Finding Traces of the 2024 Most-Phished Brands in the DNS with the Domain Research Suite
Phishing is one of the oldest threats to date, but there’s a reason it’s still around—it works. AAG recently updated the 2024 Phishing Statistics report, which revealed that Google blocks around 100 million phishing emails daily. Why is that?
Users get tricked into opening phishing emails, notably because the threat actors behind them use realistic domains that closely resemble those belonging to the world’s most popular brands. The latest AAG phishing report looked deeper into five of the most-phished brands—LinkedIn, DHL, Google, Microsoft, and FedEx—which the WhoisXML API research team decided to follow up on.
Specifically, we will scour the DNS for more signs of phishing campaigns that may be cybersquatting on the top 5 brands, how many of the brand-containing domains belong to the companies being spoofed, and who may be behind the suspicious properties.
We’ll also look for potential cybersquatters or intellectual property rights violators. Finally, we’ll show you how to protect against phishing, cybersquatting, and intellectual property rights violations. We’ll do all that with the help of the Domain Research Suite (DRS).
Let’s dig in.
Process #1: What Other Domains Could Be Cybersquatting on the 5 Most-Phished Brands?
Looking for domains and subdomains that could be mimicking the five most-phished brands of 2024—LinkedIn, DHL, Google, Microsoft, and FedEx—is possible with the help of Domains & Subdomains Discovery.
Here’s a step-by-step guide you can follow if you wish to conduct a similar investigation.
- Look for the legitimate domains of the most-phished companies. Consult the table below for the list. We’ll use it to determine what text strings to use for our searches.
| TOP 5 BRANDS | LEGITIMATE DOMAINS | TEXT STRINGS |
| linkedin[.]com | linkedin. | |
| DHL | dhl[.]com | dhl. |
| google[.]com | google. | |
| Microsoft | microsoft[.]com | microsoft. |
| FedEx | fedex[.]com | fedex. |
- Access the Domains & Subdomains Discovery dashboard at https://tools.whoisxmlapi.com/domains-subdomains-discovery. For the purpose of this demonstration, we will limit the results to domains created on 1 January 2024 onward using the Starts with parameter. To do that, tick the circle next to Domains only. Choose January 1, 2024 in the Added since calendar. Type the text string you wish to use in the Included search term box. Leave the Starts with and Include parameters as is. Leaving the Include parameter on will include misspelled variants among the results. Click the Search button.
- The results will tell you how many domains start with the specific text string. Download the results in comma-separated values (CSV) format by clicking the Export CSV button. Save the results on your computer. Repeat this step for the four other text strings.
- We uncovered 116 domains in total—12 linkedin. domains, 28 dhl. domains, 53 google. domains, 18 microsoft. domains, and five fedex. domains.
- Next, using the same parameters—Added since January 1, 2024; Starts with; and Include—but tick Subdomains only this time, type each text string shown in the table above into the Included search term box. Click the Search button.
- The results will tell you how many subdomains start with the specific text string. Download the results in CSV format by clicking the Export CSV button. Save the results on your computer. Repeat this step for the four other text strings.
- We uncovered 2,772 subdomains in all—92 linkedin. subdomains, 936 dhl. subdomains, 869 google. subdomains, 864 microsoft. subdomains, and 11 fedex. subdomains.
- To find out how many of the digital properties belong to the organizations possibly being mimicked, go to the WHOIS Search dashboard at https://tools.whoisxmlapi.com/whois-search. First, let’s retrieve the WHOIS record details of the target companies. Do that by typing the legitimate domain in the Enter domain name box then click the Search button.
- Take note of the registrant details—registrant name and/or registrant organization— if any of them is public and identifiable. You can download the results in PDF also by clicking the Download PDF button. Do the same for the four other legitimate domain names.
| TOP 5 BRANDS | LEGITIMATE DOMAINS | REGISTRANT EMAIL ADDRESSES | REGISTRANT ORGANIZATIONS |
| linkedin[.]com | hostmaster@linkedin[.]com | LinkedIn Corporation | |
| DHL | dhl[.]com | domains@deutschepost[.]de | Deutsche Post AG |
| google[.]com | / | Google LLC | |
| Microsoft | microsoft[.]com | admin@domains[.]microsoft | Microsoft Corporation |
| FedEx | fedex[.]com | hostmaster@fedex[.]com | FedEx Corporate Services, Inc. |
- Now that you have those details, perform WHOIS searches for each domain in the Domains & Subdomains Discovery CSV files you downloaded earlier. You’ll find out, for example, that linkedin[.]pa belongs to LinkedIn since it shares linkedin[.]com’s registrant email address. The domain linkedin[.]world, meanwhile, probably does not since it has no public registrant details.
Screenshot of WHOIS record details of linkedin[.]world |
- The WHOIS searches revealed that only 18 of the 116 domains are recorded as owned by the five most-phished brands. Specifically:
- Only two linkedin. domains are seemingly owned by LinkedIn.
- None of the dhl. domains are seemingly owned by DHL.
- Twelve google. domains are seemingly owned by Google.
- Only three microsoft. domains are seemingly owned by Microsoft.
- Only one fedex. domain is seemingly owned by FedEx.
- The WHOIS searches may also reveal who owns the brand-containing domains that aren’t part of the most-phished companies’ network infrastructure. In this case, for instance, we discovered that linkedin[.]gy belongs to another organization and had a public registrant name and email address in its WHOIS record. While it may not necessarily be cybersquatting, its owner may not have the right to use the LinkedIn brand. If that’s the case, LinkedIn may contact the registrant so he/she can take the necessary actions.
- Should a domain owner be involved in any unlawful or malicious activity and you want to see if he/she owns other domains that could end up getting used in attacks, you can count on Reverse WHOIS Search. Access its dashboard at https://tools.whoisxmlapi.com/reverse-whois-search. Let’s see if linkedin[.]gy’s registrant email address appears in the WHOIS records of other domains. Click Advanced search and tick In specific WHOIS fields. Under Search term(s), choose Registrant Contact: Email and Exact match from the drop-down menus, type the email address in the input box, and leave the Include, Current, and Date filters parameters as is. Then hit the Search button.
- The query provided us with 12 domains that had the registrant email address in their current WHOIS records. You can download the results in CSV format by clicking the Export CSV button.
Process #2: How Can You Find Domains That Could Be Cybersquatting on Your Brand?
Now, let’s say that you’re assessing the security of your corporate network. One critical step in that is cataloging all your digital assets with the help of DRS.
- Domains & Subdomains Discovery can help. You can look for domains and subdomains with the same name as your organization using your domain name as a search term. Follow the same steps specified in process #1 but instead of limiting the results, don’t indicate an Added since date.
- We found 383 domains and 6,550 subdomains.
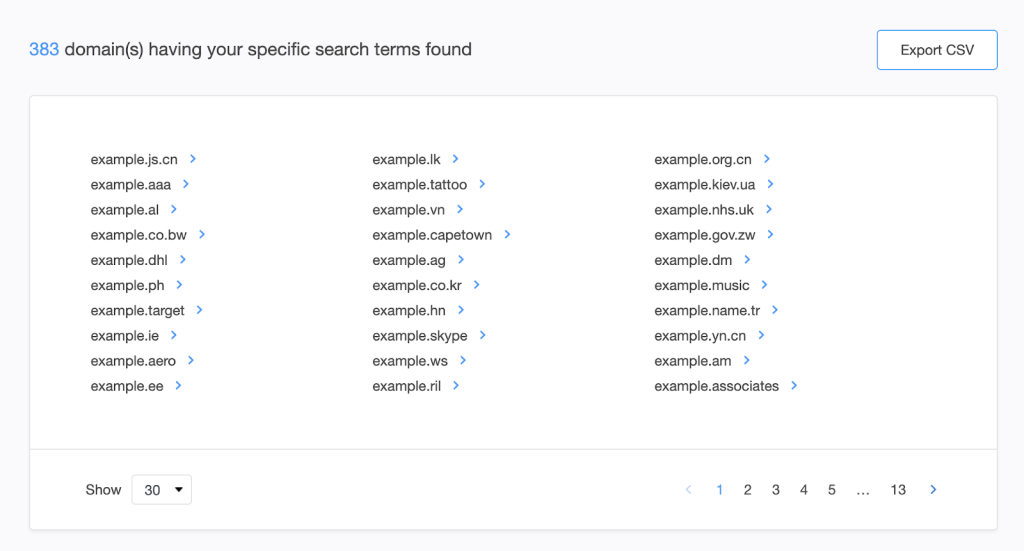
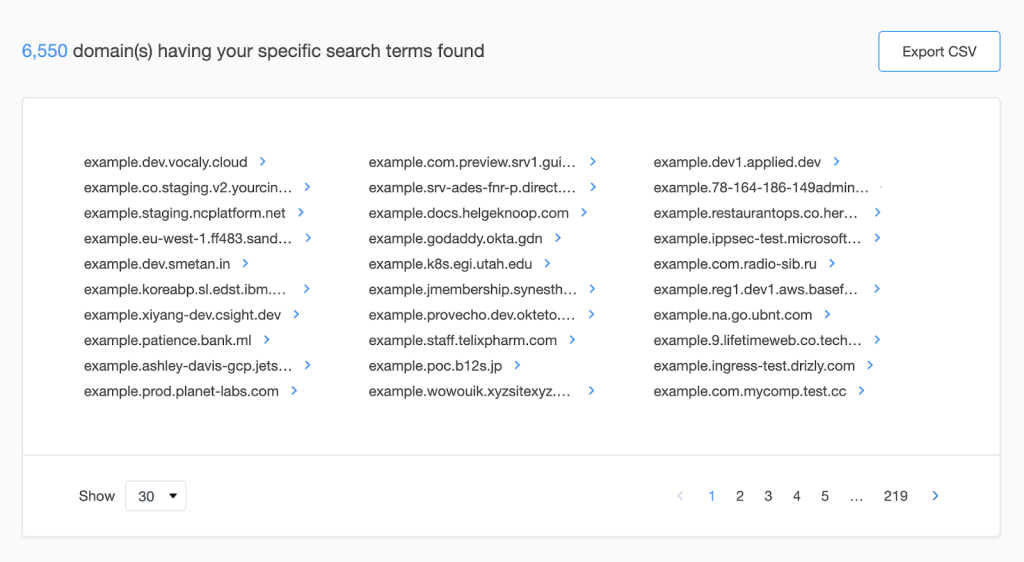
- You can then do WHOIS record comparisons for your domain name and the brand-containing domains using WHOIS Search by following the same steps outlined in process #1.
- You can also determine the owners of some of the domains if their WHOIS records have public information. You can use the data to file a domain abuse complaint with the Internet Corporation for Assigned Names and Numbers (ICANN) or a case with a law enforcement agency if they turn out to be malicious.
Process #3: How Can You Continuously Protect Your Brand and Digital Properties against Cybersquatting?
You can monitor the DNS continuously for signs of cybersquatting, phishing, or copyright infringement with Domain Monitor and Brand Monitor.
Ready to take the step toward better brand health? Follow these instructions.
- To help ensure that no registrant will abuse your brand through misappropriated domain names, access the Brand Monitor dashboard at https://tools.whoisxmlapi.com/brand-monitor. Click Advanced if you wish to include misspelled variations in your monitoring. Enter the name of the brand, product, or service you want to watch out for in the Included search term box, toggle the Typos button to on, and click + beside Add term. Do the same for all names you wish to monitor. Click the Add to monitoring button.
- You should now see the monitor in the active monitors list. You’ll receive the first notification stating how many and what domains containing the brand, product, or service name were created after 24 hours. You can get daily alerts as well so long as the monitor is active.
- Here is the result of your brand monitoring after 24 hours.
- To help ensure no registrant abuses your domain, meanwhile, access the Domain Monitor dashboard at https://tools.whoisxmlapi.com/domain-monitor. We’ll use a single domain for this demo using the Add one domain parameter but you can monitor domain names in bulk as well via the Add domains in Bulk parameter. Type the domain you wish to monitor in the Enter domain name box and click the Add to monitoring button.
- You should now see the monitor in the N domains are monitored list. You’ll receive the first notification stating how many and what domains containing the domain name were created after 24 hours. You can get daily alerts as well so long as the monitor is active.
- You can then get the results of your domain monitoring after 24 hours.
—
Phishing and impersonation are indeed global problems and they aren’t going away anytime soon. But there are ways to avoid attacks and detect unlawful activities with the help of easy-to-use web-based solutions like DRS.
Are you interested in protecting your brand from cybersquatting or doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.




































