Integrating a Newly Registered Domains Database into Enterprise Cybersecurity Strategies

It’s generally agreed that newly registered domains are potential sources of threats. After all, many of these domain registrations are made opportunistically—sometimes even in bulk, following public announcements and global events. While not all of these domains have to be avoided at all costs, they certainly deserve more scrutiny than others that have been established for years.
The good news is that monitoring newly registered domains is doable with the help of the Newly Registered & Just Expired Domains Database.
Enterprise Cybersecurity Stakeholders: Who Can Benefit From a Newly Registered Domains Database Integration?
In this post, we explore how security platform developers, security operations centers (SOCs), and managed security service providers (MSSPs) can use a newly registered domains list to bolster their cybersecurity strategies.
1. Security Platform Developers
With statistics revealing that 70% of newly-registered domains are malicious, developers can deliver a lot of value to users by adding the monitoring of said domain names to their applications. Let’s take a look at an example.
Over the past few months, companies have been battling COVID-19-related phishing attacks, some of which rely on fake emails sent by impersonators of known healthcare organizations. When falling for the usual traps, victims either get redirected to a phishing website and lose their credentials to attackers or install malware that steals data from their computers.
What victims may not know is that most of the domains figuring in these phishing attacks are newly registered. To illustrate this point and how risky it can be to let them into corporate networks, we obtained a list of indicators of compromise (IoCs) related to COVID-19 attacks from the U.S. Department of Homeland Security.
The said IoC list contained close to 2,300 domains, which we subjected to a bulk WHOIS lookup.
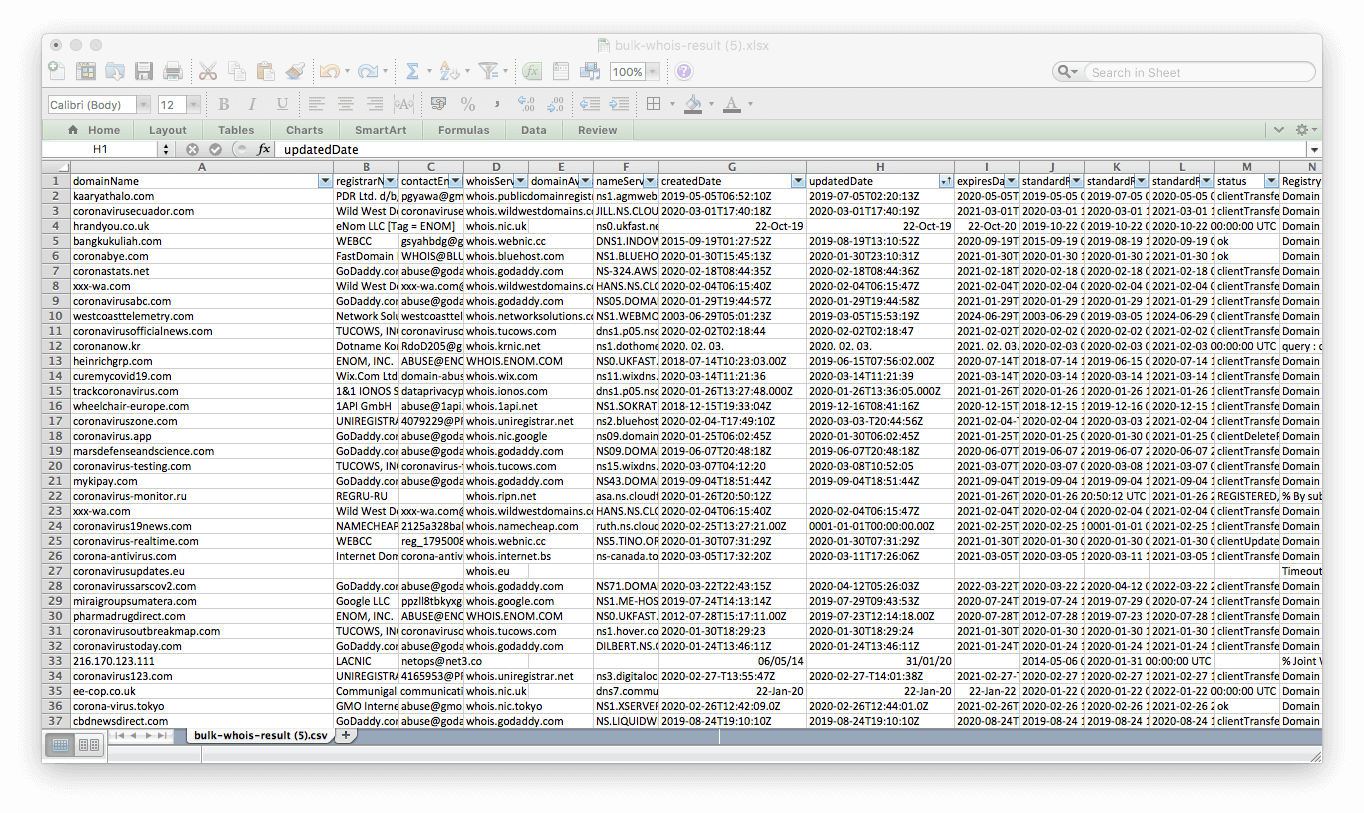
We found that around 98% of them were recently registered and therefore could have been detected by a security solution that incorporates a newly registered domains database. Some of the remaining 2% (54 out of 2,264) of the domains could have been freshly registered when they were possibly used in attacks.
What’s more, while the rise in new COVID-19 domain registrations may be utterly understandable as talks about the disease only surfaced late last year, the domains in the list claiming connections to institutions like the World Health Organization (WHO), for instance, are certainly deceitful. Established entities like WHO are more likely to house a COVID-19 page on their domain who[.]int rather than obtain a new one for it.
2. SOCs
One of the primary tasks of SOC staff is to dig deeper into ongoing attempts and attacks. It is their sworn duty to protect their organizations from all kinds of cyber threats.
Much like the phishing attacks we’ve seen a lot of these past few months, business email compromise (BEC) gangs are also ramping up their COVID-19-themed schemes. There has been an increase in the number of BEC scams targeting municipalities hoping to purchase personal protective equipment (PPE) and other related supplies to ward off the spread of the coronavirus.
One such group, dubbed “Ancient Tortoise,” became known for exploiting aging reports that finance teams use to track unpaid customer invoices. Researchers discovered that the actors behind Ancient Tortoise jumped onto the coronavirus-themed attacks bandwagon as well.
The Ancient Tortoise gang isn’t the only one hoping to lure companies and their customers or employees currently working from home into their traps, though. Another guise that BEC scammers employ is that of a legitimate co-worker providing a victim with the latest COVID-19 information. And much like phishers, BEC scammers are also fond of using newly registered domains that are copycats of popular suppliers’ legitimate domains.
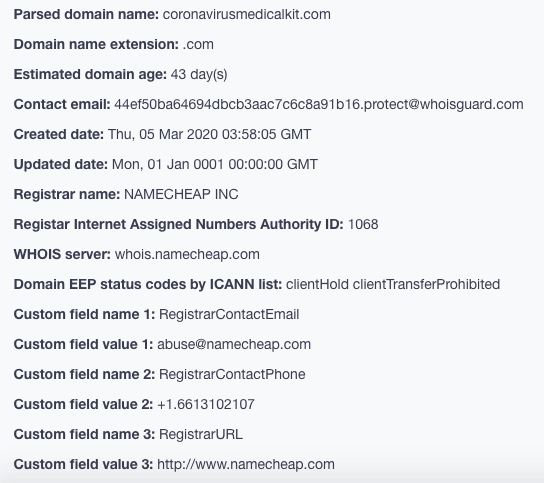
At the time of writing, all 25 IoCs related to this particular attack are newly registered domains and known malware hosts. Take a look at the Threat Intelligence Platform analysis results for coronavirusmedicalkit[.]com, beatingcoronavirus[.]com, and corona-crisis[.]com as examples.
All in all, SOC staff can get alerted and quickly block access to these by integrating a newly registered domains list into their security information and event management (SIEM) or security orchestration, automation, and response (SOAR) platforms.
3. MSSPs
Client protection should not only cover blocking known attack vectors but extend to preventing access to unknown threat sources, too. And these, of course, are likely to be newly registered domains that security solutions have yet to analyze and consequently block.
Take, for instance, a malicious domain connected to another COVID-19 related threat. Attackers preyed on user fear and anxiety to spread an information stealer via a fake coronavirus infection map. Apart from getting updates on the ensuing pandemic, however, users (who could be part of the organization an MSSP serves) also installed a malware application.
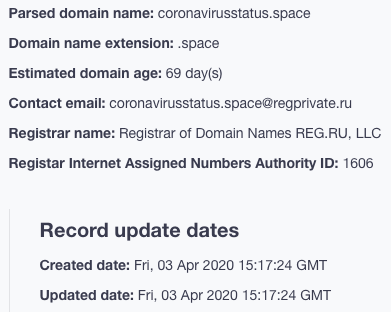
Much like in the other COVID-19-themed cases, the malware host’s domain—coronavirusstatus[.]space—is a recently registered domain.
Such a threat is, therefore, avoidable with the help of a newly registered domains database. But as was said, the buck doesn’t stop there for MSSPs. They should also be able to protect clients from the unknown. Apart from screening newly registered domains, they can use other domain and IP intelligence solutions.
MSSPs can, for instance, identify IP addresses and other domains connected to the known threat source via solutions like the Threat Intelligence Platform. They can then monitor and subsequently block access to related IP addresses and domains should the need arise. An example would be domains related to known malware host corona-explained[.]com. MSSPs can subject the domains on the same IP address to further scrutiny, too.
Threats That Organizations Can Avoid by Constantly Monitoring Their Newly Registered Domains List
Phishing, BEC, and malware attacks aren’t the only threats that Newly Registered & Just Expired Domains Database can help protect against. Others include:
- Spammers who are ramping up their campaigns with fake emails supposedly coming from institutions at the forefront of fighting the ensuing pandemic such as WHO and the Centers for Disease Control and Prevention (CDC).
- Typosquatters who are also bringing their A-game as evidenced by the proliferation of bulk coronavirus-themed domain registrations in the past few months alone.
As we demonstrated earlier, however, companies are not helpless. They can ensure their own or clients’ protection amid the ever-increasing volume of threats by adding newly-registered domain monitoring to their cybersecurity strategies.
How to Integrate a Newly Registered Domains Database into Existing Systems and Solutions
Security platform manufacturers, SOCs, and MSSPs can reap the benefits that the Newly Registered & Just Expired Domains Database provides by integrating it into existing solutions and systems. Just follow these steps:
- Log in to the Newly Registered & Just Expired Domains Database page with your WhoisXML API account credentials.
- Download the database by following the steps in this post. It comes in the form of a comma-separated values (CSV) file that can work with practically any solution or system. Here’s a sample file containing the additions to .us domains on 17 April.
- Hook the database up to your security solutions and processes as an information source.
---
Newly Registered & Just Expired Domains Database is a comprehensive source of information for organizations looking to avoid dangerous new entities circulating on the Internet. Integrating it into existing solutions and systems will allow security platform manufacturers, SOCs, and MSSPs to offer best-of-breed products and services to clients, whether internal (co-workers in the same organization) or external (third-party customers).





































