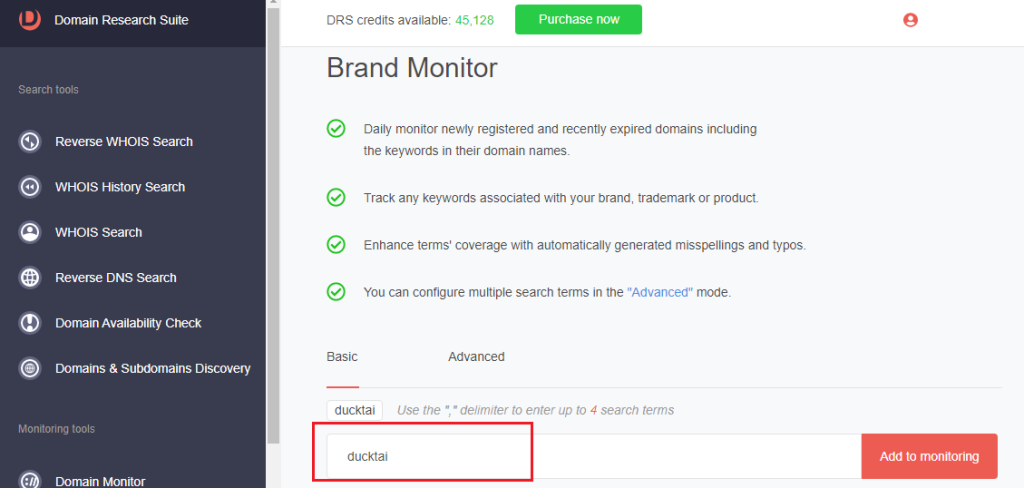
Monitoring Possible Artifacts
1. Go to Brand Monitor.
2. Type the common text string found among the IoCs and click Add to monitoring. This will alert you to newly added, updated, and expired domains containing the search string.
—
The processes involved in investigating and expanding the Ducktail IoCs shown above are also applicable to any threat. DRS search and monitoring tools enable you to track threat actors and IoCs on your own.
Are you interested in doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.




































