Finding Traces of Business and CEO Impersonators: A DIY DRS Guide to Business and CEO Impersonation Vector Identification
Business and Chief Executive Officer (CEO) impersonation have become a multibillion-dollar industry. They are, in fact, two of the most common types of phishing employed today.
In this edition of our DIY investigation guide, we will demonstrate how companies and their security teams can detect potential business and CEO impersonation scam vectors in the DNS using the Domain Research Suite (DRS) search and monitoring tools.
Process #1: Finding Potential Fortune 500 Company Impersonators
To reap the biggest profit possible from a business email compromise (BEC) scam, attackers typically spoof a target organization’s supplier or business partner using a domain that looks as close as possible to that of the third party.
Guess what? Impersonating a Fortune 500 company that works with thousands of organizations worldwide is thus bound to be very lucrative for BEC scammers. Let’s take a deep dive into the DNS to find domains and subdomains potentially cybersquatting on the popularity of 20 Fortune 500 companies.
Step #1: Looking for Domains and Subdomains Containing the Names of Fortune 500 Companies
For this step, we chose 20 Fortune 500 companies that BEC scammers could impersonate for their campaigns. We listed them, along with their official website domains and the strings we used on Domains & Subdomains Discovery as search terms, below.
| FORTUNE 500 COMPANY | OFFICIAL WEBSITE DOMAIN | DOMAINS & SUBDOMAINS DISCOVERY SEARCH TERM |
| Exxon Mobil | exxonmobil[.]com | exxonmobil |
| UnitedHealth Group | unitedhealthgroup[.]com | unitedhealthgroup |
| CVS Health | cvshealth[.]com | cvshealth |
| AmerisourceBergen | amerisourcebergen[.]com | amerisourcebergen |
| Costco Wholesale | costco[.]com | costco |
| Cigna Group | cignaglobal[.]com | cignaglobal |
| Marathon Petroleum | marathonpetroleum[.]com | marathonpetroleum |
| Phillips 66 | phillips66[.]com | phillips66 |
| Valero Energy | valero[.]com | valero |
| Centene | centene[.]com | centene |
| Fannie Mae | fanniemae[.]com | fanniemae |
| Target | target[.]com | target |
| Lowe’s | lowes[.]com | lowes |
| FedEx | fedex[.]com | fedex |
| Humana | humana[.]com | humana |
| Energy Transfer | energytransfer[.]com | energytransfer |
| State Farm Insurance | statefarm[.]com | statefarm |
| Freddie Mac | freddiemac[.]com | freddiemac |
| PepsiCo | pepsico[.]com | pepsico |
| Tesla | tesla[.]com | tesla |
To uncover potential Fortune 500 copycats that could have already figured in or may be waiting to get weaponized for BEC scams, follow these steps.
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only
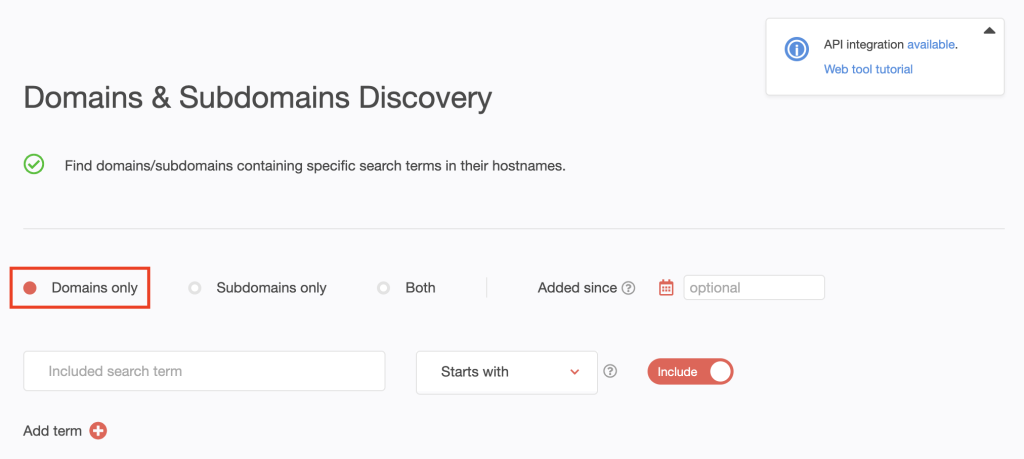
2. Type the search string for the first company on the list—exxonmobil—into the input field. Set the string placement parameter to Contains. To include possibly misspelled variations, we toggled the Include button to on.
[PRO TIP] Make your search time-bound by setting an Added since date. We used January 1, 2023.
Click Search.
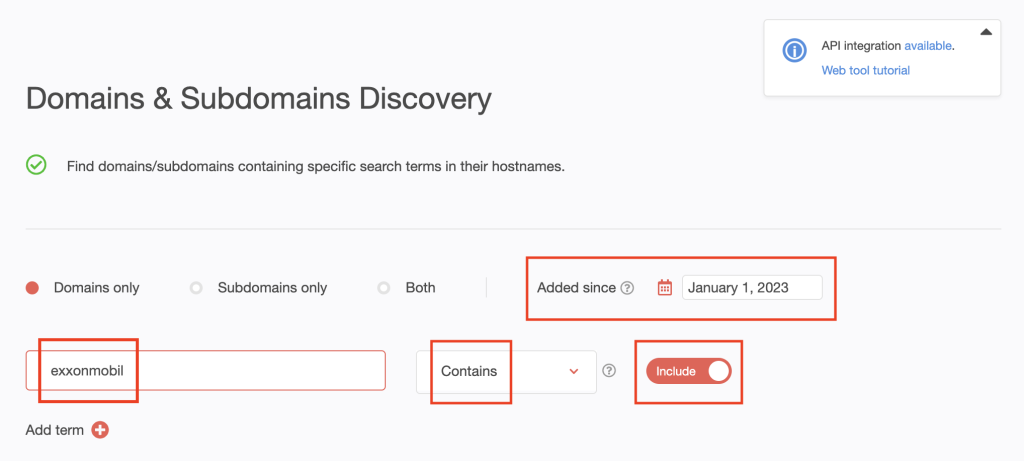
3. Our search uncovered 110 domains.
4. Repeat procedure #2 for each search string to complete your list of potential Fortune 500 cybersquatting domains. Our searches uncovered a total of 11,902 domains.
5. Now, scroll back to the top of the page. This time, choose Subdomains only.
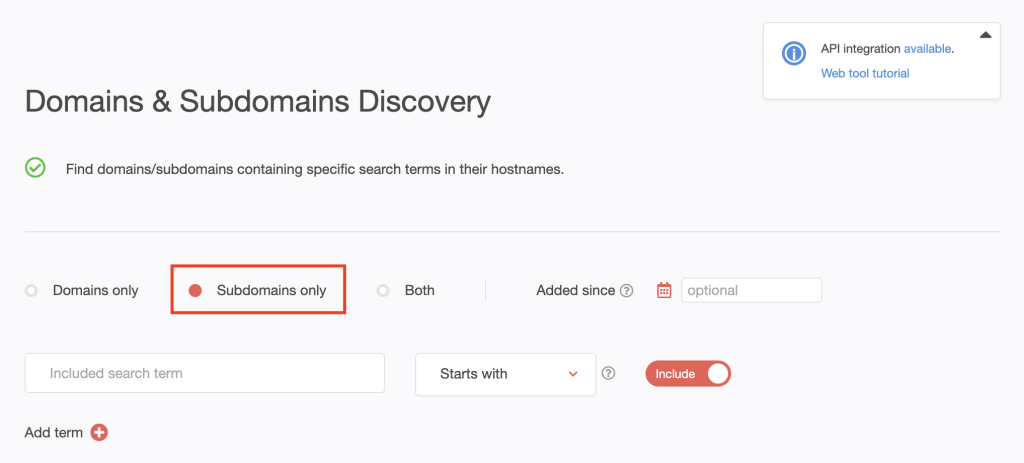
6. Type the search string for the first company on the list—exxonmobil—into the input field. Set the string placement parameter to Contains. To include possibly misspelled variations, we toggled the Include button to on.
[PRO TIP] Like we did for the domains, you can make your search time-bound by setting the Added since date to January 1, 2023.
Click Search.
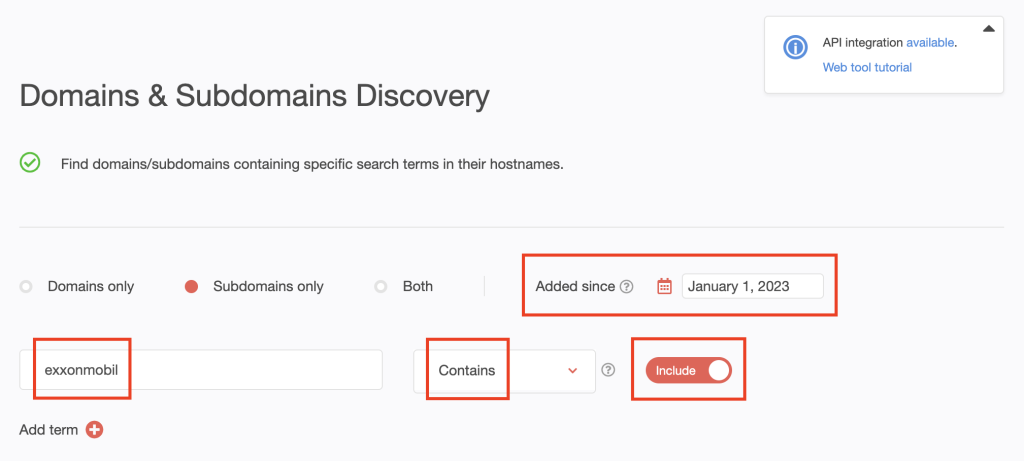
7. Our search led to the discovery of 756 subdomains.
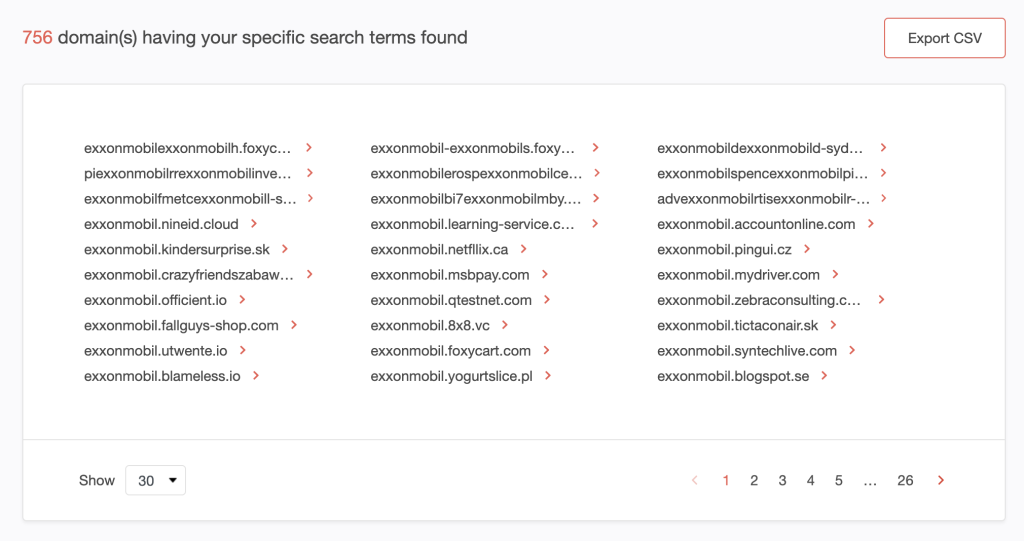
8. Repeat procedure #6 for each search string to complete your list of potential Fortune 500 cybersquatting subdomains. Our searches uncovered a total of 2,689 subdomains.
Step #2: Determining Who Owns Specific Domains and Subdomains
To know if the domains and subdomains containing the names of the 20 Fortune 500 companies on our list actually belong to the featured organizations, follow these steps.
1. Go to Domains & Subdomains Discovery. Select Domains only and type tesla into the search field. Set the string placement parameter to Contains and toggle the Include button to on.
[PRO TIP] As in the previous section, make your search time-bound by setting the Added since date to January 1, 2023.
Click Search.
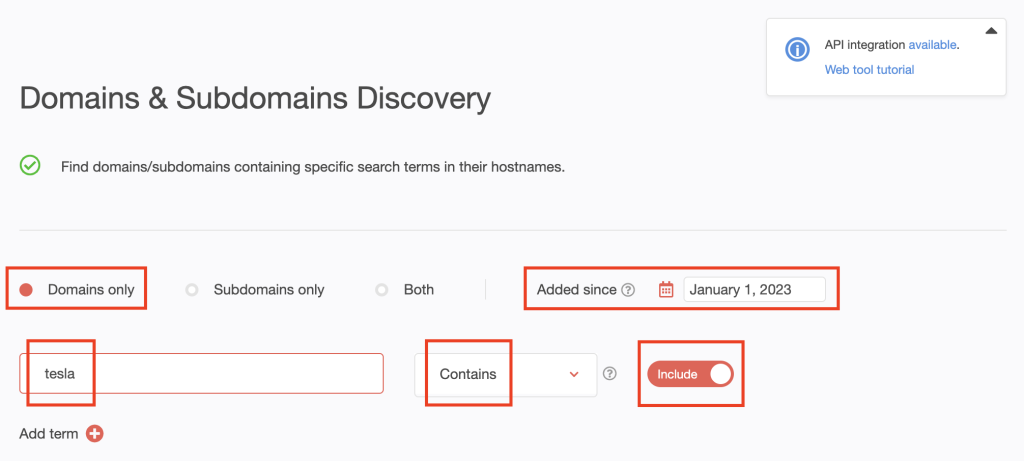
2. Our search uncovered 6,421 domains.
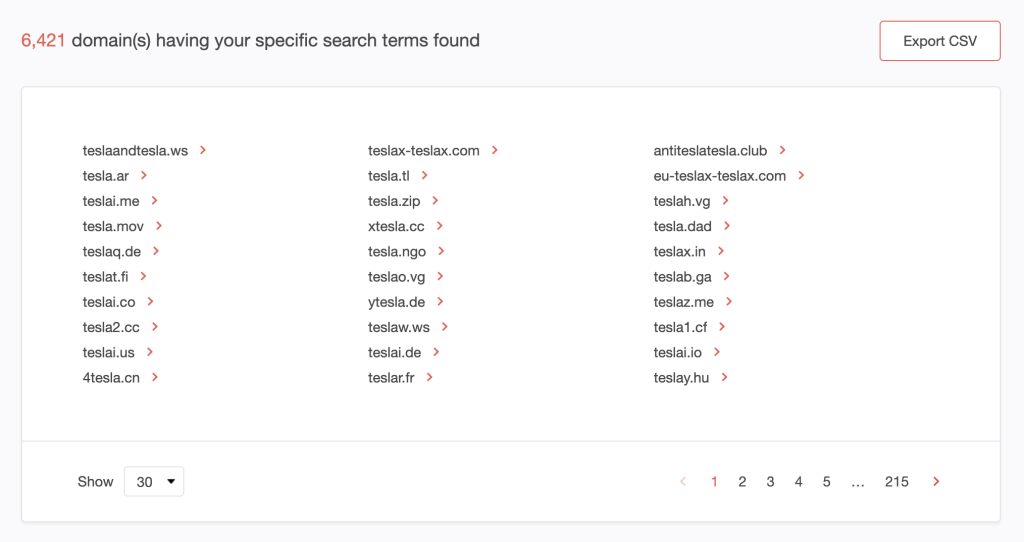
3. The domain teslagives2023[.]com on page 93 of the search results looks interesting. Why? Phishers are known for using giveaways as lures. Let’s take a closer look at it.
Click > next to the domain name to open a drop-down list.
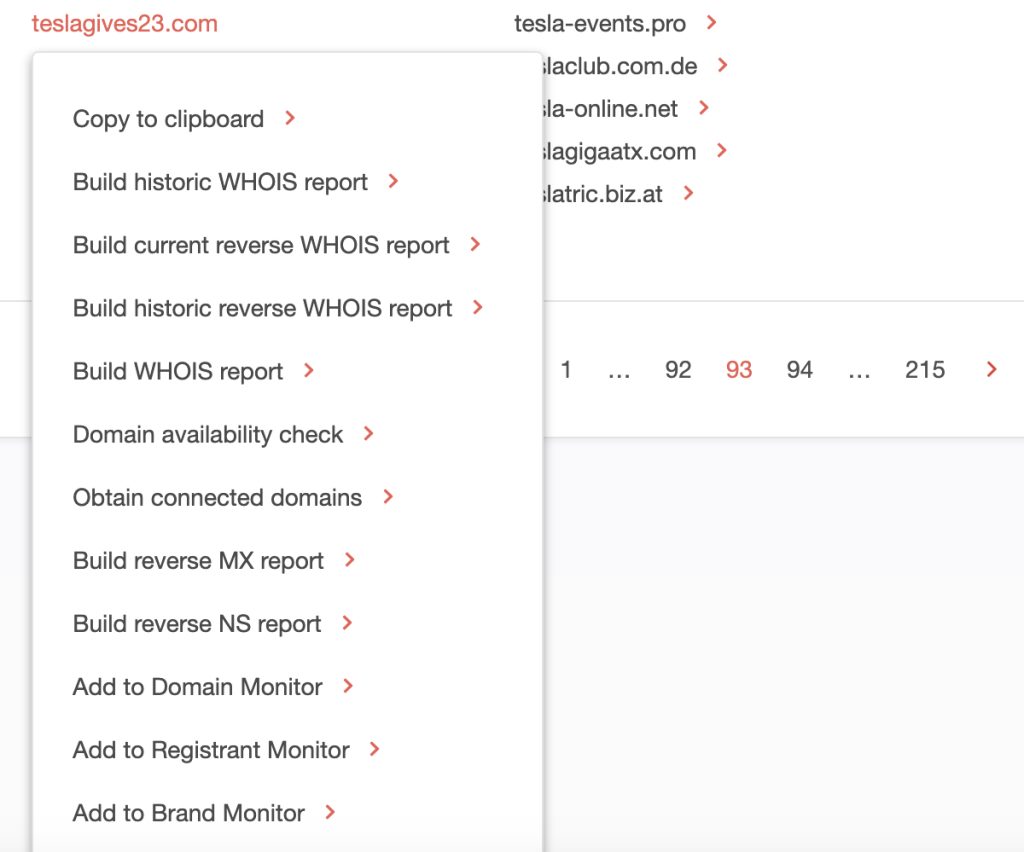
4. To determine if it could be publicly attributed to Tesla, check out its current WHOIS record by clicking Build WHOIS report. You should get the result on the left.
5. Note the differences between the current WHOIS records of the potential cybersquatter (image on the left) and Tesla’s official website domain tesla[.]com (image on the right). Focus most especially on the Registrant Email field.
Since teslagives2023[.]com doesn’t have the same registrant email address as tesla[.]com, we can say that it can’t be publicly attributed to Tesla. Translation? It most likely isn’t owned by the company.
Process #2: Discovering Potential Fortune 500 Company CEO Impersonators
Apart from BEC scams, impersonation also plays a crucial role in other nefarious activities. Impersonating famous CEOs like those of Fortune 500 companies is a must in whaling—a specialized form of phishing targeting the high-level officials or C-suites of big-named corporations. It is thus also known as “CEO fraud.”
Like BEC scams, threat actors typically register domains and subdomains containing their target C-suite’s name. Let’s take a deep dive into the DNS to find domains and subdomains potentially cybersquatting on the popularity of the CEOs of 10 Fortune 500 companies.
Step #1: Looking for Domains and Subdomains Containing the Names of Fortune 500 Company CEOs
For this step, we chose 10 Fortune 500 companies that whalers could impersonate for their campaigns. We listed them, along with their CEOs’ names and the strings we used on Domains & Subdomains Discovery as search terms, below.
| FORTUNE 500 COMPANY | CEO | DOMAINS & SUBDOMAINS DISCOVERY SEARCH TERM |
| Berkshire Hathaway | Warren Edward Buffett | warrenbuffett |
| General Motors | Mary Teresa Barra | marybarra |
| Centene | Sarah M. London | sarahlondon |
| Walgreens Boots Alliance | Rosalind G. Brewer | rosalindbrewer |
| Meta Platforms | Mark Elliot Zuckerberg | markzuckerberg |
| Dell Technologies | Michael Saul Dell | michaeldell |
| Archer Daniels Midland | Juan Ricardo Luciano | juanluciano |
| United Parcel Service | Carol B. Tomé | caroltome |
| Freddie Mac | Michael J. DeVito | michaeldevito |
| Tesla | Elon Reeve Musk | elonmusk |
To uncover potential Fortune 500 CEO copycats that could have already figured in or may be waiting to get weaponized for whaling campaigns, follow these steps.
1. Go to Domains & Subdomains Discovery. Make sure to select Domains only.
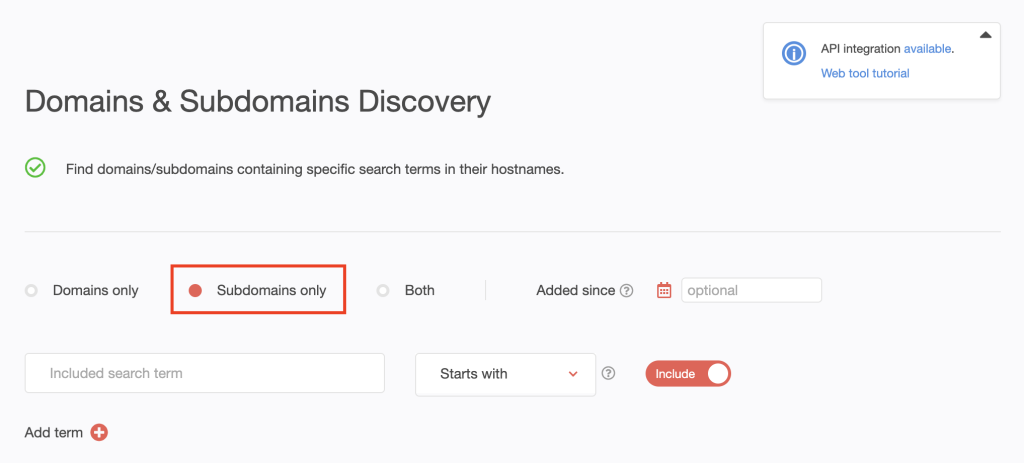
2. Type the search string for the first CEO on the list—warrenbuffett—into the input field. Set the string placement parameter to Contains. To include possibly misspelled variations, we toggled the Include button to on.
[PRO TIP] Make your search time-bound by setting an Added since date. We used January 1, 2023.
Click Search.
3. Our search uncovered 13 domains.
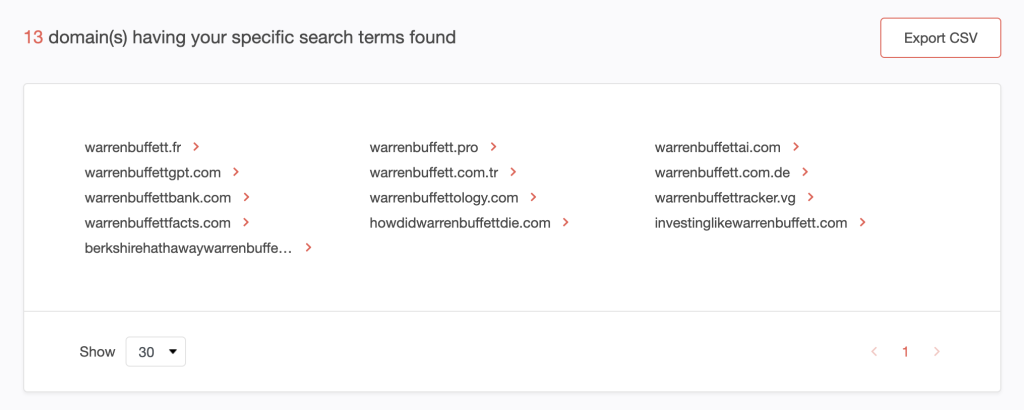
4. Repeat procedure #2 for each search string to complete your list of domains potentially riding on the popularity of our 10 Fortune 500 CEOs. Our searches uncovered a total of 311 domains.
5. Now, scroll back to the top of the page. This time, choose Subdomains only.
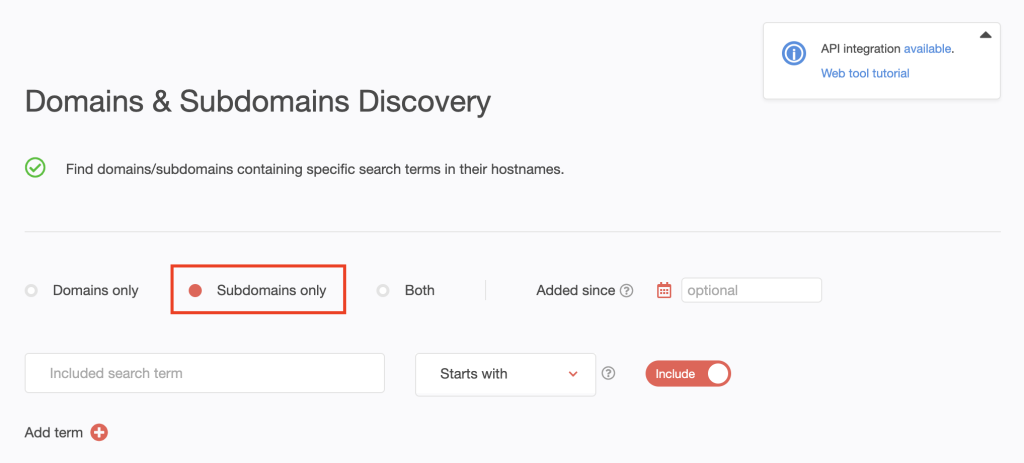
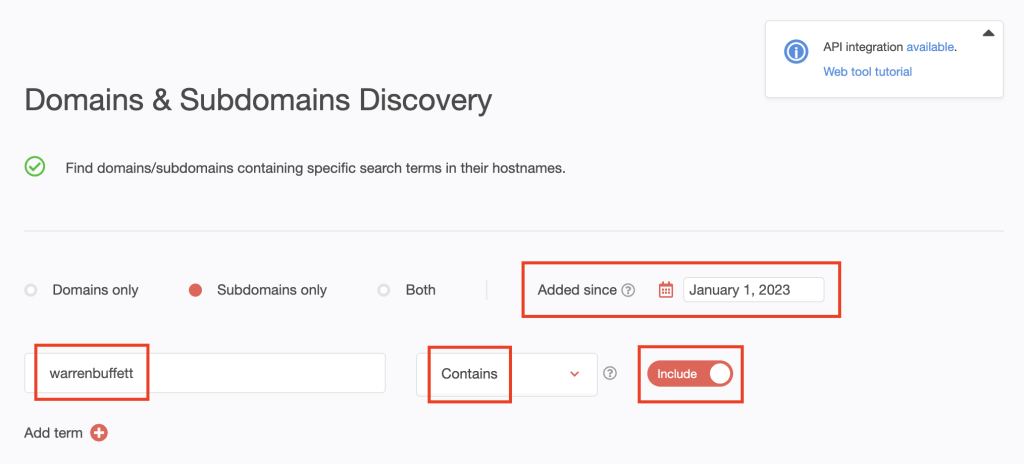
6. Type the search string for the first CEO on the list—warrenbuffett—into the input field. Set the string placement parameter to Contains. To include possibly misspelled variations, we toggled the Include button to on.
[PRO TIP] Like we did for the domains, you can make your search time-bound by setting the Added since date to January 1, 2023.
Click Search.
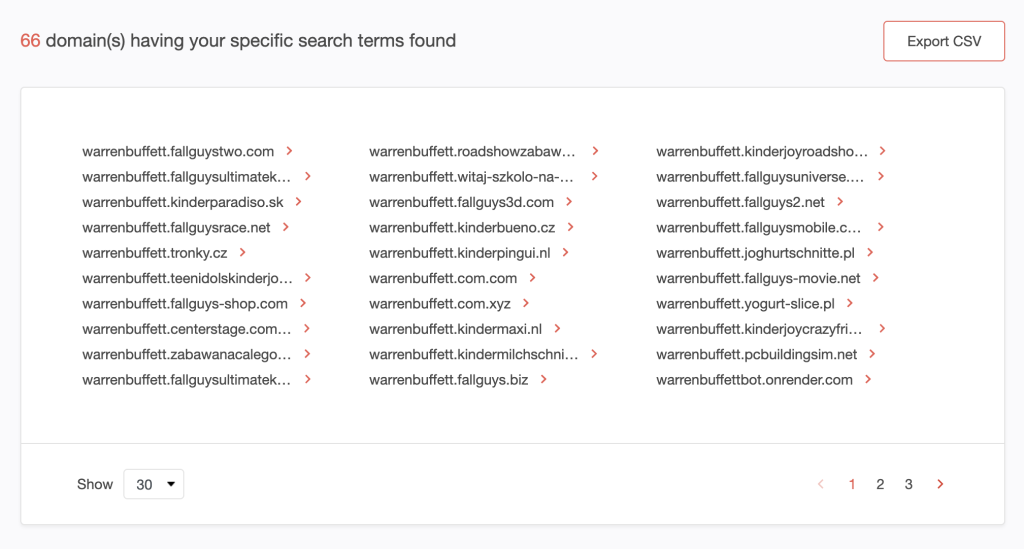
7. Our search led to the discovery of 66 subdomains.
8. Repeat procedure #6 for each search string to complete your list of potential Fortune 500 cybersquatting subdomains. Our searches uncovered a total of 388 subdomains.
Step #2: Determining Who Owns Specific Domains and Subdomains
To know if the domains and subdomains containing the names of the 10 Fortune 500 company CEOs on our list actually belong to them, follow these steps.
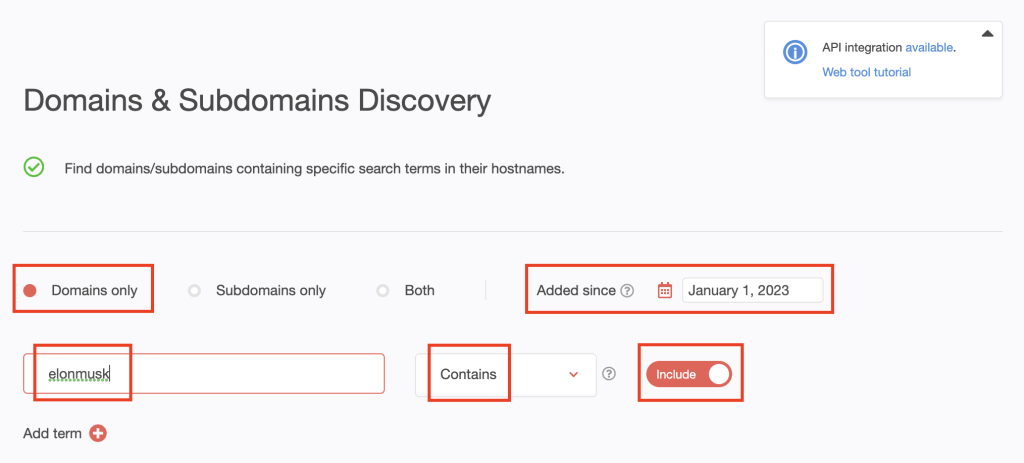
1. Go to Domains & Subdomains Discovery. Select Domains only and type elonmusk into the search field. Set the string placement parameter to Contains and toggle the Include button to on.
[PRO TIP] As in the previous section, make your search time-bound by setting the Added since date to January 1, 2023.
Click Search.
2. Our search uncovered 260 domains.
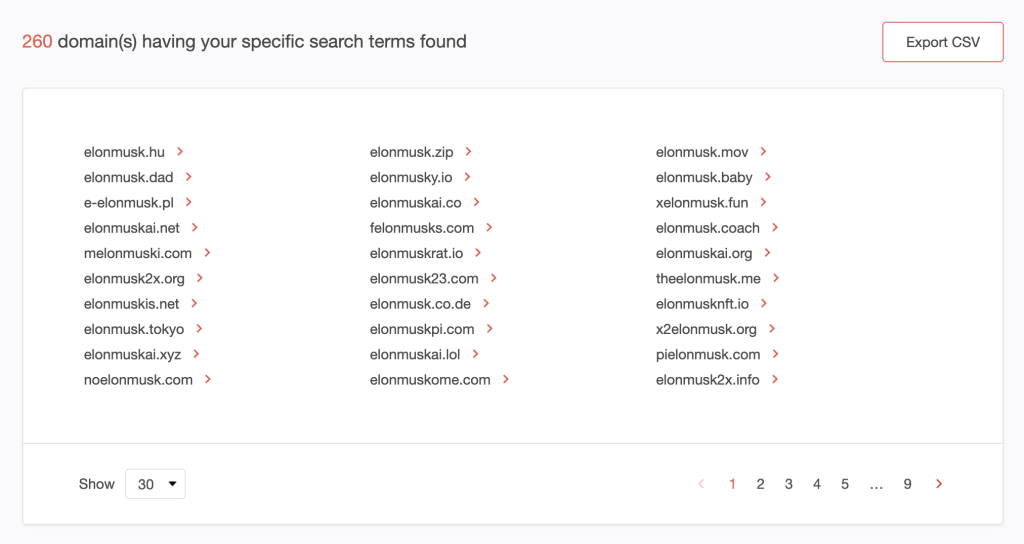
3. The domain elonmusk2x[.]org on page 1 of the search results looks harmless enough. But is it?
Click > next to the domain name to open a drop-down list.
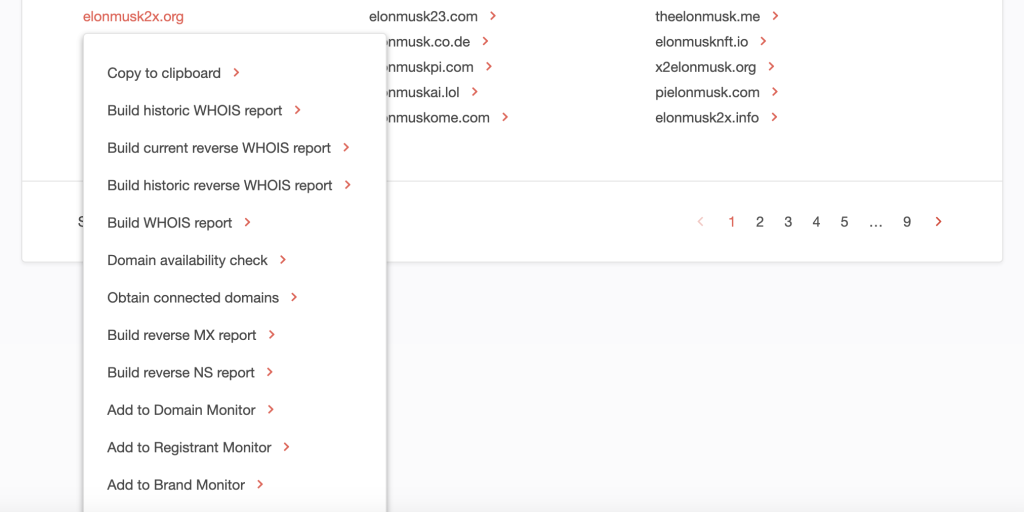
4. To determine if it could be publicly attributed to Tesla CEO Elon Musk, check out its current WHOIS record by clicking Build WHOIS report. You should get the result on the left.
5. As far as we can tell from online searches, Elon Musk doesn’t seem to have a personal website. The closest to one pertaining to his Tesla leadership would be his profile on tesla[.]com—tesla[.]com/elon-musk. From Process #1 Step #2, we know what tesla[.]com’s WHOIS record details are (image on the right in procedure #4).
6. Note the differences between the current WHOIS records of the potential cybersquatter (image on the left) and Tesla’s official website domain tesla[.]com (image on the right). Focus most especially on the Registrant Email field.
Since elonmusk2x[.]org doesn’t have the same registrant email address as tesla[.]com, we can say that it can’t be publicly attributed to Elon Musk or Tesla. Translation? It most likely isn’t owned by Elon Musk or his company.
Process #3: Identifying Who Could Be Behind a Potential Fortune 500 Business Impersonation Scam
Starting from where we left off in Step #2 of Process #1, let’s further investigate who could be behind a campaign that used the malicious domain teslagives2023[.]com.
1. We already know from the domain’s current WHOIS record that it belongs to a private person from Russia.
2. You can also see his/her name, street address, email address, and phone and fax numbers on the DRS platform. For this demonstration, however, we redacted some of the information for privacy protection purposes.
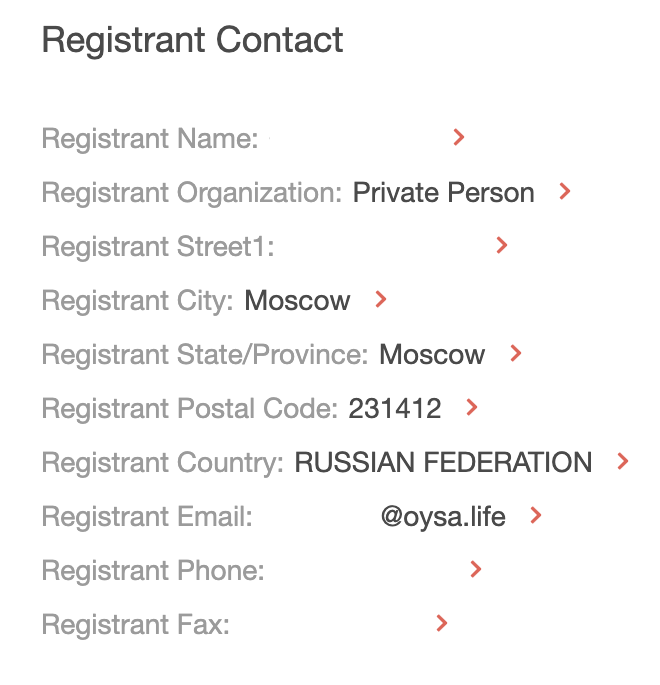
3. You can forward your findings to the authorities if you wish.
Domains and subdomains containing the names of Fortune 500 companies and their CEOs can readily be weaponized for BEC scams and whaling campaigns. In this DIY DRS investigation, we identified web properties related to business and CEO impersonation, which proved to be a huge threat in 2022 and continues to be so. The processes featured here can enable accelerated threat vector detection and help organizations avoid costly incidents.
Are you interested in doing similar fraud investigations? Access DRS if you are an existing user or sign up if you are a first-timer.








































